As already mentioned, footprinting is the primary part of hacking, wherein the attacker positive aspects major details about a possible goal. He/she then makes use of this data within the scanning part to assemble extra particulars in regards to the goal.
Scanning is the method of gathering further detailed details about the goal utilizing extremely advanced and aggressive reconnaissance methods. Community scanning refers to a set of procedures used for figuring out hosts, ports, and companies in a community. Community scanning can be used for locating lively machines in a community and figuring out the OS operating on the goal machine. It is among the most vital phases of knowledge gathering for an attacker, which permits him/her to create a profile of the goal group. Within the technique of scanning, the attacker tries to assemble data, together with the particular IP addresses that may be accessed over the community, the goal’s OS and system structure, and the ports together with their respective companies operating on every pc.
The aim of scanning is to find exploitable communications channels, probe as many listeners as doable, and observe those which are responsive or helpful to an attacker’s explicit wants. Within the scanning part of an assault, the attacker tries to search out varied methods to intrude right into a goal system. The attacker additionally tries to find extra details about the goal system to find out the presence of any configuration lapses. The attacker then makes use of the data obtained to develop an assault technique.
2. Scanning Instruments
Scanning Instruments
Scanning instruments are used to scan and establish stay hosts, open ports, operating companies on a goal community, location information, NetBIOS information, and details about all TCP/IP and UDP open ports. The knowledge obtained from these instruments will assist an moral hacker in creating the profile of the goal group and scanning the community for open ports of the units related.
▪ Nmap Supply: https://nmap.org
▪ Hping3 Supply: https://salsa.debian.org
o ICMP ping Ex. hping3 -1 10.0.0.25
o ACK scan on port 80 Ex. hping3 –A ten.0.0.25 –p 80
o UDP scan on port 80 Ex. hping3 -2 10.0.0.25 –p 80
o Accumulating Preliminary Sequence Quantity Ex. hping3 192.168.1.103 -Q -p 139
o Firewalls and Timestamps Ex. hping3 -S 72.14.207.99 -p 80 –tcp-timestamp
o SYN scan on port 50-60 Ex. hping3 -8 50-60 –S 10.0.0.25 –V
o FIN, PUSH and URG scan on port 80 Ex. hping3 –F –P –U 10.0.0.25 –p 80
o Scan whole subnet for stay host Ex. hping3 -1 10.0.1.x –rand-dest –I eth0
o Intercept all visitors containing HTTP signature Ex. hping3 -9 HTTP –I eth0
o SYN flooding a sufferer Ex. hping3 -S 192.168.1.1 -a 192.168.1.254 -p 22 –flood
▪ Hping Scan with AI
Attackers can leverage AI-powered applied sciences to boost and automate their community scanning duties. With the help of AI, attackers can effortlessly carry out community scanning utilizing the Hping3 software to amass helpful insights about their goal.
Instance #1:
An attacker can use ChatGPT to carry out this process through the use of an applicable immediate reminiscent of: “Use Hping3 to carry out ICMP scanning on the goal IP handle 10.10.1.11 and cease after 10 iterations”
The command `hping3 –icmp –rely 10 10.10.1.11` is used to execute the Hping3 software with particular parameters.
Instance #2:
An attacker can use ChatGPT to carry out this process through the use of an applicable immediate reminiscent of: “Run an hping3 ACK scan on port 80 of goal IP 10.10.1.11”
The command `sudo hping3 –ack -p 80 10.10.1.11` is used to execute the Hping3 software with particular parameters.
▪ Metasploit Supply: https://www.metasploit.com
Metasploit is an open-source challenge that gives the infrastructure, content material, and instruments to carry out penetration exams and intensive safety auditing. It supplies details about safety vulnerabilities and aids in penetration testing and IDS signature growth. It facilitates the duties of attackers, exploits writers, and payload writers. A serious benefit of the framework is the modular method, i.e., permitting the mixture of any exploit with any payload.
▪ NetScanTools Professional Supply: https://www.netscantools.com
NetScanTools Professional is an investigation software that permits you to troubleshoot, monitor, uncover, and detect units in your community. Utilizing this software, you may simply collect details about the native LAN in addition to Web customers, IP addresses, ports, and so forth. Attackers can discover vulnerabilities and uncovered ports within the goal system. It helps the attackers to record IPv4/IPv6 addresses, hostnames, domains, e-mail addresses, and URLs mechanically or manually (utilizing guide instruments). NetScanTools Professional combines many community instruments and utilities categorized by their features, reminiscent of lively, passive, DNS, and native pc.
Some further scanning instruments are listed beneath: ▪ sx (https://github.com) ▪ RustScan (https://github.com) ▪ MegaPing (http://magnetosoft.com) ▪ SolarWinds®Engineer’s Toolset (https://www.solarwinds.com) ▪ PRTG Community Monitor (https://www.paessler.com)
Display Numerous Scanning Methods for Host Discovery
Host Discovery
Scanning is the method of gathering details about programs which are “alive” and responding on the community. Host discovery is taken into account as the first process within the community scanning course of. To carry out a whole scan and establish open ports and companies, it’s essential to test for stay programs. Host discovery supplies an correct standing of the programs within the community, which permits an attacker to keep away from scanning each port on each system in a listing of IP addresses to establish whether or not the goal host is up. Host discovery is step one in community scanning. This part highlights the right way to test for stay programs in a community utilizing varied ping scan methods. It additionally discusses the right way to ping sweep a community to detect stay hosts/programs together with varied ping sweep instruments.
Host Discovery Methods Host discovery methods might be adopted to find the lively/stay hosts within the community. As an moral hacker, you could pay attention to the varied sorts of host discovery methods. Some host discovery methods are listed beneath:
▪ ARP Ping Scan
▪ UDP Ping Scan
▪ ICMP Ping Scan
o ICMP ECHO Ping
• ICMP ECHO Ping Sweep
o ICMP Timestamp Ping
o ICMP Handle Masks Ping
▪ TCP Ping Scan
o TCP SYN Ping
o TCP ACK Ping
▪ IP Protocol Scan
ARP Ping Scan
Within the ARP ping scan, the ARP packets are despatched for locating all lively units within the IPv4 vary regardless that the presence of such units is hidden by restrictive firewalls. In most networks, many IP addresses are unused at any given time, particularly within the non-public handle ranges of the LAN.
Attackers use the Nmap software to carry out ARP ping scan for locating stay hosts within the community. In Zenmap, the -PR choice is used to carry out ARP ping scan.
Notice: -sn is the Nmap command to disable the port scan. Since Nmap makes use of ARP ping scan because the default ping scan, to disable it and carry out different desired ping scans, you should utilize –disable-arp-ping.
Benefits:
▪ ARP ping scan is taken into account to be extra environment friendly and correct than different host discovery methods
▪ ARP ping scan mechanically handles ARP requests, retransmission, and timeout at its personal discretion
▪ ARP ping scan is helpful for system discovery, the place chances are you’ll must scan giant handle areas
▪ ARP ping scan can show the response time or latency of a tool to an ARP packet
UDP Ping Scan
UDP ping scan is just like TCP ping scan; nevertheless, within the UDP ping scan, Nmap sends UDP packets to the goal host. The default port quantity utilized by Nmap for the UDP ping scan is 40,125. This extremely unusual port is used because the default for sending UDP packets to the goal. This default port quantity might be configured utilizing DEFAULT_UDP_PROBE_PORT_SPEC throughout compile time in Nmap. Attackers ship UDP packets to the goal host, and a UDP response signifies that the goal host is lively. If the goal host is offline or unreachable, varied error messages reminiscent of host/community unreachable or TTL exceeded could possibly be returned. In Zenmap, the -PU choice is used to carry out the UDP ping scan.
Benefits: ▪ UDP ping scans have the benefit of detecting programs behind firewalls with strict TCP filtering, leaving the UDP visitors forgotten.
ICMP ECHO
Ping Scan Attackers use the ICMP ping scan to ship ICMP packets to the vacation spot system to assemble all essential details about it. It’s because ICMP doesn’t embody port abstraction, and it’s totally different from port scanning. Nonetheless, it’s helpful to find out what hosts in a community are operating by pinging all of them. ICMP ECHO ping scan entails sending ICMP ECHO requests to a bunch. If the host is alive, it’ll return an ICMP ECHO reply. This scan is helpful for finding lively units or figuring out if ICMP is passing via a firewall.
ICMP ECHO Ping Sweep
A ping sweep (also referred to as an ICMP sweep) is a fundamental community scanning approach that’s adopted to find out the vary of IP addresses that map to stay hosts (computer systems). Though a single ping will inform the person whether or not a specified host pc exists on the community, a ping sweep consists of ICMP ECHO requests despatched to a number of hosts. If a specified host is lively, it’ll return an ICMP ECHO reply. Ping sweeps are among the many oldest and slowest strategies used to scan a community. This utility is distributed throughout practically all platforms, and it acts as a roll name for programs; a system that’s lively on the community solutions the ping question that one other system sends out.
ICMP ECHO Ping Sweep Utilizing Nmap Supply: https://nmap.org Nmap helps an attacker to carry out a ping sweep that determines stay hosts from a spread of IP addresses. In Zenmap, the -PE choice with a listing of IP addresses is used to carry out ICMP ECHO ping sweep.
ICMP Timestamp Ping Scan
Moreover the standard ICMP ECHO ping, there are another sorts of ICMP pinging methods reminiscent of ICMP timestamp ping scan and ICMP handle masks ping scan, which an attacker can undertake in particular situations.
ICMP Handle Masks Ping Scan
ICMP handle masks ping is one other different to the standard ICMP ECHO ping, the place the attackers ship an ICMP handle masks question to the goal host to amass data associated to the subnet masks. Nonetheless, the handle masks response from the vacation spot host is conditional, and it could or might not reply with the suitable subnet worth relying on its configuration by the administrator on the goal’s finish. Such a ping methodology can be efficient in figuring out the lively hosts equally to the ICMP timestamp ping, particularly when the administrator blocks the standard ICMP Echo ping. In Zenmap, the -PM choice is used to carry out an ICMP handle masks ping scan.
