Endpoint Detection and Response focuses on monitoring and responding to threats on particular person gadgets like laptops and servers. Whereas, Community Detection and Response displays community site visitors to detect and reply to threats throughout the complete community infrastructure.
Fixed threats and vulnerabilities are everlasting companions within the IT panorama. Numerous safety options have emerged to guard perimeter, digital belongings. Because the cyber menace panorama could be very huge and complicated and requires specialised instruments and applied sciences to successfully deal with cyber threats and that are always evolving to scale back the menace panorama.
In as we speak’s article we perceive the distinction between endpoint detection and response (EDR) and Community detection and response (NDR) instruments and applied sciences, their key options, key variations and use instances.
What’s Endpoint Detection and Response (EDR)
Endpoint detection and response instruments give attention to endpoints because the title suggests. They work on endpoints similar to workstations, servers, mobiles, laptops and different cell belongings. They supply actual time monitoring, detection and blocking of threats with superior menace detection capabilities. It could actually establish malware and different malicious actions on gadgets and supply fast incident response. EDR options present menace searching, malicious exercise discovery and its containment to forestall incidents and cut back the assault floor.
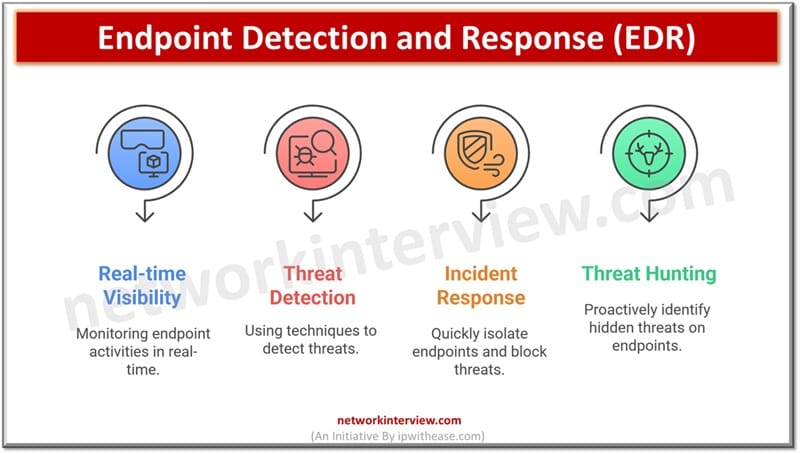
Options of EDR
- Actual time visibility into actions occurring on endpoints
- Big selection of menace detection strategies getting used similar to anomaly detection, heuristics and scans primarily based on menace signatures
- Fast incident response to isolate suspected endpoints , malicious content material blocking and menace remediation with minimal or no impression on operations
- Proactive menace searching is supported to establish hidden threats and potential vulnerabilities on endpoints
What’s Community Detection and Response (NDR)
Community detection and response or NDR because the title suggests focus is community perimeter / community site visitors. Steady monitoring of community site visitors is carried out to create a baseline for regular community behaviour patterns. When any sample exterior the baseline is detected then potential menace presence is recorded and notified. NDR instruments accumulate and analyze community knowledge utilizing machine studying strategies to detect potential threats. It detects uncommon site visitors primarily based on baseline derived by community analysts which could get missed out because of unknown or new signatures.
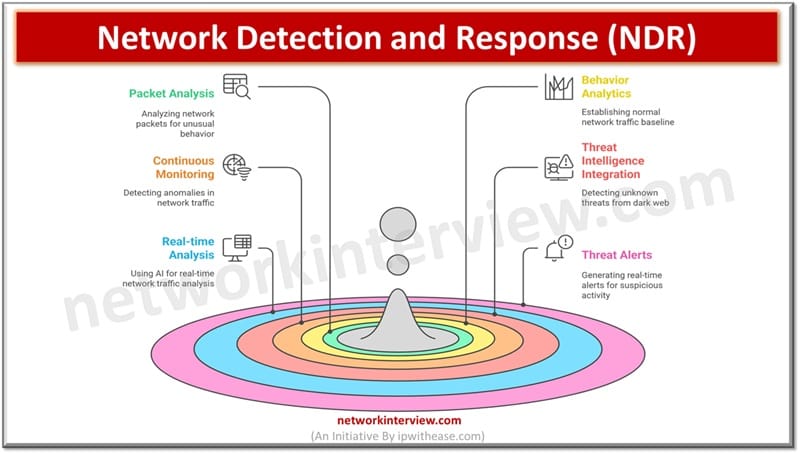
Options of NDR
- Capturing community packets and analyzing them for his or her content material for uncommon behaviour detection, menace identification with deep packet inspections
- Behaviour analytics to ascertain regular community site visitors baseline
- Steady monitoring of community site visitors for anomaly detection similar to uncommon excessive knowledge transfers, a number of login makes an attempt and suspected breach indicated with knowledge flows
- It’s built-in with menace intelligence feeds to detect unknown threats from darkish internet
- Community site visitors evaluation in actual time utilizing machine studying and AI algorithms
- On detection of suspicious exercise actual time menace alerts are generated
Comparability: EDR vs NDR
Beneath desk summarizes the variations between the 2:
Options |
EDR(Endpoint Detection and Response) |
NDR(Community Detection and Response) |
| Scope | Primarily meant for endpoints similar to workstations, laptops. Cellular gadgets and many others. | Primarily meant for networks |
| Operate | Risk detection and response for endpoints | Monitoring of community site visitors for detecting threats and anomalies |
| Options | • Knowledge assortment at endpoints repeatedly
• Risk detection and actual time alerting • Behaviour analytics and remediation (auto) • Integration with menace databases enrich the identification of menace panorama which permits recognition of malware, suspicious IP addresses and many others. |
• Deep packet inspections
• Anomaly detection and protocol decoding • Visitors evaluation and alert on threats • ML and AI primarily based insights assist in identification of recent menace actors |
| Use instances | • Perfect for organizations in search of granular safety and incident response dealing with capabilities on endpoints
• Meant for malware, ransomware and vulnerabilities detection |
• Visibility, menace detection and response capabilities for organizations specializing in community safety
• Meant for defense from insider menace, and lateral motion |
| Advantages | • Centered strategy in the direction of endpoint safety
• Risk detection and auto remediation |
• Centered strategy in the direction of community safety
• Actual time response and menace detection |
| Response mechanism | Isolation of compromised endpoints | Malicious community exercise blocking |
| Knowledge sources | Brokers deployed on endpoints have exercise logs | Community sensors deployed to investigate community site visitors |
| Identification and entry administration | Identification integration at fundamental stage supported | No direct involvement |
Obtain the comparability desk: Endpoint Detection and Response vs Community Detection and Response
Endpoint Detection and Response focuses on monitoring and responding to threats on particular person gadgets like laptops and servers. Whereas, Community Detection and Response displays community site visitors to detect and reply to threats throughout the complete community infrastructure.
