This put up is by Lizzie.
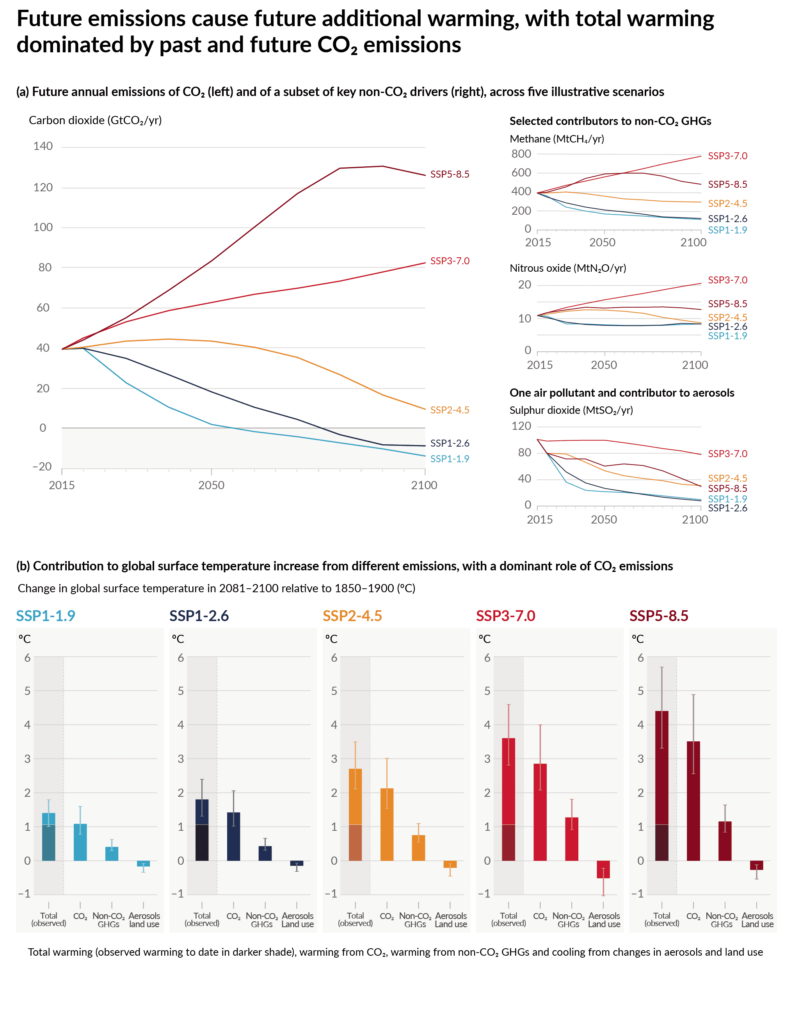
The Intergovernmental Panel on Local weather Change (IPCC) is a United Nations group that helps assemble the absolute best info on local weather change and its impacts, after which tries to speak it to the world. In 2017 they up to date their former fashions for emissions situations (consultant focus pathways, RCPs) to incorporate socioeconomic narratives and known as them Shared Socioeconomic Pathways (SSPs, oy! The acronyms).
One has been ringing in my head for some time now. And I’ve been which means to trace it down, particularly since some ‘who may have imagined this?’ conversations that I had months in the past. I’m lastly making the time now as I wrap up instructing local weather change ecology.
Right here’s the outline for SSP3 — Regional Rivalry – A Rocky Street:
A resurgent nationalism, considerations about competitiveness and safety, and regional conflicts push nations to more and more give attention to home or, at most, regional points. Insurance policies shift over time to turn into more and more oriented towards nationwide and regional safety points. Nations give attention to reaching vitality and meals safety objectives inside their very own areas on the expense of broader-based growth. Investments in schooling and technological growth decline. Financial growth is sluggish, consumption is material-intensive, and inequalities persist or worsen over time. Inhabitants development is low in industrialized and excessive in creating nations. A low worldwide precedence for addressing environmental considerations results in robust environmental degradation in some areas.
Reference right here and see additionally this.
There’s solely 5 narratives. Lacking from them is the prospect to alter which one we’re on; see additionally the Local weather Motion Tracker.