TCP SYN Ping Scan TCP SYN ping is a bunch discovery approach for probing totally different ports to find out if the port is on-line and to test if it encounters any firewall rule units. In this kind of host discovery approach, an attacker makes use of the Nmap software to provoke the three-way handshake by sending the empty TCP SYN flag to the goal host. After receiving SYN, the goal host acknowledges the receipt with an ACK flag. After reception of the ACK flag, the attacker confirms that the goal host is lively and terminates the connection by sending an RST flag to the goal host machine (since his/her goal of host discovery is achieved). Port 80 is used because the default vacation spot port. A variety of ports may also be laid out in this kind of pinging format with out inserting an area between -PS and the port quantity (e.g., PS22-25,80,113,1050,35000), the place the probe will probably be carried out in opposition to every port parallelly. In Zenmap, the -PS choice is used to carry out a TCP SYN ping scan.
IP Protocol Ping Scan IP protocol ping is the newest host discovery choice that sends IP ping packets with the IP header of any specified protocol quantity. It has the identical format because the TCP and UDP ping. This system tries to ship totally different packets utilizing totally different IP protocols, hoping to get a response indicating {that a} host is on-line.
Host Discovery with AI
An attacker can even leverage AI-powered ChatGPT or different generative AI know-how to carry out this process through the use of an applicable immediate reminiscent of
- “Scan the goal community 10.10.1.0/24 for lively hosts and place solely the IP addresses right into a file scan1.txt”
- `nmap -sn 10.10.1.0/24 -OG-| awk ‘/Up$/{print $2}’ > scan1.txt`
- “Run a quick however complete Nmap scan in opposition to scan1.txt with low verbosity and write the outcomes to scan2.txt”
- nmap -T4 -iL scan.txt -oN scan2.txt -v0
- “Use Nmap to carry out ICMP ECHO ping sweep on the goal community 10.10.1.0/24”
- nmap -sn -PE 10.10.1.0/24
Ping Sweep Instruments
Ping sweep instruments ping a whole vary of community IP addresses to establish the stay programs. The next are ping sweep instruments that allow one to find out stay hosts on the goal community by sending a number of ICMP ECHO requests to numerous hosts on the community at a time.
▪ Offended IP Scanner Supply: https://angryip.org
▪ SolarWinds Engineer’s Toolset (https://www.solarwinds.com)
▪ NetScanTools Professional (https://www.netscantools.com)
▪ Colasoft Ping Device (https://www.colasoft.com)
▪ Superior IP Scanner (https://www.advanced-ip-scanner.com)
▪ OpUtils (https://www.manageengine.com)
4. Port and Service Discovery
The subsequent step within the community scanning course of entails checking the open ports and companies in stay programs. This discovery of open ports and companies might be carried out through varied port scanning methods. Directors typically use port scanning methods to confirm the safety insurance policies of their networks, whereas attackers use them to establish open ports and operating companies on a bunch with the intent of compromising the community. Furthermore, typically, customers unknowingly hold pointless open ports on their programs. An attacker takes benefit of such open ports to launch assaults.
Port Scanning Methods
Port scanning methods are additional categorized as described beneath. This categorization relies on the kind of protocol used for communication within the community.
TCP Join/Full-Open Scan
Supply: https://insecure.org
TCP Join/Full Open Scan is among the most dependable types of TCP scanning. In TCP Join scanning, the OS’s TCP join() system name tries to open a connection to each port of curiosity on the goal machine. If the port is listening, the join() name will lead to a profitable reference to the host on that specific port; in any other case, it’ll return an error message stating that the port shouldn’t be reachable.
Stealth Scan (Half-Open Scan)
The stealth scan entails resetting the TCP connection between the consumer and the server abruptly earlier than completion of the three-way handshake alerts, therefore making the connection half-open. A stealth scan sends a single body to a TCP port with none TCP handshaking or further packet transfers. Such a scan sends a single body with the expectation of a single response. The half-open scan partially opens a connection however stops midway via. The stealth scan can be referred to as a “SYN scan,” as a result of it solely sends the SYN packet. This prevents the service from notifying the incoming connection. TCP SYN or half-open scanning is a stealth methodology of port scanning. The stealth scan additionally implements the three-way handshake methodology. Within the final stage, it examines the packets coming into the interface and terminates the connection earlier than triggering a brand new initialization to establish distant ports.
Inverse TCP Flag Scan
Attackers ship TCP probe packets with a TCP flag (FIN, URG, PSH) set or with no flags. When the port is open, the attacker doesn’t get any response from the host, whereas when the port is closed, she or he receives the RST from the goal host.
Xmas Scan
Xmas scan is a kind of inverse TCP scanning approach with the FIN, URG, and PUSH flags set to ship a TCP body to a distant system. If the goal has opened the port, then you’ll obtain no response from the distant system. If the goal has closed the port, then you’ll obtain a distant system reply with an RST. You should use this port scanning approach to scan giant networks and discover which host is up and what companies it’s providing. This system describes all TCP flag units. When all flags are set, some programs grasp; therefore, the flags are sometimes set within the nonsense sample URG-PSH-FIN. Attackers use the TCP Xmas scan to find out if ports are closed on the goal machine through the RST packet. This scan solely works when programs are compliant with RFC 793-based TCP/IP implementation. It won’t work in opposition to any present model of Microsoft Home windows.
BSD Networking Code
This methodology depends on the BSD networking code. Thus, you should utilize this just for UNIX hosts; it doesn’t assist Home windows NT. If the person scans any Microsoft system, it’ll present that every one the ports on the host are open.
You may initialize all of the flags when transmitting the packet to a distant host. If the goal system accepts the packet and doesn’t ship any response, it signifies that the port is open. If the goal system sends an RST flag, then it implies that the port is closed.
In Zenmap, the -sX choice is used to carry out Xmas scan whereas the -sF and -sN choices are used to carry out FIN scan and NULL scan, respectively.
nmap -sX -v 192.168.2.79
TCP Maimon Scan
This scan approach is similar to NULL, FIN, and Xmas scan, however the probe used right here is FIN/ACK. Generally, to find out if the port is open or closed, the RST packet must be generated as a response to a probe request. Nonetheless, in lots of BSD programs, the port is open if the packet will get dropped in response to a probe.
5. OS Discovery (Banner Grabbing/OS Fingerprinting)
An attacker makes use of OS discovery or banner grabbing methods to establish community hosts operating purposes and OS variations with recognized exploits. This part introduces you to banner grabbing, its varieties, and banner grabbing instruments.
Two sorts of banner grabbing methods are described beneath:
▪ Lively Banner Grabbing
Lively banner grabbing applies the precept that an OS’s IP stack has a singular manner of responding to specifically crafted TCP packets. This occurs due to totally different interpretations that distributors apply whereas implementing the TCP/IP stack on a selected OS. In lively banner grabbing, the attacker sends a wide range of malformed packets to the distant host, and the responses are in contrast with a database. Responses from totally different OS range due to variations in TCP/IP stack implementation.
As an example, the scanning utility Nmap makes use of a sequence of 9 exams to find out an OS fingerprint or banner grabbing. The exams listed beneath present some insights into an lively banner grabbing assault, as described at https://nmap.org/e book/osdetect-methods.html#osdetect-probes
▪ Passive Banner Grabbing Supply: https://www.broadcom.com
Like lively banner grabbing, passive banner grabbing additionally will depend on the differential implementation of the stack and the varied methods wherein an OS responds to packets. Nonetheless, as a substitute of counting on scanning the goal host, passive fingerprinting captures packets from the goal host through sniffing to review telltale indicators that may reveal an OS.
Determine Goal System OS
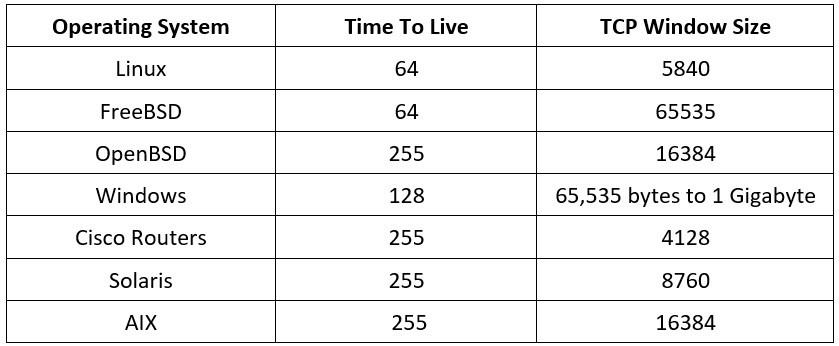
Figuring out the goal OS is among the vital duties for an attacker to compromise the goal community/machine. In a community, varied requirements are applied to permit totally different OSs to speak with one another. These requirements govern the functioning of varied protocols reminiscent of IP, TCP, UDP, and so on. By analyzing sure parameters/fields in these protocols, one can reveal the small print of the OS. Parameters reminiscent of Time to Dwell (TTL) and TCP window dimension within the IP header of the primary packet in a TCP session assist establish the OS operating on the goal machine. The TTL discipline determines the utmost time {that a} packet can stay in a community, and the TCP window dimension determines the size of the packet reported. These values range amongst OSs, as described within the following desk:
Attackers can use varied instruments to carry out OS discovery on the goal machine, together with Wireshark, Nmap, Unicornscan, and Nmap Script Engine. Attackers can even undertake the IPv6 fingerprinting methodology to seize the goal OS particulars.
OS Discovery utilizing Wireshark Supply: https://www.wireshark.org
OS Discovery utilizing Nmap and Unicornscan
OS Discovery utilizing Nmap Supply: https://nmap.org
To take advantage of the goal, it’s extremely important to establish the OS operating on the goal machine. Attackers can make use of varied instruments to amass the OS particulars of the goal. Nmap is among the efficient instruments for performing OS discovery actions. In Zenmap, the -O choice is used to carry out OS discovery, which shows the OS particulars of the goal machine.
OS Discovery utilizing Unicornscan
Supply: https://sourceforge.web In Unicornscan, the OS of the goal machine might be recognized by observing the TTL values within the acquired scan consequence. To carry out Unicornscan, the syntax #unicornscan
OS Discovery utilizing Nmap Script Engine
Supply: https://nmap.org Nmap Scripting Engine (NSE) in Nmap can be utilized to automate all kinds of networking duties by permitting customers to jot down and share scripts. These scripts might be executed parallelly with the identical effectivity and velocity as Nmap. Attackers can even use varied scripts within the Nmap Script Engine for performing OS discovery on the goal machine. For instance, in Nmap, smb-os-discovery is an inbuilt script used for gathering OS data on the goal machine via the SMB protocol. In Zenmap, NSE might be typically activated utilizing the -sC choice. If the customized scripts are to be specified, then attackers can use the –script choice. The NSE outcomes will probably be displayed with each the Nmap regular and XML outputs.
