
Picture: Shutterstock, ArtHead.
The U.S. authorities at the moment imposed financial sanctions on Funnull Know-how Inc., a Philippines-based firm that gives laptop infrastructure for a whole lot of 1000’s of internet sites concerned in digital forex funding scams referred to as “pig butchering.” In January 2025, KrebsOnSecurity detailed how Funnull was getting used as a content material supply community that catered to cybercriminals searching for to route their visitors by way of U.S.-based cloud suppliers.
“Individuals lose billions of {dollars} yearly to those cyber scams, with revenues generated from these crimes rising to document ranges in 2024,” reads an announcement from the U.S. Division of the Treasury, which sanctioned Funnull and its 40-year-old Chinese language administrator Liu Lizhi. “Funnull has straight facilitated a number of of those schemes, leading to over $200 million in U.S. victim-reported losses.”
The Treasury Division mentioned Funnull’s operations are linked to nearly all of digital forex funding rip-off web sites reported to the FBI. The company mentioned Funnull straight facilitated pig butchering and different schemes that resulted in additional than $200 million in monetary losses by Individuals.
Pig butchering is a rampant type of fraud whereby persons are lured by flirtatious strangers on-line into investing in fraudulent cryptocurrency buying and selling platforms. Victims are coached to take a position an increasing number of cash into what seems to be an especially worthwhile buying and selling platform, solely to seek out their cash is gone after they want to money out.
The scammers usually insist that traders pay extra “taxes” on their crypto “earnings” earlier than they will see their invested funds once more (spoiler: they by no means do), and a stunning variety of individuals have misplaced six figures or extra by way of these pig butchering scams.
KrebsOnSecurity’s January story on Funnull was primarily based on analysis from the safety agency Silent Push, which found in October 2024 {that a} huge variety of domains hosted through Funnull have been selling playing websites that bore the emblem of the Suncity Group, a Chinese language entity named in a 2024 UN report (PDF) for laundering hundreds of thousands of {dollars} for the North Korean state-sponsored hacking group Lazarus.
