To configure IPS on a FortiGate firewall, allow an IPS sensor within the related safety coverage. Then, apply or customise the sensor below Safety Profiles > Intrusion Prevention.
Intrusion prevention techniques or IPS present safety for the networks and hosts inside a community. They’ll detect and block network-based assaults. IPS sensors will be enabled based mostly on IPS signatures, IPS patterns and IPS filters. Many service suppliers present separate {hardware} or software program for IPS performance. Nonetheless, sure high-end firewall suppliers bundle IPS functionality into their firewall field itself which is definitely a whole menace administration answer in itself.
In at the moment’s subject we are going to study learn how to configure Intrusion prevention (IPS) on a FortiGate firewall.
What’s FortiGate Firewall IPS
FortiGate intrusion prevention is designed to offer actual time menace safety for networks. It leverages signature-based behaviour and anomaly-based detection strategies to detect and forestall safety threats. FortiGate applies intrusion prevention utilizing a wide range of operational modes. All three modes have their very own advantages and limitations, which one to decide on relies on the location.
- L3 (NAT/route mode): On this mode FortiGate locations an L3 community the place visitors is routed. IP addresses are configured statistically or dynamically on every interface. MAC based mostly insurance policies are relevant for IPS coverage supply tackle in NAT route mode.
- Digital wire mode: On this mode it’s deployed between two community segments. It operates like a digital wire and doesn’t carry out routing or NAT.
- Clear mode: On this mode it acts like a bridge. All interfaces in the identical VDOM are in the identical L2 forwarding area.
Configuring IPS on FortiGate Firewall
To configure IPS on FortiGate firewall
Step 1
Select endpoint coverage🡪 Infranet Enforcer
Step 2
Click on on New Infranet Enforcer and choose FortiGate firewall in platform from drop down
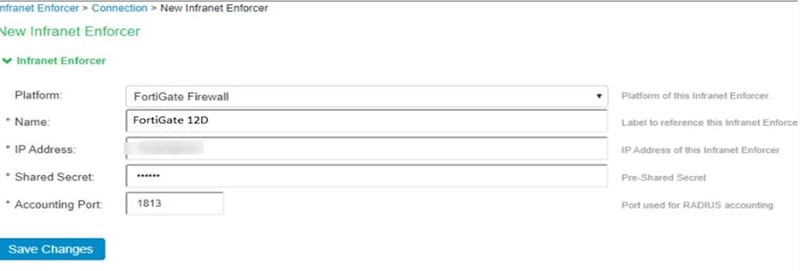
Enter FortiGate firewall IP tackle
Enter shared secret
Enter port quantity
Step 3
Click on on Save modifications and create insurance policies on FortiGate firewall for enforcement of visitors
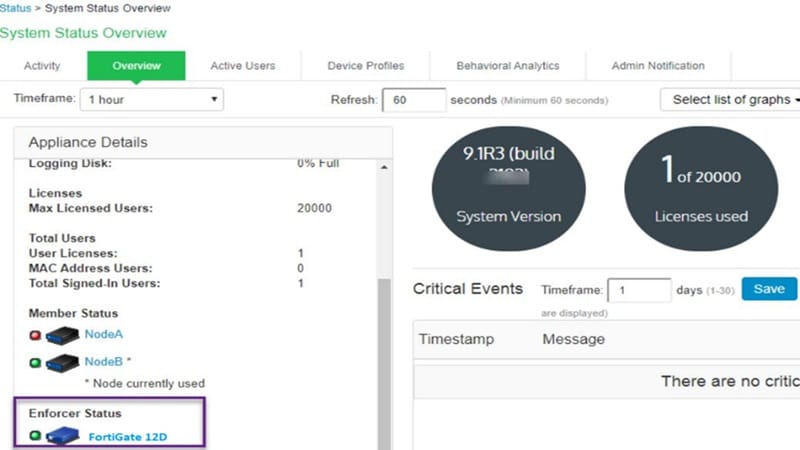
FortiGate has IPS sensors that are collections of IPS signatures and filters which outline what IPS engine will scan when the sensor is utilized. An IPS sensor may have a number of signatures or filters. Customized IPS signatures will also be created to use to an IPS sensor.