OS Discovery utilizing IPv6 Fingerprinting Supply: https://nmap.org IPv6 Fingerprinting is one other approach used to establish the OS operating on the goal machine. It has the identical performance as IPv4, reminiscent of sending probes, ready and gathering the responses, and matching them with the database of fingerprints. The distinction between IPv6 and IPv4 fingerprinting is that IPv6 makes use of a number of further superior IPv6-specific probes together with a separate IPv6-specifc OS detection engine. Nmap sends practically 18 probes within the following order to establish the goal OS utilizing the IPv6 fingerprinting methodology. ▪ Sequence technology (S1–S6) ▪ ICMPv6 echo (IE1) ▪ ICMPv6 echo (IE2) ▪ Node Info Question (NI) ▪ Neighbor Solicitation (NS) ▪ UDP (U1) ▪ TCP specific congestion notification (TECN) ▪ TCP (T2–T7)
In Zenmap, the -6 choice together with -O choice is used to carry out OS discovery utilizing the IPv6 fingerprinting methodology.
Syntax: # nmap -6 -O
OS Discovery with AI
An attacker can even leverage AI-powered ChatGPT or different generative AI know-how to carry out this process through the use of an applicable immediate reminiscent of
• “Use TTL to establish the working system operating on the goal IP handle 10.10.1.11”
ping -c 1 10.10.1.11 && echo “Test the TTL worth from the response to deduce the OS (Linux/Unix: 64, Home windows: 128)”
• “Use TTL to establish the working system operating on the goal IP handle 10.10.1.9”
ping -c 1 10.10.1.9 | grep “ttl”
• “Use Nmap script engine to carry out OS discovery on the goal IP addresses in scan1.txt”
nmap -iL scan1.txt -O –script=default –script-args=newtargets -oN os_discovery_results.txt
Create and Run Customized Script to Automate Community Scanning Duties With AI Attackers can leverage AI-powered applied sciences to boost and automate their community scanning duties. With the help of AI, attackers can effortlessly create and run customized community scanning scripts and purchase helpful insights about their targets. By creating such customized scripts, attackers can effectively execute a sequence of community scanning instructions to assemble details about a goal area. With this script, attackers can uncover stay programs, open ports, operating companies, service variations, and extra on the goal IP ranges.
As an example, Attackers can use ChatGPT to information the event of a script through the use of an applicable immediate reminiscent of: “Develop a script that may automate community scanning efforts and discover out stay programs, open ports, operating companies, service variations, and so on. heading in the right direction IP vary 10.10.1.0/24”
The next bash script is designed to automate community scanning efforts on the goal IP vary 10.10.1.0/24:
#!/bin/bash
nmap -sP 10.10.1.0/24 -oG – | awk ‘/Up$/{print $2}’ > live_hosts.txt && nmap -iL live_hosts.txt -sV -oA scan_results && cat scan_results.nmap
6. Scanning Past IDS and Firewall
Intrusion detection programs (IDS) and firewalls are safety mechanisms supposed to forestall an attacker from accessing a community. Nonetheless, even IDS and firewalls have some safety limitations. Attackers attempt to launch assaults to take advantage of these limitations. This part highlights varied IDS/firewall evasion methods reminiscent of packet fragmentation, supply routing, IP handle spoofing, and so on.
Though firewalls and IDS can forestall malicious visitors (packets) from coming into a community, attackers can ship supposed packets to the goal that evade the IDS/firewall by implementing the next methods: ▪ Packet Fragmentation ▪ Supply Routing ▪ Supply Port Manipulation ▪ IP Handle Decoy ▪ IP Handle Spoofing ▪ MAC Handle Spoofing ▪ Creating Customized Packets ▪ Randomizing Host Order ▪ Sending Dangerous Checksums ▪ Proxy Servers ▪ Anonymizers
Packet Fragmentation
Packet fragmentation refers back to the splitting of a probe packet into a number of smaller packets (fragments) whereas sending it to a community. When these packets attain a bunch, the IDS and firewalls behind the host typically queue all of them and course of them one after the other. Nonetheless, since this methodology of processing entails better CPU and community useful resource consumption, the configuration of most IDS trigger them to skip fragmented packets throughout port scans. Due to this fact, attackers use packet fragmentation instruments reminiscent of Nmap to separate the probe packet into smaller packets that circumvent the port-scanning methods employed by IDS. As soon as these fragments attain the destined host, they’re reassembled to type a single packet.
SYN/FIN Scanning
Utilizing IP Fragments SYN/FIN scanning utilizing IP fragments shouldn’t be a brand new scanning methodology however a modification of earlier methods. This technique of scanning was developed to keep away from false positives generated by different scans due to a packet filtering system on the goal system. The TCP header splits into a number of packets to evade the packet filter. For any transmission, each TCP header will need to have the supply and vacation spot port for the preliminary packet (8-octet, 64-bit). The initialized flags within the subsequent packet enable the distant host to reassemble the packets upon receipt through an Web protocol module that detects the fragmented knowledge packets utilizing field-equivalent values of the supply, vacation spot, protocol, and identification.
Supply Routing
An IP datagram incorporates varied fields, together with the IP choices discipline, which shops supply routing data and features a record of IP addresses via which the packet travels to its vacation spot. Because the packet travels via the nodes within the community, every router examines the vacation spot IP handle and chooses the following hop to direct the packet to the vacation spot. When attackers ship malformed packets to a goal, these packets hop via varied routers and gateways to succeed in the vacation spot. In some instances, the routers within the path would possibly embody configured firewalls and IDS that block such packets. To keep away from them, attackers implement a free or strict supply routing mechanism, wherein they manipulate the IP handle path within the IP choices discipline in order that the packet takes the attacker-defined path (with out firewall-/IDS-configured routers) to succeed in the vacation spot, thereby evading firewalls and IDS.
Supply Port Manipulation
Supply port manipulation is a method used for bypassing the IDS/firewall, the place the precise port numbers are manipulated with widespread port numbers for evading sure IDS and firewall guidelines. The primary safety misconfigurations happen due to blindly trusting the supply port quantity. The administrator largely configures the firewall by permitting the incoming visitors from well-known ports reminiscent of HTTP, DNS, FTP, and so on. The firewall can merely enable the incoming visitors from the packets despatched by the attackers utilizing such widespread ports.
IP Handle Decoy
The IP handle decoy approach refers to producing or manually specifying IP addresses of the decoys to evade IDS/firewalls. It seems to the goal that the decoys in addition to the host(s) are scanning the community. This system makes it tough for the IDS/firewall to find out which IP handle is definitely scanning the community and which IP addresses are decoys. The Nmap scanning software comes with a built-in scan perform referred to as a decoy scan, which cloaks a scan with decoys. This system generates a number of IP addresses to carry out a scan, thus making it tough for the goal safety mechanisms reminiscent of IDS, firewalls, and so on., to establish the unique supply from the registered logs. The goal IDS would possibly report scanning from 5–0 IP addresses; nevertheless, it can’t differentiate between the precise scanning IP handle and the innocuous decoy IPs.
▪ nmap -D RND:10 [target]
▪ nmap -D decoy1,decoy2,decoy3,…,ME,… [target
IP Address Spoofing
Most firewalls filter packets based on the source IP address. These firewalls examine the source IP address and determine whether the packet is coming from a legitimate source or an illegitimate source. The IDS filters packets from illegitimate sources. Attackers use IP spoofing technique to bypass such IDS/firewalls.
- IP spoofing using Hping3: Hping3 www.certifiedhacker.com -a 7.7.7.7
MAC Address Spoofing
Network firewalls filter packets based on the source media access control (MAC) address. They examine the MAC address in the packet header and determine whether the packets originate from a legitimate source. Firewalls allow traffic from specific sources using MAC filtering rules and restrict packets that do not satisfy the filtering rules. To avoid these restrictions, attackers use MAC spoofing techniques, in which they employ fake MAC addresses and masquerade as legitimate users to scan the hosts located behind the firewall.
▪ nmap -sT -Pn –spoof-mac 0 [Target IP]
▪ nmap -sT -Pn –spoof-mac [Vendor] [Target IP]
▪ nmap -sT -Pn –spoof-mac [new MAC] [Target IP]
Creating Customized Packets
The attacker creates and sends customized packets to scan the supposed goal past the IDS/firewalls. Numerous methods are used to create customized packets. A few of them are talked about beneath:
▪ Creating Customized Packets through the use of Packet Crafting Instruments Attackers create customized TCP packets to scan the goal by bypassing the firewalls. Attackers use varied packet crafting instruments reminiscent of Colasoft packet builder (https://www.colasoft.com), NetScanTools Professional (https://www.netscantools.com), and so on., to scan the goal that’s past the firewall. Packet crafting instruments craft and ship packet streams (customized packets) utilizing totally different protocols at totally different switch charges.
Randomizing Host Order
The attacker scans the variety of hosts within the goal community in a random order to scan the supposed goal that’s mendacity past the firewall. The choice utilized by Nmap to scan with a random host order is –randomize-hosts. This system instructs Nmap to shuffle every group of 16384 hosts earlier than scanning with sluggish timing choices, thus making the scan much less notable to community monitoring programs and firewalls. If bigger group sizes are randomized, the PING_GROUP_SZ must be elevated in nmap.h and it must be compiled once more. One other methodology might be adopted by producing the goal IP record with the record scan command -sL -n -oN
Sending Dangerous Checksums
The attacker sends packets with dangerous or bogus TCP/UDP checksums to the supposed goal to keep away from sure firewall rule units. TCP/UDP checksums are used to make sure knowledge integrity. Sending packets with incorrect checksums may also help attackers to amass data from improperly configured programs by checking for any response. If there’s a response, then it’s from the IDS or firewall, which didn’t confirm the obtained checksum. If there isn’t a response or the packets are dropped, then it may be inferred that the system is configured. This system instructs Nmap to ship packets with invalid TCP, UDP, or SCTP checksums to the goal host. The choice utilized by Nmap is –badsum.