Silent Push discovered Funnull was a legal content material supply community (CDN) that carried an excessive amount of visitors tied to rip-off web sites, funneling the visitors by way of a dizzying chain of auto-generated domains and U.S.-based cloud suppliers earlier than redirecting to malicious or phishous web sites. The FBI has launched a technical writeup (PDF) of the infrastructure used to handle the malicious Funnull domains between October 2023 and April 2025.
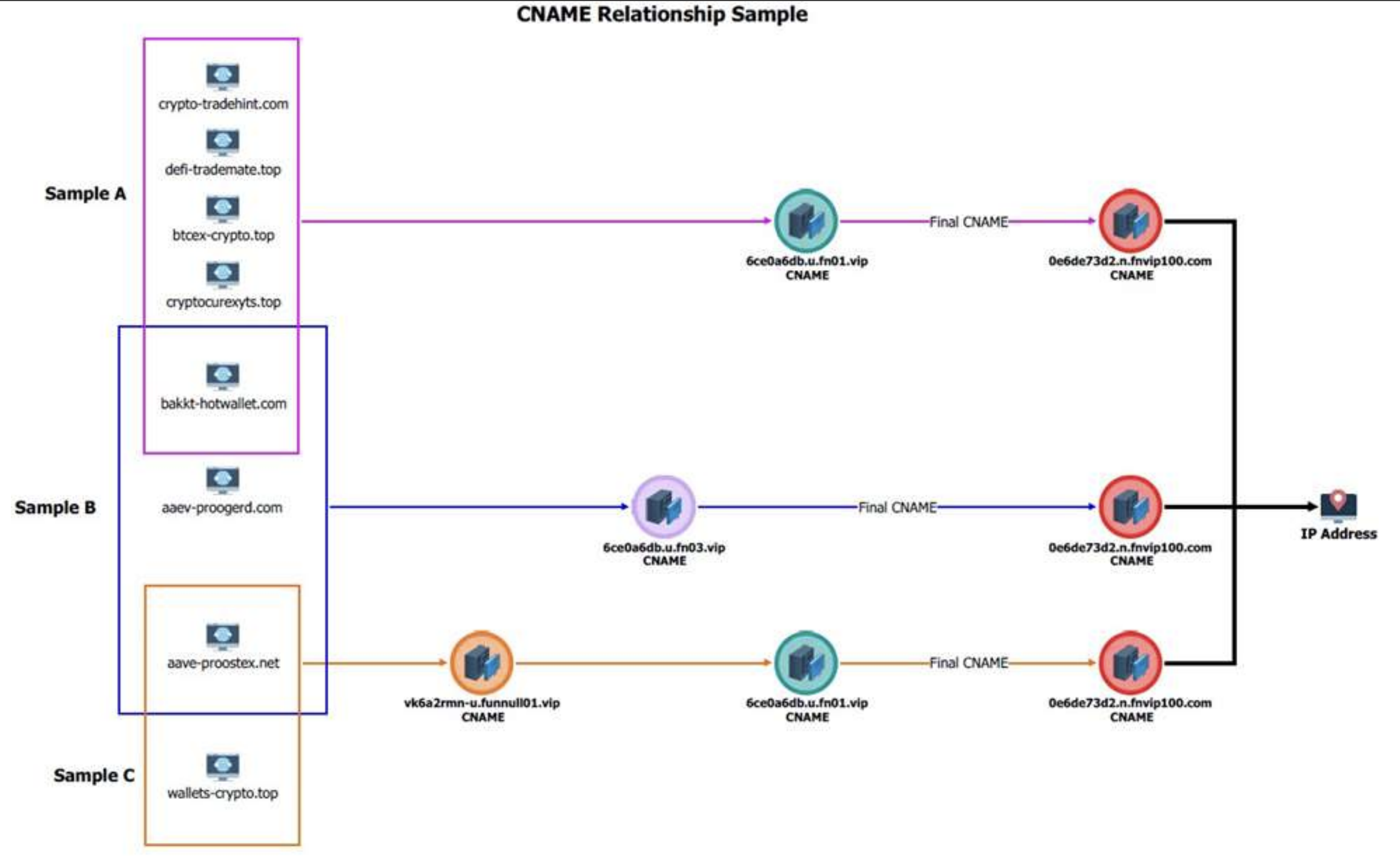
A graphic from the FBI explaining how Funnull generated a slew of latest domains frequently and mapped them to Web addresses on U.S. cloud suppliers.
Silent Push revisited Funnull’s infrastructure in January 2025 and located Funnull was nonetheless utilizing most of the identical Amazon and Microsoft cloud Web addresses recognized as malicious in its October report. Each Amazon and Microsoft pledged to rid their networks of Funnull’s presence following that story, however based on Silent Push’s Zach Edwards solely a type of firms has adopted by way of.
Edwards mentioned Silent Push now not sees Microsoft Web addresses exhibiting up in Funnull’s infrastructure, whereas Amazon continues to battle with eradicating Funnull servers, together with one which seems to have first materialized in 2023.
“Amazon is doing a horrible job — on daily basis since they made these claims to you and us in our public weblog they’ve had IPs nonetheless mapped to Funnull, together with some which have stayed mapped for inexplicable intervals of time,” Edwards mentioned.
Amazon mentioned its Amazon Net Companies (AWS) internet hosting platform actively counters abuse makes an attempt.
“We have now stopped a whole lot of makes an attempt this 12 months associated to this group and we’re trying into the data you shared earlier at the moment,” reads an announcement shared by Amazon. “If anybody suspects that AWS sources are getting used for abusive exercise, they will report it to AWS Belief & Security utilizing the report abuse type right here.”
