How To
Have you ever ever googled your self? Had been you pleased with what got here up? If not, contemplate requesting the elimination of your private info from search outcomes.
30 Oct 2024
•
,
4 min. learn

In at the moment’s digital age, sustaining management over your private info is extra essential than ever. Whether or not you’re involved about privateness, safety, or just need to handle your on-line presence, realizing easy methods to scale back your visibility in search outcomes is usually a worthwhile talent.
So, let’s have a look at why it’s possible you’ll need to scale back your digital footprint, together with in Google Search, and how one can defend your knowledge from prying eyes.
What exhibits up in Google Search?
Let’s begin with an train to know how your identify and different info seem on-line and to establish any potential privateness considerations:
Seek for your individual identify on Google (ideally in citation marks, utilizing an online browser’s incognito mode, and with out being logged into your Google account) and see what turns up. Normally, it’s your social media account, weblog, or work-related web site.
Now refine your search with an extra parameter, like an oft-visited web site, or possibly your avenue’s identify. Unsurprisingly, the search outcomes grow to be extra particular, showcasing how highly effective engines like google are at pinpointing somebody’s knowledge.
When you have a social media account with weak privateness settings, run a weblog below your actual identify, or checklist your e mail tackle on an organization web site, these particulars may be simply compiled to construct an in depth image of your digital identification, typically full together with your pursuits, habits and affiliations. Nevertheless, this aggregation of knowledge is usually a drawback for a number of causes.
The risks of social engineering
In response to the 2024 Verizon Information Breach Investigations Report, as a lot as 68% of knowledge breaches occurred because of human error. Of this, a big proportion resulted from individuals falling for social engineering ways resembling phishing, pretexting, e mail scams, and extortion.
Pretexting is a kind of social engineering assault whereby an attacker creates a pretext (story) with a view to finally steal a sufferer’s cash or knowledge.
Ne’er-do-wells can exploit this wealth of publicly obtainable info utilizing social engineering ways. These schemes purpose to trick individuals into sending cash or revealing delicate knowledge, resembling account credentials.
A subset of Enterprise E-mail Compromise (BEC), CEO fraud entails crooks impersonating an organization govt and deceiving workers, usually in finance or accounting, into transferring funds or divulging delicate company info.
Managing your knowledge in Google Search
Think about all the information you discovered throughout our train – and consider it within the context of the above-mentioned scams.
Fortunately, Google took discover of individuals’s grievances about their typically being only a search away and created a number of varieties to assist customers take away their info. What’s extra, Google additionally offers a instrument, “Outcomes about you”, that permits you to observe your knowledge on-line and see whether or not knowledge factors like your house tackle, telephone quantity or e mail tackle present up in search outcomes.
Tips on how to use Google’s “Outcomes about you”
To make use of this function, it’s essential to have a Google account. You possibly can entry it via a browser in your pc or by way of the Google app in your telephone.
For the browser model, comply with these steps:
- Log into your Google account and click on in your profile avatar.
- Within the menu, click on on “Handle your Google Account” after which “Information and Privateness”.
- Within the Historical past settings click on on “My exercise” after which “Different exercise”.
- Scroll till you discover “Outcomes about you” and click on on “Handle outcomes about you”.
Whereas on the web page, choose “Get Began” or “Settings”. You’ll be prompted to enter the data they wish to discover, resembling nicknames, telephone numbers, or addresses. You may also arrange notifications to warn you if Google finds outcomes related together with your contact info.
On cellular units, merely click on in your Google Account’s profile avatar within the Google App and there must be an possibility titled “Outcomes about you” within the preliminary menu.
The search takes some time to finish, however you’ll obtain a notification as quickly because the question is completed. If the outcomes are to not your liking, you’ll be able to request elimination via the designated possibility.
Do word that “Outcomes about you” will not be obtainable in all areas/nations, however extra are being added as we go alongside.
Request the elimination of search outcomes
An alternative choice is to submit a direct request to Google to evaluation and take away search outcomes that fulfill specific standards – resembling publicity of your e mail or house tackle, login credentials, or different private particulars.
It’s somewhat straightforward – simply begin a elimination request by filling out the required type (pictured beneath and obtainable right here).