Proxy Servers
A proxy server is an utility that may function an middleman for connecting with different computer systems. A proxy server is used:
▪ As a firewall and to guard the native community from exterior assaults. ▪ As an IP handle multiplexer that permits a number of computer systems to hook up with the Web when you may have just one IP handle (NAT/PAT).
▪ To anonymize net browsing (to some extent). ▪ To extract undesirable content material, reminiscent of adverts or “unsuitable” materials (utilizing specialised proxy servers).
▪ To offer some safety in opposition to hacking assaults. ▪ To avoid wasting bandwidth.
Free Proxy Servers
Some free proxy servers obtainable on the Web, which may also help you to entry restricted websites with out revealing your IP handle. Within the Google search engine, kind “Free Proxy Servers” to see a listing of such servers. Choose one from this record and obtain and set up it to browse anonymously with out revealing your professional IP handle.
Proxy Chaining
Proxy chaining helps an attacker to extend his/her Web anonymity. Web anonymity will depend on the variety of proxies used for fetching the goal utility; the bigger the variety of proxy servers used, the better is the attacker’s anonymity.
Proxy Instruments
Proxy instruments are supposed to permit customers to surf the Web anonymously by protecting their IP hidden via a sequence of SOCKS or HTTP proxies. These instruments can even act as HTTP, mail, FTP, SOCKS, information, telnet, and HTTPS proxy servers.
▪ Proxy Switcher Supply: https://www.proxyswitcher.com
▪ CyberGhost VPN Supply: https://www.cyberghostvpn.com
Along with the proxy instruments talked about above, there are a lot of different proxy instruments supposed to permit customers to surf the Web anonymously. Some further proxy instruments are listed beneath: ▪ Burp Suite (https://www.portswigger.web) ▪ Tor (https://www.torproject.org) ▪ Hotspot Protect (https://www.hotspotshield.com) ▪ Proxifier (https://www.proxifier.com) ▪ IPRoyal Residential Proxy (https://iproyal.com)
Anonymizers
An anonymizer is an intermediate server positioned between an finish person and a web site that accesses the web site on their behalf and makes net browsing actions untraceable. Anonymizers enable customers to bypass Web censorship. An anonymizer eliminates all figuring out data (IP handle) from the system whereas browsing the Web, thereby making certain privateness. It encrypts the information transferred from a pc to the Web service supplier (ISP). Most anonymizers can anonymize net (HTTP:), File Switch Protocol (FTP:), and gopher (gopher:) Web companies.
Anonymizer instruments use varied methods reminiscent of SSH, VPN, and HTTP proxies, which permit entry to blocked or censored content material on the Web with commercials omitted.
▪ Whonix Supply: https://www.whonix.org
Some further anonymizers are listed beneath:
▪ Psiphon (https://psiphon.ca) ▪ TunnelBear (https://www.tunnelbear.com) ▪ Invisible Web Undertaking (I2P) (https://geti2p.web) ▪ Brilliant Information Proxy API (https://brightdata.com)
Censorship Circumvention Instruments
▪ AstrillVPN Supply: https://www.astrill.com
▪ Tails Supply: https://tails.web
7. Community Scanning Countermeasures
In moral hacking, the moral hacker, also referred to as the “pen tester,” has to carry out a further process {that a} regular hacker doesn’t observe (i.e., adopting countermeasures in opposition to the respective vulnerabilities decided via hacking). That is important as a result of understanding safety loopholes in your community is nugatory until you undertake measures to guard them in opposition to actual hackers. This part discusses varied countermeasures to defend in opposition to community scanning assaults.
Ping Sweep Countermeasures
Some countermeasures for stopping ping sweep makes an attempt are as follows: ▪ Configure firewalls to dam incoming ICMP echo requests from unknown or untrusted sources.
▪ Use intrusion detection programs (IDSes) and intrusion prevention programs (IPSes), reminiscent of Snort (https://www.snort.org), to detect and stop ping-sweep makes an attempt.
▪ Rigorously consider the kind of Web Management Message Protocol (ICMP) visitors flowing via enterprise networks.
▪ Terminate the reference to any host sending greater than 10 ICMP ECHO requests. ▪ Use a demilitarized zone (DMZ) and permit solely instructions reminiscent of ICMP ECHO_REPLY, HOST UNREACHABLE, and TIME EXCEEDED within the DMZ.
▪ Restrict ICMP visitors with access-control lists (ACLs) to the ISP’s particular IP addresses. ▪ Implement charge limiting for ICMP packets to cut back the efficacy of ping sweeps and different ICMP-based scanning methods.
▪ Break the community into smaller, remoted segments. This limits the scope of what an attacker can uncover via a ping sweep and makes lateral motion tougher if the community is compromised.
▪ Make the most of non-public IP handle ranges for inner community units and implement community handle translation (NAT) on the community boundary. This hides inner IP addresses from exterior observers.
Port Scanning Countermeasures
As mentioned beforehand, port scanning supplies a considerable amount of helpful data to attackers, reminiscent of IP addresses, host names, open ports, and companies operating on ports. Open ports particularly supply a simple means for an attacker to interrupt into the community. Nonetheless, there isn’t a trigger for concern, offered that the system or community is secured in opposition to port scanning by adopting the next countermeasures: ▪ Configure firewall and intrusion detection system (IDS) guidelines to detect and block probes. ▪ The firewall must be able to detecting the probes despatched by attackers utilizing port-scanning instruments. It mustn’t enable visitors to move via after merely inspecting the TCP header. The firewall ought to be capable to study the information contained in every packet earlier than permitting visitors to move via it.
▪ Run the port scanning instruments in opposition to hosts on the community to find out whether or not the firewall precisely detects the port scanning exercise.
▪ Make sure that the router, IDS, and firewall firmware are up to date with their newest releases/variations.
▪ Configure industrial firewalls to guard the community in opposition to quick port scans and SYN floods.
▪ Hackers use instruments reminiscent of Nmap and carry out OS detection to smell the small print of a distant OS. Thus, you will need to make use of an IDS in such instances. Snort (https://www.snort.org) is a really helpful intrusion detection and prevention know-how, primarily as a result of signatures are regularly obtainable from public authors.
▪ Hold as few ports open as doable and filter the remaining, as an intruder might try and enter via any open port. Use a customized rule set to lock down the community, block undesirable ports on the firewall, and filter the next ports: 135–159, 256–258, 389, 445, 1080, 1745, and 3268.
▪ Block undesirable companies operating on the ports and replace the service variations. ▪ Make sure that the variations of companies operating on the ports are non-vulnerable. ▪ Block inbound ICMP message varieties and all outbound ICMP type-3 unreachable messages at border routers organized in entrance of the corporate’s foremost firewall.
▪ Attackers try and carry out supply routing and ship packets to the targets, which is probably not reachable through the Web, utilizing an intermediate host that may work together with the goal. Therefore, it’s essential to make sure that the firewall and router can block such source-routing methods.
▪ Make sure that the mechanisms used for routing and filtering on the routers and firewalls, respectively, can’t be bypassed utilizing a selected supply port or supply routing strategies.
▪ Take a look at the IP handle house utilizing TCP and UDP port scans in addition to ICMP probes to find out the community configuration and accessible ports.
▪ Make sure that the anti-scanning and anti-spoofing guidelines are configured. ▪ If a industrial firewall is in use, then guarantee the next: o It’s patched with the newest updates. o It has accurately outlined anti-spoofing guidelines. o Its fast-mode companies are unusable.
▪ Make sure that TCP wrappers restrict entry to the community primarily based on domains or IP addresses.
▪ Use proxy servers to dam fragmented or malformed packets. ▪ Make sure that the firewalls ahead open port scans to empty hosts or honeypots to make the port-scanning process tough and time-consuming.
▪ Make use of an intrusion prevention system (IPS) to establish port scan makes an attempt and blacklist IP addresses.
▪ Implement port knocking to cover open ports. ▪ Use community handle translation (NAT) to cover the IP addresses of inner programs. ▪ Implement egress filtering to manage outbound visitors, which may also help in figuring out and stopping malicious inner hosts from scanning exterior targets.
▪ Implement digital native space networks (VLANs) to isolate several types of visitors and limit entry between them.
Banner Grabbing Countermeasures
▪ Disabling or Altering Banner An open port signifies {that a} service/banner is operating on it. When attackers connect with an open port utilizing banner grabbing methods, the system presents a banner containing delicate data such because the OS, server kind, and model. Utilizing the data gathered, the attacker identifies particular vulnerabilities to take advantage of after which launches assaults. The countermeasures in opposition to banner grabbing assaults are as follows: o Show false banners to mislead or deceive attackers. o Flip off pointless companies on the community host to restrict data disclosure. o Use server masking instruments to disable or change banner data. o Take away pointless HTTP headers and response knowledge and camouflage the server by offering false signatures. This additionally supplies the choice of eliminating file extensions reminiscent of .asp and .aspx, which clearly point out that the positioning is operating on a Microsoft server.
o For Apache 2.x with the mod_headers module, use a directive within the httpd.conf file to vary the banner data header and set the server as New Server Identify.
o Alternatively, change the ServerSignature line to ServerSignatureOff within the httpd.conf file.
o Disable the small print of the seller and model within the banners.
o Modify the worth of Server Tokens from Full to Prod in Apache’s httpd.conf file to forestall disclosure of the server model.
o Modify the worth of RemoveServerHeader from 0 to 1 within the UrlScan.ini config file discovered at C: WindowsSystem32inetservUrlscan. This methodology prevents disclosure of the server model.
o Trick attackers by modifying the worth of AlternateServerName to values reminiscent of xyz or myserver.
o Disable HTTP strategies reminiscent of Join, Put, Delete, and Choices from net utility servers.
o Take away the X-Powered-By header solely with the customHeaders choice within the
▪ Hiding File Extensions from Net Pages
File extensions reveal details about the underlying server know-how that an attacker can use to launch assaults. The countermeasures in opposition to such banner grabbing assaults are as follows:
o Disguise file extensions to masks the net know-how.
o Change utility mappings reminiscent of .asp with .htm, .foo, and so on. to disguise the identities of servers.
o Apache customers can use mod_negotiation directives.