U.S. primarily based cloud suppliers stay a pretty residence base for cybercriminal organizations as a result of many organizations won’t be overly aggressive in blocking visitors from U.S.-based cloud networks, as doing so may end up in blocking entry to many official net locations which are additionally on that very same shared community section or host.
What’s extra, funneling their unhealthy visitors in order that it seems to be popping out of U.S. cloud Web suppliers permits cybercriminals to connect with web sites from net addresses which are geographically shut(r) to their targets and victims (to sidestep location-based safety controls by your financial institution, for instance).
Funnull isn’t the one cybercriminal infrastructure-as-a-service supplier that was sanctioned this month: On Could 20, 2025, the European Union imposed sanctions on Stark Industries Options, an ISP that materialized in the beginning of Russia’s invasion of Ukraine and has been used as a world proxy community that conceals the true supply of cyberattacks and disinformation campaigns towards enemies of Russia.
In Could 2024, KrebsOnSecurity printed a deep dive on Stark Industries Options that discovered a lot of the malicious visitors traversing Stark’s community (e.g. vulnerability scanning and password brute pressure assaults) was being bounced by way of U.S.-based cloud suppliers. My reporting confirmed how deeply Stark had penetrated U.S. ISPs, and that Ivan Neculiti for a few years bought “bulletproof” internet hosting companies that advised Russian cybercrime discussion board prospects they’d proudly ignore any abuse complaints or police inquiries.
The homepage of Stark Industries Options.
That story examined the historical past of Stark’s co-founders, Moldovan brothers Ivan and Yuri Neculiti, who every denied previous involvement in cybercrime or any present involvement in aiding Russian disinformation efforts or cyberattacks. However, the EU sanctioned each brothers as effectively.
The EU mentioned Stark and the Neculti brothers “enabled varied Russian state-sponsored and state-affiliated actors to conduct destabilising actions together with coordinated info manipulation and interference and cyber-attacks towards the Union and third international locations by offering companies supposed to cover these actions from European regulation enforcement and safety businesses.”

Picture: Shutterstock, ArtHead.
The U.S. authorities at the moment imposed financial sanctions on Funnull Know-how Inc., a Philippines-based firm that gives laptop infrastructure for a whole lot of 1000’s of internet sites concerned in digital forex funding scams referred to as “pig butchering.” In January 2025, KrebsOnSecurity detailed how Funnull was getting used as a content material supply community that catered to cybercriminals searching for to route their visitors by way of U.S.-based cloud suppliers.
“Individuals lose billions of {dollars} yearly to those cyber scams, with revenues generated from these crimes rising to document ranges in 2024,” reads an announcement from the U.S. Division of the Treasury, which sanctioned Funnull and its 40-year-old Chinese language administrator Liu Lizhi. “Funnull has straight facilitated a number of of those schemes, leading to over $200 million in U.S. victim-reported losses.”
The Treasury Division mentioned Funnull’s operations are linked to nearly all of digital forex funding rip-off web sites reported to the FBI. The company mentioned Funnull straight facilitated pig butchering and different schemes that resulted in additional than $200 million in monetary losses by Individuals.
Pig butchering is a rampant type of fraud whereby persons are lured by flirtatious strangers on-line into investing in fraudulent cryptocurrency buying and selling platforms. Victims are coached to take a position an increasing number of cash into what seems to be an especially worthwhile buying and selling platform, solely to seek out their cash is gone after they want to money out.
The scammers usually insist that traders pay extra “taxes” on their crypto “earnings” earlier than they will see their invested funds once more (spoiler: they by no means do), and a stunning variety of individuals have misplaced six figures or extra by way of these pig butchering scams.
KrebsOnSecurity’s January story on Funnull was primarily based on analysis from the safety agency Silent Push, which found in October 2024 {that a} huge variety of domains hosted through Funnull have been selling playing websites that bore the emblem of the Suncity Group, a Chinese language entity named in a 2024 UN report (PDF) for laundering hundreds of thousands of {dollars} for the North Korean state-sponsored hacking group Lazarus.