Fixed threats and vulnerabilities are everlasting companions within the IT panorama. Numerous safety options have emerged to guard perimeter, digital belongings. Because the cyber menace panorama could be very huge and complicated and requires specialised instruments and applied sciences to successfully deal with cyber threats and that are always evolving to scale back the menace panorama.
In as we speak’s article we perceive the distinction between endpoint detection and response (EDR) and Community detection and response (NDR) instruments and applied sciences, their key options, key variations and use instances.
What’s Endpoint Detection and Response (EDR)
Endpoint detection and response instruments give attention to endpoints because the title suggests. They work on endpoints similar to workstations, servers, mobiles, laptops and different cell belongings. They supply actual time monitoring, detection and blocking of threats with superior menace detection capabilities. It could actually establish malware and different malicious actions on gadgets and supply fast incident response. EDR options present menace searching, malicious exercise discovery and its containment to forestall incidents and cut back the assault floor.

Options of EDR
- Actual time visibility into actions occurring on endpoints
- Big selection of menace detection strategies getting used similar to anomaly detection, heuristics and scans primarily based on menace signatures
- Fast incident response to isolate suspected endpoints , malicious content material blocking and menace remediation with minimal or no impression on operations
- Proactive menace searching is supported to establish hidden threats and potential vulnerabilities on endpoints
What’s Community Detection and Response (NDR)
Community detection and response or NDR because the title suggests focus is community perimeter / community site visitors. Steady monitoring of community site visitors is carried out to create a baseline for regular community behaviour patterns. When any sample exterior the baseline is detected then potential menace presence is recorded and notified. NDR instruments accumulate and analyze community knowledge utilizing machine studying strategies to detect potential threats. It detects uncommon site visitors primarily based on baseline derived by community analysts which could get missed out because of unknown or new signatures.

Options of NDR
- Capturing community packets and analyzing them for his or her content material for uncommon behaviour detection, menace identification with deep packet inspections
- Behaviour analytics to ascertain regular community site visitors baseline
- Steady monitoring of community site visitors for anomaly detection similar to uncommon excessive knowledge transfers, a number of login makes an attempt and suspected breach indicated with knowledge flows
- It’s built-in with menace intelligence feeds to detect unknown threats from darkish internet
- Community site visitors evaluation in actual time utilizing machine studying and AI algorithms
- On detection of suspicious exercise actual time menace alerts are generated
Comparability: EDR vs NDR
Beneath desk summarizes the variations between the 2:
Options |
EDR(Endpoint Detection and Response) |
NDR(Community Detection and Response) |
| Scope | Primarily meant for endpoints similar to workstations, laptops. Cellular gadgets and many others. | Primarily meant for networks |
| Operate | Risk detection and response for endpoints | Monitoring of community site visitors for detecting threats and anomalies |
| Options | • Knowledge assortment at endpoints repeatedly
• Risk detection and actual time alerting • Behaviour analytics and remediation (auto) • Integration with menace databases enrich the identification of menace panorama which permits recognition of malware, suspicious IP addresses and many others. |
• Deep packet inspections
• Anomaly detection and protocol decoding • Visitors evaluation and alert on threats • ML and AI primarily based insights assist in identification of recent menace actors |
| Use instances | • Perfect for organizations in search of granular safety and incident response dealing with capabilities on endpoints
• Meant for malware, ransomware and vulnerabilities detection |
• Visibility, menace detection and response capabilities for organizations specializing in community safety
• Meant for defense from insider menace, and lateral motion |
| Advantages | • Centered strategy in the direction of endpoint safety
• Risk detection and auto remediation |
• Centered strategy in the direction of community safety
• Actual time response and menace detection |
| Response mechanism | Isolation of compromised endpoints | Malicious community exercise blocking |
| Knowledge sources | Brokers deployed on endpoints have exercise logs | Community sensors deployed to investigate community site visitors |
| Identification and entry administration | Identification integration at fundamental stage supported | No direct involvement |
Obtain the comparability desk: Endpoint Detection and Response vs Community Detection and Response