▪ Different Banner Grabbing Countermeasures
o Use packet filtering to dam or limit entry to ports that may reveal banner data unnecessarily.
o Use IDS/IPS programs to watch and alert on scanning actions that might point out banner grabbing makes an attempt.
o Change protocols that ship clear-text banners (reminiscent of HTTP, FTP, and Telnet) with their safe counterparts (HTTPS, SFTP/FTPS, SSH) to encrypt the connection and banner data.
o Use transport layer safety (TLS) for companies to encrypt the banner data in the course of the handshake course of, making it tougher for unauthorized events to seize banners.
Notice: It’s preferable to not use file extensions in any respect.
IP Spoofing Detection Methods
▪ Direct TTL Probes
On this approach, you initially ship a packet (ping request) to the professional host and watch for a reply. Test whether or not the TTL worth within the reply matches with that of the packet you’re checking. Each could have the identical TTL if they’re utilizing the identical protocol. Though the preliminary TTL values range based on the protocol used, a number of preliminary TTL values are generally used. For TCP/UDP, the values are 64 and 128; for ICMP, they’re 128 and 255.
If the reply is from a unique protocol, then you need to test the precise hop rely to detect the spoofed packets. Deduct the TTL worth within the reply from the preliminary TTL worth to find out the hop rely. The packet is a spoofed packet if the reply TTL doesn’t match the TTL of the packet. It is going to be very simple to launch an assault if the attacker is aware of the hop rely between the supply and the host. On this case, the check result’s a false unfavorable. This system is profitable when the attacker is in a unique subnet from that of the sufferer.
Notice: Regular visitors from one host can distinction TTLs relying on visitors patterns.
▪ IP Identification Quantity
Customers can establish spoofed packets by monitoring the IP identification (IPID) quantity within the IP packet headers. The IPID will increase incrementally every time a system sends a packet. Each IP packet on the community has a singular “IP identification” quantity, which is elevated by one for each packet transmission. To establish whether or not a packet is spoofed, ship a probe packet to the supply IP handle of the packet and observe the IPID quantity within the reply. The IPID worth within the response packet should be near however barely better than the IPID worth of the probe packet. The supply handle of the IP packet is spoofed if the IPID of the response packet shouldn’t be near that of the probe packet. This methodology is efficient even when each the attacker and the goal are on the identical subnet.
▪ TCP Movement Management Technique
The TCP can optimize the circulate management on each the sender’s and the receiver’s finish with its algorithm. The algorithm accomplishes circulate management utilizing the sliding window precept. The person can management the circulate of IP packets by the window dimension discipline within the TCP header. This discipline represents the utmost quantity of knowledge that the recipient can obtain and the utmost quantity of knowledge that the sender can transmit with out acknowledgement. Thus, this discipline helps to manage knowledge circulate. The sender ought to cease sending knowledge each time the window dimension is about to zero.
Usually circulate management, the sender ought to cease sending knowledge as soon as the preliminary window dimension is exhausted. The attacker, who’s unaware of the ACK packet containing window dimension data, would possibly proceed to ship knowledge to the sufferer. If the sufferer receives knowledge packets past the window dimension, they’re spoofed packets. For efficient circulate management and early detection of spoofing, the preliminary window dimension should be very small.
Most spoofing assaults happen in the course of the handshake, as it’s difficult to construct a number of spoofing replies with the proper sequence quantity. Due to this fact, apply the circulate management spoofed packet detection methodology to the handshake. In a TCP handshake, the host sending the preliminary SYN packet waits for SYN-ACK earlier than sending the ACK packet. To test whether or not you’re getting the SYN request from a real consumer or a spoofed one, set SYN-ACK to zero. If the sender sends an ACK with any knowledge, it signifies that the sender is a spoofed one. It’s because when SYN-ACK is about to zero, the sender should reply to it solely with the ACK packet, with out further knowledge.
Attackers sending spoofed TCP packets won’t obtain the goal’s SYN-ACK packets. Attackers can’t reply to modifications within the congestion window dimension. When the obtained visitors continues after a window dimension is exhausted, the packets are almost definitely spoofed.
IP Spoofing Countermeasures
As talked about beforehand, IP spoofing is a method adopted by a hacker to interrupt right into a goal community. Due to this fact, to guard the community from exterior hackers, IP spoofing countermeasures must be utilized in community safety settings. Some IP spoofing countermeasures that may be utilized are as follows: ▪ Keep away from Belief Relationships Don’t depend on IP-based authentication. Attackers might masquerade as trusted hosts and
ship malicious packets. If these packets are accepted underneath the idea that they’re “clear” as a result of they’re from a trusted host, malicious code will infect the system. Due to this fact, it’s advisable to check all packets, even once they originate from a trusted host. This drawback might be prevented by implementing password authentication together with belief relationship–primarily based authentication.
▪ Use Firewalls and Filtering Mechanisms
As said above, all incoming and outgoing packets must be filtered to keep away from assaults and lack of delicate data. A firewall can limit malicious packets from coming into a non-public community and stop extreme knowledge loss. Entry-control lists (ACLs) can be utilized to dam unauthorized entry. Nonetheless, the potential for an insider assault additionally exists. Inside attackers can ship delicate details about the enterprise to opponents, which may result in monetary loss and different points. One other danger of outgoing packets is that an attacker might reach putting in a malicious sniffing program operating in a hidden mode on the community. These applications collect and ship all of the community data to the attacker with none notification after filtering out the outgoing packets. Due to this fact, the scanning of outgoing packets should be assigned the identical significance as that of incoming packets.
▪ Use Random Preliminary Sequence Numbers
Most units select their preliminary sequence numbers (ISNs) primarily based on timed counters. This makes the ISNs predictable, as it’s simple for an attacker to find out the idea of producing an ISN. The attacker can decide the ISN of the following TCP connection by analyzing the ISN of the present session or connection. If the attacker can predict the ISN, then they’ll set up a malicious connection to the server and sniff community visitors. To keep away from this danger, use random ISNs.
▪ Ingress Filtering
Ingress filtering prevents spoofed visitors from coming into the Web. It’s utilized to routers as a result of it enhances the performance of the routers and blocks spoofed visitors. Configuring and utilizing ACLs that drop packets with a supply handle exterior the outlined vary is one methodology of implementing ingress filtering.
▪ Egress Filtering
Egress filtering is a apply that goals to forestall IP spoofing by blocking outgoing packets with a supply handle from the surface.
▪ Use Encryption
To maximise community safety, use robust encryption for all visitors positioned on transmission media with out contemplating its kind and site. That is the very best methodology to forestall IP spoofing assaults. IPSec can be utilized to drastically cut back the IP spoofing danger, because it supplies knowledge authentication, integrity, and confidentiality. Encryption periods must be enabled on the router in order that trusted hosts can talk securely with native hosts. Attackers are inclined to concentrate on targets which are simple to compromise. If an attacker wishes to interrupt into an encrypted community, they have to decrypt the complete slew of encrypted packets, which is a tough process. Due to this fact, an attacker is prone to transfer on and try to search out one other goal that’s simple to compromise or just abort the try. Furthermore, use the newest encryption algorithms that present robust safety.
▪ SYN Flooding Countermeasures Countermeasures in opposition to SYN flooding assaults can even assist keep away from IP spoofing assaults. ▪ Different IP Spoofing Countermeasures
o Improve the integrity and confidentiality of internet sites by migrating from IPv4 to IPv6 throughout growth.
o Implement digital certificates authentication mechanisms reminiscent of area and two-way auth certificates verification.
o Use a safe VPN whereas accessing any kind of public Web service reminiscent of free Wi-Fi and hotspots.
o Make use of application-specific mitigation units reminiscent of Behemoth scrubbers for deep-level packet investigation at a excessive velocity of practically 100 million packets/s.
cut back the time of lively vulnerability.
o Configure routers to ship encoded details about fragmented packets coming into the community.
o Configure routers to confirm the information packets utilizing their signatures by storing the arrival knowledge packet digests.
o Configure routers to cover intranet hosts from the exterior community by implementing modifications to the community handle translation (NAT).
o Configure inner switches to desk the DHCP static addresses to filter malicious spoofed visitors.
o Use safe variations of communication protocols (reminiscent of HTTPS, SFTP, and SSH) that supply encryption and authentication.
Scanning Detection and Prevention Instruments Safety professionals use varied subtle instruments reminiscent of ExtraHop and Splunk Enterprise Safety to detect lively networks and port scanning makes an attempt initiated by attackers.
▪ ExtraHop Supply: https://www.extrahop.com
A number of the further scanning detection and prevention instruments are listed beneath: ▪ Splunk Enterprise Safety (https://www.splunk.com) ▪ Scanlogd (https://github.com) ▪ Vectra Detect (https://www.vectra.ai) ▪ IBM Safety QRadar XDR (https://www.ibm.com) ▪ Cynet 360 AutoXDRTM (https://www.cynet.com)
Lab
Situation
Earlier, you gathered all doable details about the goal reminiscent of group data (worker particulars, companion particulars, net hyperlinks, and so on.), community data (domains, sub-domains, sub sub-domains, IP addresses, community topology, and so on.), and system data (OS particulars, person accounts, passwords, and so on.).
Now, as an moral hacker, or as a penetration tester (hereafter, pen tester), the next step will probably be to carry out port scanning and community scanning on the IP addresses that you simply obtained within the information-gathering part. This may assist you to establish an entry level into the goal community.
Scanning itself shouldn’t be the precise intrusion, however an prolonged type of reconnaissance wherein the moral hacker and pen tester learns extra in regards to the goal, together with details about open ports and companies, OSes, and any configuration lapses. The knowledge gleaned from this reconnaissance lets you choose methods for the assault on the goal system or community.
This is among the most vital phases of intelligence gathering, which allows you to create a profile of the goal group. Within the technique of scanning, you try to assemble data, together with the particular IP addresses of the goal system that may be accessed over the community (stay hosts), open ports, and respective companies operating on the open ports and vulnerabilities within the stay hosts.
Port scanning will assist you establish open ports and companies operating on particular ports, which entails connecting to Transmission Management Protocol (TCP) and Person Datagram Protocol (UDP) system ports. Port scanning can be used to find the vulnerabilities within the companies operating on a port.