Silent Push discovered Funnull was a legal content material supply community (CDN) that carried an excessive amount of visitors tied to rip-off web sites, funneling the visitors by way of a dizzying chain of auto-generated domains and U.S.-based cloud suppliers earlier than redirecting to malicious or phishous web sites. The FBI has launched a technical writeup (PDF) of the infrastructure used to handle the malicious Funnull domains between October 2023 and April 2025.

A graphic from the FBI explaining how Funnull generated a slew of latest domains frequently and mapped them to Web addresses on U.S. cloud suppliers.
Silent Push revisited Funnull’s infrastructure in January 2025 and located Funnull was nonetheless utilizing most of the identical Amazon and Microsoft cloud Web addresses recognized as malicious in its October report. Each Amazon and Microsoft pledged to rid their networks of Funnull’s presence following that story, however based on Silent Push’s Zach Edwards solely a type of firms has adopted by way of.
Edwards mentioned Silent Push now not sees Microsoft Web addresses exhibiting up in Funnull’s infrastructure, whereas Amazon continues to battle with eradicating Funnull servers, together with one which seems to have first materialized in 2023.
“Amazon is doing a horrible job — on daily basis since they made these claims to you and us in our public weblog they’ve had IPs nonetheless mapped to Funnull, together with some which have stayed mapped for inexplicable intervals of time,” Edwards mentioned.
Amazon mentioned its Amazon Net Companies (AWS) internet hosting platform actively counters abuse makes an attempt.
“We have now stopped a whole lot of makes an attempt this 12 months associated to this group and we’re trying into the data you shared earlier at the moment,” reads an announcement shared by Amazon. “If anybody suspects that AWS sources are getting used for abusive exercise, they will report it to AWS Belief & Security utilizing the report abuse type right here.”
U.S. primarily based cloud suppliers stay a pretty residence base for cybercriminal organizations as a result of many organizations won’t be overly aggressive in blocking visitors from U.S.-based cloud networks, as doing so may end up in blocking entry to many official net locations which are additionally on that very same shared community section or host.
What’s extra, funneling their unhealthy visitors in order that it seems to be popping out of U.S. cloud Web suppliers permits cybercriminals to connect with web sites from net addresses which are geographically shut(r) to their targets and victims (to sidestep location-based safety controls by your financial institution, for instance).
Funnull isn’t the one cybercriminal infrastructure-as-a-service supplier that was sanctioned this month: On Could 20, 2025, the European Union imposed sanctions on Stark Industries Options, an ISP that materialized in the beginning of Russia’s invasion of Ukraine and has been used as a world proxy community that conceals the true supply of cyberattacks and disinformation campaigns towards enemies of Russia.
In Could 2024, KrebsOnSecurity printed a deep dive on Stark Industries Options that discovered a lot of the malicious visitors traversing Stark’s community (e.g. vulnerability scanning and password brute pressure assaults) was being bounced by way of U.S.-based cloud suppliers. My reporting confirmed how deeply Stark had penetrated U.S. ISPs, and that Ivan Neculiti for a few years bought “bulletproof” internet hosting companies that advised Russian cybercrime discussion board prospects they’d proudly ignore any abuse complaints or police inquiries.

The homepage of Stark Industries Options.
That story examined the historical past of Stark’s co-founders, Moldovan brothers Ivan and Yuri Neculiti, who every denied previous involvement in cybercrime or any present involvement in aiding Russian disinformation efforts or cyberattacks. However, the EU sanctioned each brothers as effectively.
The EU mentioned Stark and the Neculti brothers “enabled varied Russian state-sponsored and state-affiliated actors to conduct destabilising actions together with coordinated info manipulation and interference and cyber-attacks towards the Union and third international locations by offering companies supposed to cover these actions from European regulation enforcement and safety businesses.”