Step 4
From Safety profiles 🡪 Intrusion prevention pane – create new sensor and likewise view listing of predefined sensors. FortiOS has a predefined listing of sensors having related signatures.
| IPS sensors | Description |
| all_default | To filter all predefined signatures, setting motion to the signature’s default motion. |
| all_default_pass | To filter all predefined signatures, and set motion to watch / move |
| default | To filters all predefined signatures having Crucial/Excessive/Medium severity and set
motion to signature’s default motion. |
| high_security | To filters all predefined signatures having Crucial/Excessive/Medium severity and set
Motion as block. Low severity signatures motion set to default motion. |
| protect_client | To filter on Goal=Consumer for cover from client-side vulnerabilities by setting motion as default motion |
| protect_email_server | To filter on track = sever and protocol = IMAP, POP3 or SMTP for cover from e mail server-side vulnerabilities Units motion to signature’s default motion. |
| protect_http_server | To filter on Goal=Server and Protocol=HTTP for cover from HTTP server-side vulnerabilities. Units motion to signature’s default motion. |
| wifi-default | To filter all predefined signatures having Crucial/Excessive/Medium severity. Units motion default motion. Meant for offloading Wi-Fi visitors. |
IPS engine doesn’t look at community visitors by default for all signatures. It examines community visitors for signatures talked about in IPS sensors. It is advisable create an IPS sensor and specify which IPS signature it’s going to use.
Step 5
To view IPS sensors go to safety profiles🡪 intrusion prevention and to create new sensor click on on ‘New’
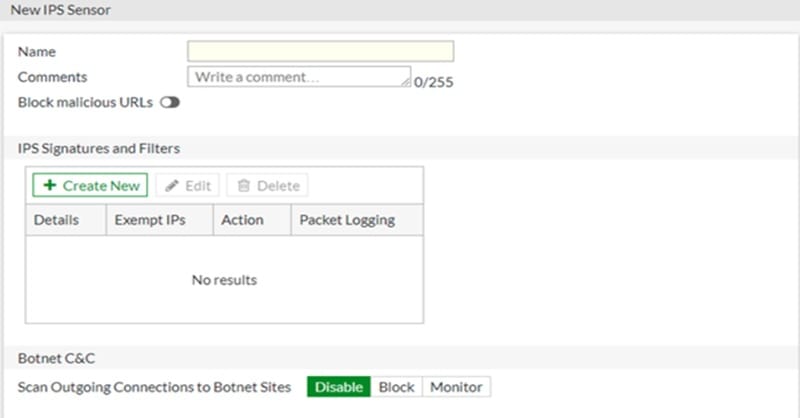
Step 6
Underneath IPS signatures and filters, click on create new to create a set of IPS signatures or set of IPS filters.
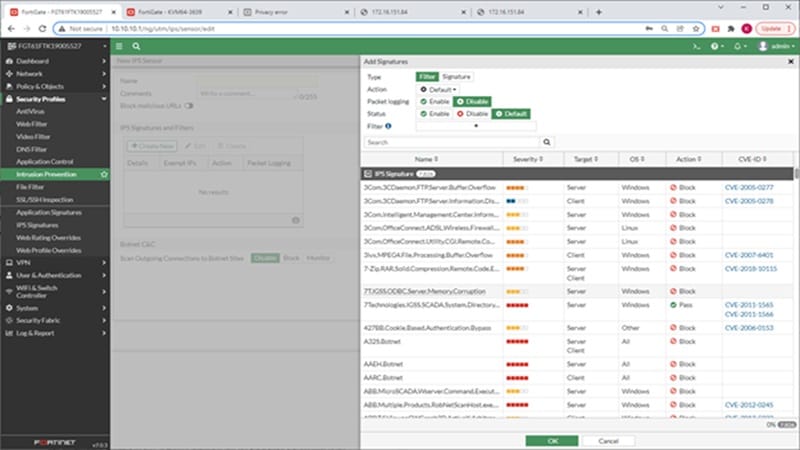
IPS sensors will be created for particular sorts of visitors. FortiGuard periodically provides predefined signatures to replace and counter new threats. These are included routinely in IPS sensors that are configured to make use of filters when new signatures match with specs of filters.