The target of this lab is to conduct community scanning, port scanning, analyzing the community vulnerabilities, and so on.
Community scans are wanted to:
- Test stay programs and open ports
- Determine companies operating in stay programs
- Carry out banner grabbing/OS fingerprinting
- Determine community vulnerabilities
Overview of Scanning Networks
Community scanning is the method of gathering further detailed details about the goal through the use of extremely advanced and aggressive reconnaissance methods. The aim of scanning is to find exploitable communication channels, probe as many listeners as doable, and hold observe of the responsive ones.
Kinds of scanning:
- Port Scanning: Lists open ports and companies
- Community Scanning: Lists the lively hosts and IP addresses
- Vulnerability Scanning: Reveals the presence of recognized weaknesses
Moral hackers and pen testers use quite a few instruments and methods to scan the goal community. Beneficial labs that may help you in studying varied community scanning methods embody:
-
Carry out host discovery
- Carry out host discovery utilizing Nmap
-
Carry out port and repair discovery
- Discover varied community scanning methods utilizing Nmap
-
Carry out OS discovery
- Carry out OS discovery utilizing Nmap Script Engine (NSE)
-
Scan past IDS and Firewall
- Scan past IDS/firewall utilizing varied evasion methods
-
Carry out community scanning utilizing varied scanning instruments
- Scan a goal community utilizing Metasploit
-
Carry out Community Scanning utilizing AI
- Scan a Goal utilizing ShellGPT
- Carry out host discovery utilizing Nmap
Overview of Host Discovery
Host discovery is taken into account the first process within the community scanning course of. It’s used to find the lively/stay hosts in a community. It supplies an correct standing of the programs within the community, which, in flip, reduces the time spent on scanning each port on each system in a sea of IP addresses so as to establish whether or not the goal host is up.
The next are examples of host discovery methods:
- ARP ping scan
- UDP ping scan
- ICMP ping scan (ICMP ECHO ping, ICMP timestamp, ping ICMP, and handle masks ping)
- TCP ping scan (TCP SYN ping and TCP ACK ping)
- IP protocol ping scan
Nmap is a utility used for community discovery, community administration, and safety auditing. Additionally it is used to carry out duties reminiscent of community stock, managing service improve schedules, and monitoring host or service uptime.
Right here, we’ll use Nmap to find a listing of stay hosts within the goal community. We are able to use Nmap to scan the lively hosts within the goal community utilizing varied host discovery methods reminiscent of ARP ping scan, UDP ping scan, ICMP ECHO ping scan, ICMP ECHO ping sweep, and so on.
Run nmap -sn -PR [Target IP Address] command (right here, the goal IP handle is 10.10.1.22).
-sn: disables port scan and -PR: performs ARP ping scan.
┌─[root@parrot]─[/home/attacker]
└──╼ #nmap -sn -PR 10.10.1.22
Beginning Nmap 7.94SVN ( https://nmap.org ) at 2025-02-23 11:29 EST
Nmap scan report for 10.10.1.22
Host is up (0.00077s latency).
MAC Handle: 00:15:5D:01:80:02 (Microsoft)
Nmap completed: 1 IP handle (1 host up) scanned in 0.16 seconds
┌─[root@parrot]─[/home/attacker]
└──╼ #
The ARP ping scan probes ARP request to focus on host; an ARP response signifies that the host is lively.
Run nmap -sn -PU [Target IP Address] command, (right here, the goal IP handle is 10.10.1.22). The scan outcomes seem, indicating the goal Host is up, as proven within the screenshot.
-PU: performs the UDP ping scan.
The UDP ping scan sends UDP packets to the goal host; a UDP response signifies that the host is lively. If the goal host is offline or unreachable, varied error messages reminiscent of “host/community unreachable” or “TTL exceeded” could possibly be returned.
Now, we’ll carry out the ICMP ECHO ping scan. Run nmap -sn -PE [Target IP Address] command, (right here, the goal IP handle is 10.10.1.22). The scan outcomes seem, indicating that the goal Host is up, as proven within the screenshot.
-PE: performs the ICMP ECHO ping scan.
The ICMP ECHO ping scan entails sending ICMP ECHO requests to a bunch. If the goal host is alive, it’ll return an ICMP ECHO reply. This scan is helpful for finding lively units or figuring out if the ICMP is passing via a firewall.
Now, we’ll carry out an ICMP ECHO ping sweep to find stay hosts from a spread of goal IP addresses. Run nmap -sn -PE [Target Range of IP Addresses] command (right here, the goal vary of IP addresses is 10.10.1.10-23). The scan outcomes seem, indicating the goal Host is up, as proven within the screenshot.
On this lab process, we’re scanning Home windows 11, Home windows Server 2022, Home windows Server 2019, and Android machines. If Android machine is down, navigate to the Sources tab and choose Android. Click on Energy and Show icon from the highest part of the web page, from the drop-down choices, choose Reset/Reboot and click on Sure.
The ICMP ECHO ping sweep is used to find out the stay hosts from a spread of IP addresses by sending ICMP ECHO requests to a number of hosts. If a bunch is alive, it’ll return an ICMP ECHO reply.
Run nmap -sn -PP [Target IP Address] command, (right here, the goal IP handle is 10.10.1.22). The scan outcomes seem, indicating the goal Host is up, as proven within the screenshot.
-PP: performs the ICMP timestamp ping scan.
ICMP timestamp ping is an non-obligatory and extra kind of ICMP ping whereby the attackers question a timestamp message to amass the data associated to the present time from the goal host machine.
Aside from the aforementioned community scanning methods, you may as well use the next scanning methods to carry out a bunch discovery on a goal community.
-
ICMP Handle Masks Ping Scan: This system is an alternate for the standard ICMP ECHO ping scan, that are used to find out whether or not the goal host is stay particularly when directors block the ICMP ECHO pings.
# nmap -sn -PM [target IP address]
-
TCP SYN Ping Scan: This system sends empty TCP SYN packets to the goal host, ACK response signifies that the host is lively.
# nmap -sn -PS [target IP address]
-
TCP ACK Ping Scan: This system sends empty TCP ACK packets to the goal host; an RST response signifies that the host is lively.
# nmap -sn -PA [target IP address]
-
IP Protocol Ping Scan: This system sends totally different probe packets of various IP protocols to the goal host, any response from any probe signifies {that a} host is lively.
# nmap -sn -PO [target IP address]
===============================================================
Port scanning methods are categorized based on the kind of protocol used for communication inside the community.
- TCP Scanning
- Open TCP scanning strategies (TCP join/full open scan)
- Stealth TCP scanning strategies (Half-open Scan, Inverse TCP Flag Scan, ACK flag probe scan, third get together and spoofed TCP scanning strategies)
- UDP Scanning
- SCTP Scanning
- SCTP INIT Scanning
- SCTP COOKIE/ECHO Scanning
- SSDP and Checklist Scanning
- IPv6 Scanning
The Zenmap seems; within the Command discipline, kind nmap -sT -v [Target IP Address] (right here, the goal IP handle is 10.10.1.22) and click on Scan.
-sT: performs the TCP join/full open scan and -v: permits the verbose output (embody all hosts and ports within the output).
TCP join scan completes a three-way handshake with the goal machine. Within the TCP three-way handshake, the consumer sends a SYN packet, which the recipient acknowledges with the SYN+ACK packet. In flip, the consumer acknowledges the SYN+ACK packet with an ACK packet to finish the connection. As soon as the handshake is accomplished, the consumer sends an RST packet to finish the connection.
Click on the Ports/Hosts tab to assemble extra data on the scan outcomes. Nmap shows the Port, Protocol, State, Service, and Model of the scan.
Click on the Topology tab to view the topology of the goal community that incorporates the offered IP handle and click on the Fisheye choice to view the topology clearly.
-
On this sub-task, we will be performing a stealth scan/TCP half-open scan, Xmas scan, TCP Maimon scan, and ACK flag probe scan on a firewall-enabled machine (i.e., Home windows Server 2022) so as to observe the consequence. To do that, we have to allow Home windows Firewall within the Home windows Server 2022 machine.
-
Within the Command discipline of Zenmap, kind nmap -sS -v [Target IP Address] (right here, the goal IP handle is 10.10.1.22) and click on Scan.
-sS: performs the stealth scan/TCP half-open scan and -v: permits the verbose output (embody all hosts and ports within the output).
The stealth scan entails resetting the TCP connection between the consumer and server abruptly earlier than completion of three-way handshake alerts, and therefore leaving the connection half-open. This scanning approach can be utilized to bypass firewall guidelines, logging mechanisms, and conceal underneath community visitors.
Equally, kind nmap -sX -v [Target IP Address] (right here, the goal IP handle is 10.10.1.22) and click on Scan.
-sX: performs the Xmas scan and -v: permits the verbose output (embody all hosts and ports within the output).
Xmas scan sends a TCP body to a goal system with FIN, URG, and PUSH flags set. If the goal has opened the port, then you’ll obtain no response from the goal system. If the goal has closed the port, then you’ll obtain a goal system reply with an RST.
-
Within the Command discipline of Zenmap, kind nmap -sU -v [Target IP Address] (right here, the goal IP handle is 10.10.1.22) and click on Scan.
-sU: performs the UDP scan and -v: permits the verbose output (embody all hosts and ports within the output). This scan may take roughly 15-20 minutes.
-
The scan outcomes seem, displaying all open UDP ports and companies operating on the goal machine, as proven within the screenshot.
This scan will take roughly 20 minutes to complete the scanning course of and the outcomes would possibly differ in your lab atmosphere.
The UDP scan makes use of UDP protocol as a substitute of the TCP. There isn’t any three-way handshake for the UDP scan. It sends UDP packets to the goal host; no response signifies that the port is open. If the port is closed, an ICMP port unreachable message is obtained.
-
Aside from the aforementioned port scanning and repair discovery methods, you may as well use the next scanning methods to carry out a port and repair discovery on a goal community utilizing Nmap.
-
IDLE/IPID Header Scan: A TCP port scan methodology that can be utilized to ship a spoofed supply handle to a pc to find what companies can be found.