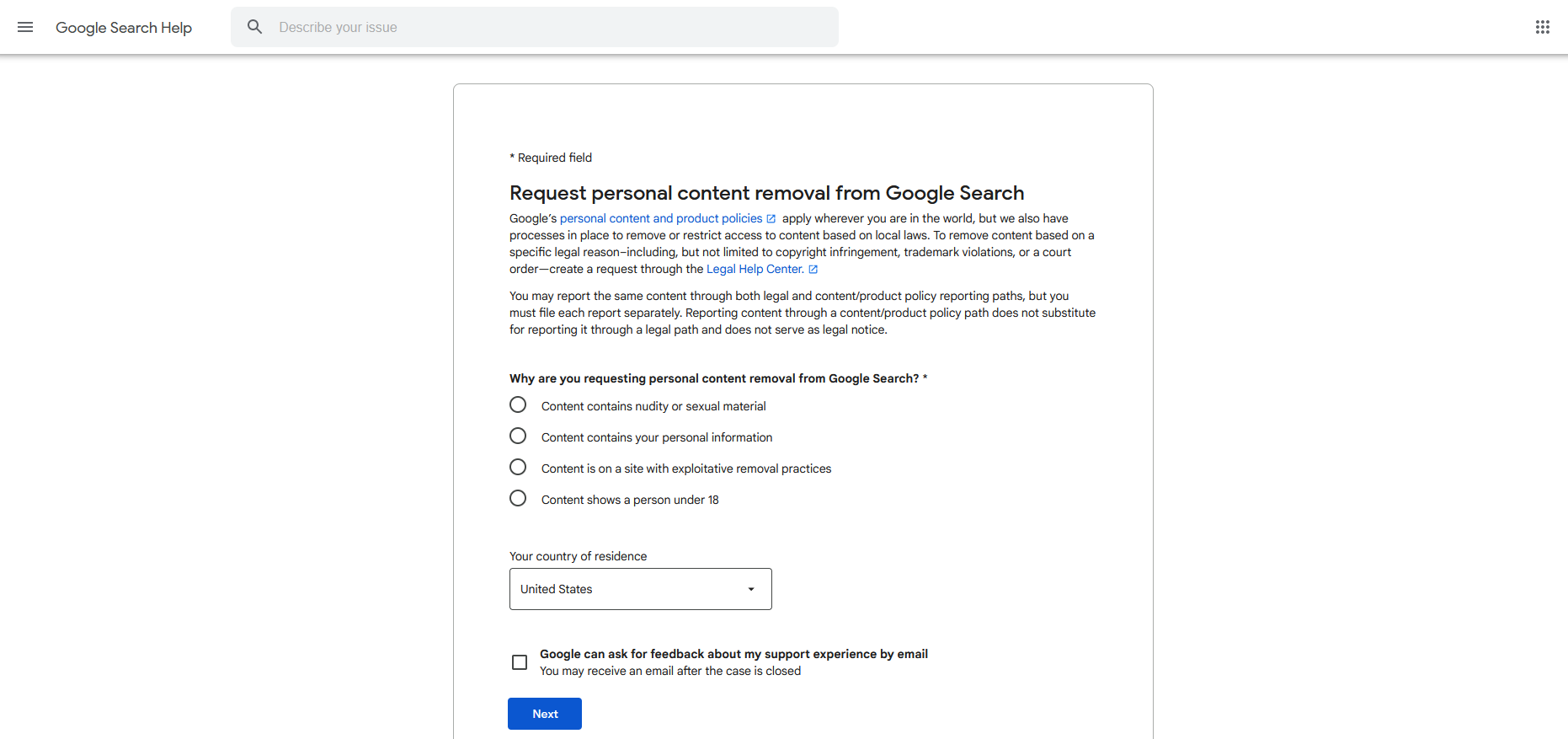

If the difficulty isn’t clear-cut or Google requires extra info to pinpoint the issue, you’ll obtain an e mail asking for additional clarification.
Cybersecurity, privateness, and a scam-free life
Some individuals could also be snug with having their public knowledge obtainable on-line, however privacy-minded residents may not. Even well-known public figures and organizations ought to hold sure knowledge confidential to keep away from privateness and safety dangers.
Likewise, by limiting your on-line presence, you’ll be able to extra simply lead a privacy-conscious life. In the long run, it boils right down to understanding what details about you is on the market and to staying vigilant in order that malicious actors received’t catch you off-guard.