To configure IPS on a FortiGate firewall, allow an IPS sensor within the related safety coverage. Then, apply or customise the sensor below Safety Profiles > Intrusion Prevention.
Intrusion prevention techniques or IPS present safety for the networks and hosts inside a community. They’ll detect and block network-based assaults. IPS sensors will be enabled based mostly on IPS signatures, IPS patterns and IPS filters. Many service suppliers present separate {hardware} or software program for IPS performance. Nonetheless, sure high-end firewall suppliers bundle IPS functionality into their firewall field itself which is definitely a whole menace administration answer in itself.
In at the moment’s subject we are going to study learn how to configure Intrusion prevention (IPS) on a FortiGate firewall.
What’s FortiGate Firewall IPS
FortiGate intrusion prevention is designed to offer actual time menace safety for networks. It leverages signature-based behaviour and anomaly-based detection strategies to detect and forestall safety threats. FortiGate applies intrusion prevention utilizing a wide range of operational modes. All three modes have their very own advantages and limitations, which one to decide on relies on the location.
- L3 (NAT/route mode): On this mode FortiGate locations an L3 community the place visitors is routed. IP addresses are configured statistically or dynamically on every interface. MAC based mostly insurance policies are relevant for IPS coverage supply tackle in NAT route mode.
- Digital wire mode: On this mode it’s deployed between two community segments. It operates like a digital wire and doesn’t carry out routing or NAT.
- Clear mode: On this mode it acts like a bridge. All interfaces in the identical VDOM are in the identical L2 forwarding area.
Configuring IPS on FortiGate Firewall
To configure IPS on FortiGate firewall
Step 1
Select endpoint coverage🡪 Infranet Enforcer
Step 2
Click on on New Infranet Enforcer and choose FortiGate firewall in platform from drop down
 Present identify of Intranet Enforcer: ‘FortiGate 12D’
Present identify of Intranet Enforcer: ‘FortiGate 12D’
Enter FortiGate firewall IP tackle
Enter shared secret
Enter port quantity
Step 3
Click on on Save modifications and create insurance policies on FortiGate firewall for enforcement of visitors

FortiGate has IPS sensors that are collections of IPS signatures and filters which outline what IPS engine will scan when the sensor is utilized. An IPS sensor may have a number of signatures or filters. Customized IPS signatures will also be created to use to an IPS sensor.
Step 4
From Safety profiles 🡪 Intrusion prevention pane – create new sensor and likewise view listing of predefined sensors. FortiOS has a predefined listing of sensors having related signatures.
| IPS sensors | Description |
| all_default | To filter all predefined signatures, setting motion to the signature’s default motion. |
| all_default_pass | To filter all predefined signatures, and set motion to watch / move |
| default | To filters all predefined signatures having Crucial/Excessive/Medium severity and set
motion to signature’s default motion. |
| high_security | To filters all predefined signatures having Crucial/Excessive/Medium severity and set
Motion as block. Low severity signatures motion set to default motion. |
| protect_client | To filter on Goal=Consumer for cover from client-side vulnerabilities by setting motion as default motion |
| protect_email_server | To filter on track = sever and protocol = IMAP, POP3 or SMTP for cover from e mail server-side vulnerabilities Units motion to signature’s default motion. |
| protect_http_server | To filter on Goal=Server and Protocol=HTTP for cover from HTTP server-side vulnerabilities. Units motion to signature’s default motion. |
| wifi-default | To filter all predefined signatures having Crucial/Excessive/Medium severity. Units motion default motion. Meant for offloading Wi-Fi visitors. |
IPS engine doesn’t look at community visitors by default for all signatures. It examines community visitors for signatures talked about in IPS sensors. It is advisable create an IPS sensor and specify which IPS signature it’s going to use.
Step 5
To view IPS sensors go to safety profiles🡪 intrusion prevention and to create new sensor click on on ‘New’

Step 6
Underneath IPS signatures and filters, click on create new to create a set of IPS signatures or set of IPS filters.

IPS sensors will be created for particular sorts of visitors. FortiGuard periodically provides predefined signatures to replace and counter new threats. These are included routinely in IPS sensors that are configured to make use of filters when new signatures match with specs of filters.