# nmap -sI -v [target IP address]
-
SCTP INIT Scan: An INIT chunk is shipped to the goal host; an INIT+ACK chunk response implies that the port is open, and an ABORT Chunk response signifies that the port is closed.
# nmap -sY -v [target IP address]
-
SCTP COOKIE ECHO Scan: A COOKIE ECHO chunk is shipped to the goal host; no response implies that the port is open and ABORT Chunk response signifies that the port is closed.
# nmap -sZ -v [target IP address]
-
-
Within the Command discipline, kind nmap -sV [Target IP Address] (right here, the goal IP handle is 10.10.1.22) and click on Scan.
-
-sV: detects service variations.
-
The scan outcomes seem, displaying that open ports and the model of companies operating on the ports, as proven within the screenshot.
Service model detection lets you get hold of details about the operating companies and their variations on a goal system. Acquiring an correct service model quantity permits you to decide which exploits the goal system is weak to.
-
Within the Command discipline, kind nmap -A [Target Subnet] (right here, goal subnet is 10.10.1.* ) and click on Scan. By offering the “*” (asterisk) wildcard, you may scan a complete subnet or IP vary.
-A: permits aggressive scan. The aggressive scan choice helps OS detection (-O), model scanning (-sV), script scanning (-sC), and traceroute (–traceroute). You shouldn’t use -A in opposition to goal networks with out permission.
-
Nmap scans the complete community and shows data for all of the hosts that had been scanned, together with the open ports and companies, system kind, particulars of OS, and so on.
===================================================================
Overview of OS Discovery/ Banner Grabbing
Banner grabbing, or OS fingerprinting, is a technique used to find out the OS that’s operating on a distant goal system.
There are two sorts of OS discovery or banner grabbing methods:
-
Lively Banner Grabbing Specifically crafted packets are despatched to the distant OS, and the responses are famous, that are then in contrast with a database to find out the OS. Responses from totally different OSes range, due to variations within the TCP/IP stack implementation.
-
Passive Banner Grabbing This will depend on the differential implementation of the stack and the varied methods an OS responds to packets. Passive banner grabbing contains banner grabbing from error messages, sniffing the community visitors, and banner grabbing from web page extensions.
Parameters reminiscent of TTL and TCP window dimension within the IP header of the primary packet in a TCP session performs an vital position in figuring out the OS operating on the goal machine. The TTL discipline determines the utmost time a packet can stay in a community, and the TCP window dimension determines the size of the packet reported. These values differ for various OSes: you may seek advice from the next desk to study the TTL values and TCP window dimension related to varied OSes.
run nmap -O [Target IP Address] command (right here, the goal machine is Home windows Server 2022 [10.10.1.22]). The scan outcomes seem, displaying details about open ports, respective companies operating on the open ports, and the identify of the OS operating on the goal system.
-O: performs the OS discovery.
Within the terminal window, run nmap –script smb-os-discovery.nse [Target IP Address] command (right here, the goal machine is Home windows Server 2022 [10.10.1.22]). The scan outcomes seem, displaying the goal OS, pc identify, NetBIOS pc identify, and so on. particulars underneath the Host script outcomes part.
–script: specifies the personalized script and smb-os-discovery.nse: makes an attempt to find out the OS, pc identify, area, workgroup, and present time over the SMB protocol (ports 445 or 139).
=======================================================================
An Intrusion Detection System (IDS) and firewall are the safety mechanisms supposed to forestall an unauthorized particular person from accessing a community. Nonetheless, even IDSs and firewalls have some safety limitations. Firewalls and IDSs intend to keep away from malicious visitors (packets) from coming into right into a community, however sure methods can be utilized to ship supposed packets to the goal and evade IDSs/firewalls.
Methods to evade IDS/firewall:
- Packet Fragmentation: Ship fragmented probe packets to the supposed goal, which re-assembles it after receiving all of the fragments
- Supply Routing: Specifies the routing path for the malformed packet to succeed in the supposed goal
- Supply Port Manipulation: Manipulate the precise supply port with the widespread supply port to evade IDS/firewall
- IP Handle Decoy: Generate or manually specify IP addresses of the decoys in order that the IDS/firewall can’t decide the precise IP handle
- IP Handle Spoofing: Change supply IP addresses in order that the assault seems to be coming in as another person
- Creating Customized Packets: Ship customized packets to scan the supposed goal past the firewalls
- Randomizing Host Order: Scan the variety of hosts within the goal community in a random order to scan the supposed goal that’s mendacity past the firewall
- Sending Dangerous Checksums: Ship the packets with dangerous or bogus TCP/UDP checksums to the supposed goal
- Proxy Servers: Use a sequence of proxy servers to cover the precise supply of a scan and evade sure IDS/firewall restrictions
- Anonymizers: Use anonymizers that enable them to bypass Web censors and evade sure IDS and firewall guidelines
Nmap affords many options to assist perceive advanced networks with enabled safety mechanisms and helps mechanisms for bypassing poorly applied defenses. Utilizing Nmap, varied methods might be applied, which might bypass the IDS/firewall safety mechanisms.
n the terminal window, run nmap -f [Target IP Address] command, (right here, the goal machine is Home windows 11 [10.10.1.11]).
-f change is used to separate the IP packet into tiny fragment packets.
Packet fragmentation refers back to the splitting of a probe packet into a number of smaller packets (fragments) whereas sending it to a community. When these packets attain a bunch, IDSs and firewalls behind the host typically queue all of them and course of them one after the other. Nonetheless, since this methodology of processing entails better CPU consumption in addition to community assets, the configuration of most of IDSs makes it skip fragmented packets throughout port scans.
-
Within the Parrot Terminal window, run nmap -g 80 [Target IP Address] command, (right here, goal IP handle is 10.10.1.11).
On this command, you should utilize the -g or –source-port choice to carry out supply port manipulation.
Supply port manipulation refers to manipulating precise port numbers with widespread port numbers to evade IDS/firewall: that is helpful when the firewall is configured to permit packets from well-known ports like HTTP, DNS, FTP, and so on.
-
The outcomes seem, displaying all open TCP ports together with the identify of companies operating on the ports, as proven within the screenshot.
Now, run nmap -mtu 8 [Target IP Address] command (right here, goal IP handle is 10.10.1.11).
On this command, -mtu: specifies the variety of Most Transmission Unit (MTU) (right here, 8 bytes of packets).
Utilizing MTU, smaller packets are transmitted as a substitute of sending one full packet at a time. This system evades the filtering and detection mechanism enabled within the goal machine.
Within the Wireshark window, scroll-down and you may observe the fragmented packets having most size as 8 bytes, as proven within the screenshot.
Now, run nmap -D RND:10 [Target IP Address] command (right here, goal IP handle is 10.10.1.11).
On this command, -D: performs a decoy scan and RND: generates a random and non-reserved IP addresses (right here, 10).
The IP handle decoy approach refers to producing or manually specifying IP addresses of the decoys to evade IDS/firewall. This system makes it tough for the IDS/firewall to find out which IP handle was really scanning the community and which IP addresses had been decoys. Through the use of this command, Nmap mechanically generates a random variety of decoys for the scan and randomly positions the true IP handle between the decoy IP addresses.
Within the Wireshark window, scroll-down and you may observe the packets displaying the a number of IP addresses within the supply part, as proven within the screenshot.
Within the terminal window, run nmap -sT -Pn –spoof-mac 0 [Target IP Address] command (right here, goal IP handle is 10.10.1.11).
On this command –spoof-mac 0 represents randomizing the MAC handle, -sT: performs the TCP join/full open scan, -Pn is used to skip the host discovery.
MAC handle spoofing approach entails spoofing a MAC handle with the MAC handle of a professional person on the community. This system permits you to ship request packets to the focused machine/community pretending to be a professional host.
=======================================================================
Scanning instruments are used to scan and establish stay hosts, open ports, operating companies on a goal community, location-info, NetBIOS information, and details about all TCP/IP and UDP open ports. Info obtained from these instruments will help an moral hacker in creating the profile of the goal group and to scan the community for open ports of the units related.
Metasploit Framework is a software that gives details about safety vulnerabilities within the goal group’s system, and aids in penetration testing and IDS signature growth. It facilitates the duties of attackers, exploit writers, and payload writers. A serious benefit of the framework is the modular method, that’s, permitting the mixture of any exploit with any payload.
Execute command msfconsole to launch Metasploit.
-
An msf command line seems. Sort nmap -Pn -sS -A -oX Take a look at 10.10.1.0/24 and press Enter to scan the subnet, as proven within the screenshot.
Right here, we’re scanning the entire subnet 10.10.1.0/24 for lively hosts.
-
Nmap begins scanning the subnet and shows the outcomes. It takes roughly 5 minutes for the scan to finish.
Sort search portscan and press Enter. The Metasploit port scanning modules seem, as proven within the screenshot.
-
Right here, we’ll use the auxiliary/scanner/portscan/syn module to carry out an SYN scan on the goal programs. To take action, kind use auxiliary/scanner/portscan/syn and hit Enter.
-
We’ll use this module to carry out an SYN scan in opposition to the goal IP handle vary (10.10.1.5-23) to search for open port 80 via the eth0 interface.
To take action, difficulty the beneath instructions:
- set INTERFACE eth0
- set PORTS 80
- set RHOSTS 10.10.1.5-23
- set THREADS 50
PORTS: specifies the ports to scan (e.g., 22-25, 80, 110-900), RHOSTS: specifies the goal handle vary or CIDR identifier, and THREADS: specifies the variety of concurrent threads (default 1).
-
After specifying the above values, kind run and press Enter, to provoke the scan in opposition to the goal IP handle vary.
Equally, you may as well specify a spread of ports to be scanned in opposition to the goal IP handle vary.
-
Now, we’ll carry out a TCP scan for open ports on the goal programs.
-
To load the auxiliary/scanner/portscan/tcp module, kind use auxiliary/scanner/portscan/tcp and press Enter. Run present choices command to view module choices.
-
Sort set RHOSTS [Target IP Address] and press Enter.
Right here, we’ll carry out a TCP scan for open ports on a single IP handle (10.10.1.22), as scanning a number of IP addresses consumes a lot time.
-
Sort run and press Enter to find open TCP ports within the goal system.
It should take roughly 20 minutes for the scan to finish.
The outcomes seem, displaying all open TCP ports within the goal IP handle (10.10.1.22).
You may additional discover varied modules of Metasploit reminiscent of FTP module to establish the FTP model operating within the goal host.This data can additional be used to carry out vulnerability evaluation on the open companies found within the goal hosts.
=============================================================
Community scanning utilizing AI enhances cybersecurity by automating the detection of vulnerabilities and threats. AI-driven instruments analyze community visitors, establish anomalies, and predict potential assaults with excessive accuracy, offering proactive protection mechanisms and decreasing response instances for cybersecurity groups.
ShellGPT is an AI-powered software that may help in scanning networks by automating duties reminiscent of figuring out lively units, detecting open ports, and analyzing community vulnerabilities. It leverages superior algorithms to offer environment friendly, real-time insights, making certain community safety and efficiency optimization.
Right here, we’ll use ShellGPT to find lively hosts, open ports, companies operating, and OS particulars of programs current within the goal community.
The instructions generated by ShellGPT might range relying on the immediate used and the instruments obtainable on the machine. As a result of these variables, the output generated by ShellGPT would possibly differ from what’s proven within the screenshots. These variations come up from the dynamic nature of the AI’s processing and the various environments wherein it operates. In consequence, chances are you’ll observe variations in command syntax, execution, and outcomes whereas performing this lab process.
-
After incorporating the ShellGPT API in Parrot Safety Machine, within the terminal window run sgpt –chat scan –shell “Use hping3 to carry out ICMP scanning on the goal IP handle 10.10.1.11 and cease after 10 iterations” to carry out ICMP scan heading in the right direction IP handle.
Within the immediate kind E and press Enter to execute the command.
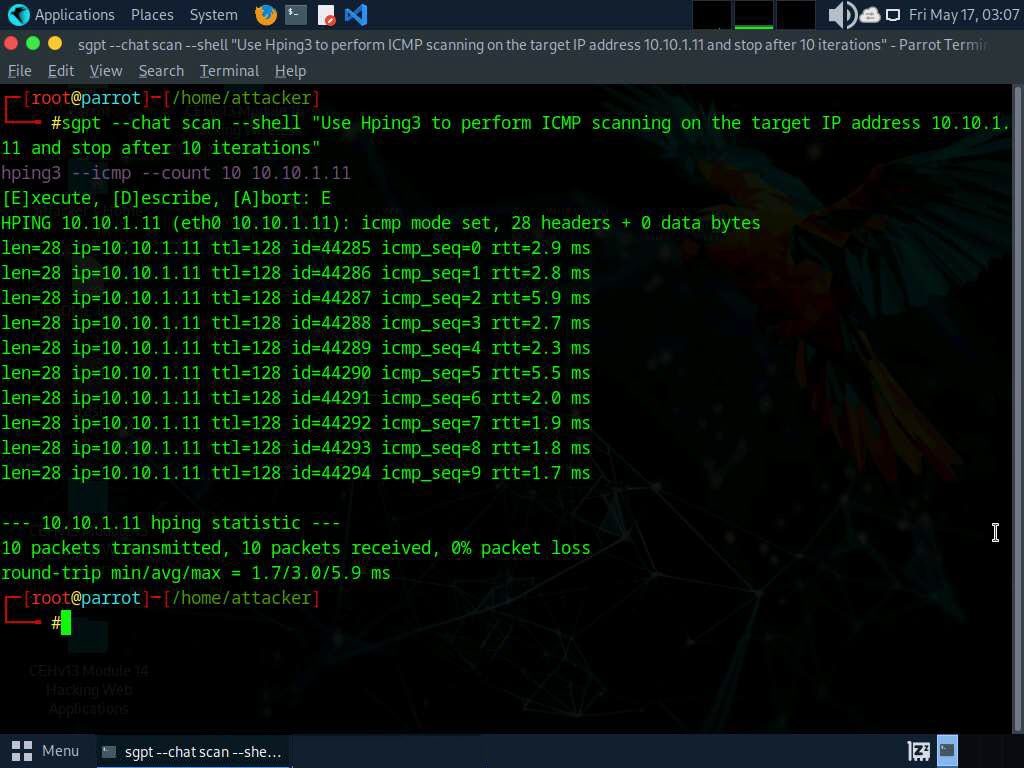
-
Now, run sgpt –chat scan –shell “Run a hping3 ACK scan on port 80 of goal IP 10.10.1.11” command to carry out ACK scan heading in the right direction IP handle.
Within the immediate kind E and press Enter to execute the command.
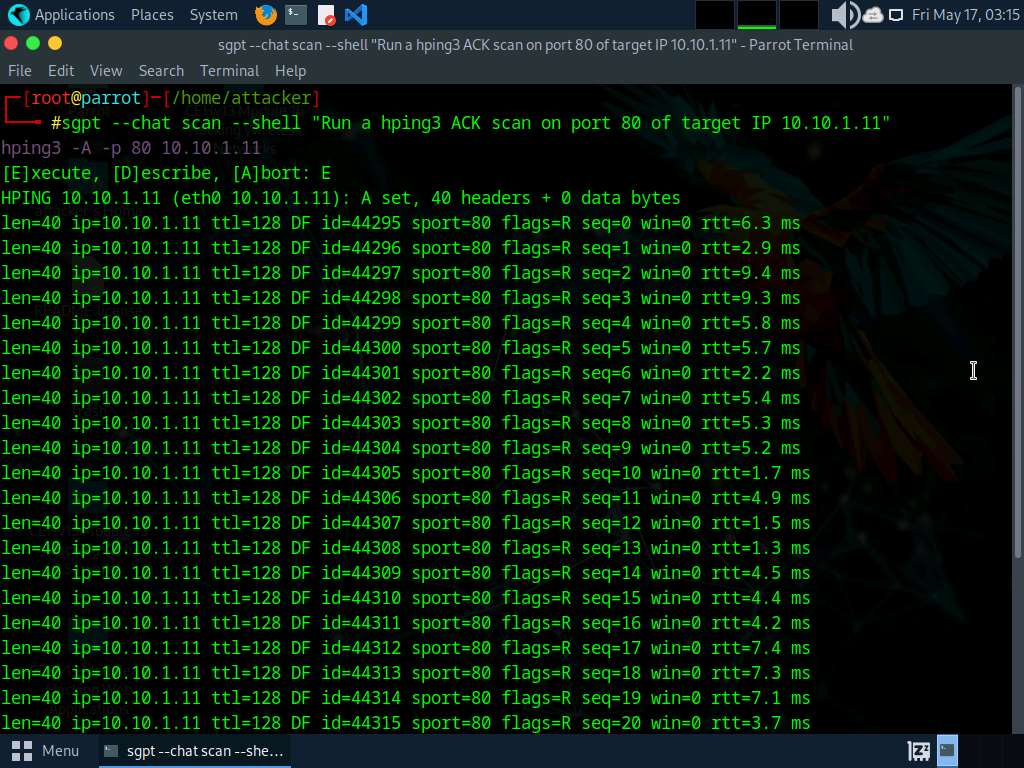
-
Press Ctrl + C to cease the scan.
-
Run sgpt –chat scan –shell “Scan the goal community 10.10.1.0/24 for lively hosts and place solely the IP addresses right into a file scan1.txt” to carry out host discovery.
Within the immediate kind E and press Enter to execute the command.
-
Now run pluma scan1.txt command to open scan1.txt file and think about the IP addresses of lively hosts within the goal subnet.
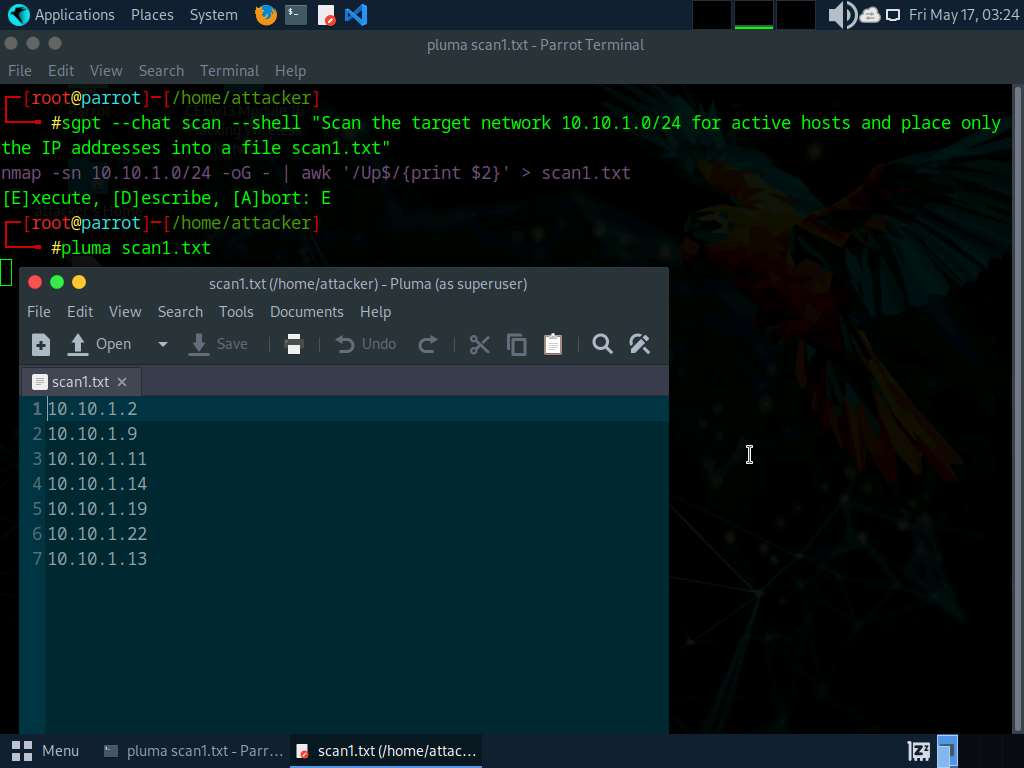
-
Shut the textual content editor window.
-
To carry out nmap scan in opposition to the IP addresses that had been gathered in earlier step run sgpt –chat scan –shell “Run a quick however complete nmap scan in opposition to scan1.txt with low verbosity and write the outcomes to scan2.txt” command.
Within the immediate kind E and press Enter to execute the command.
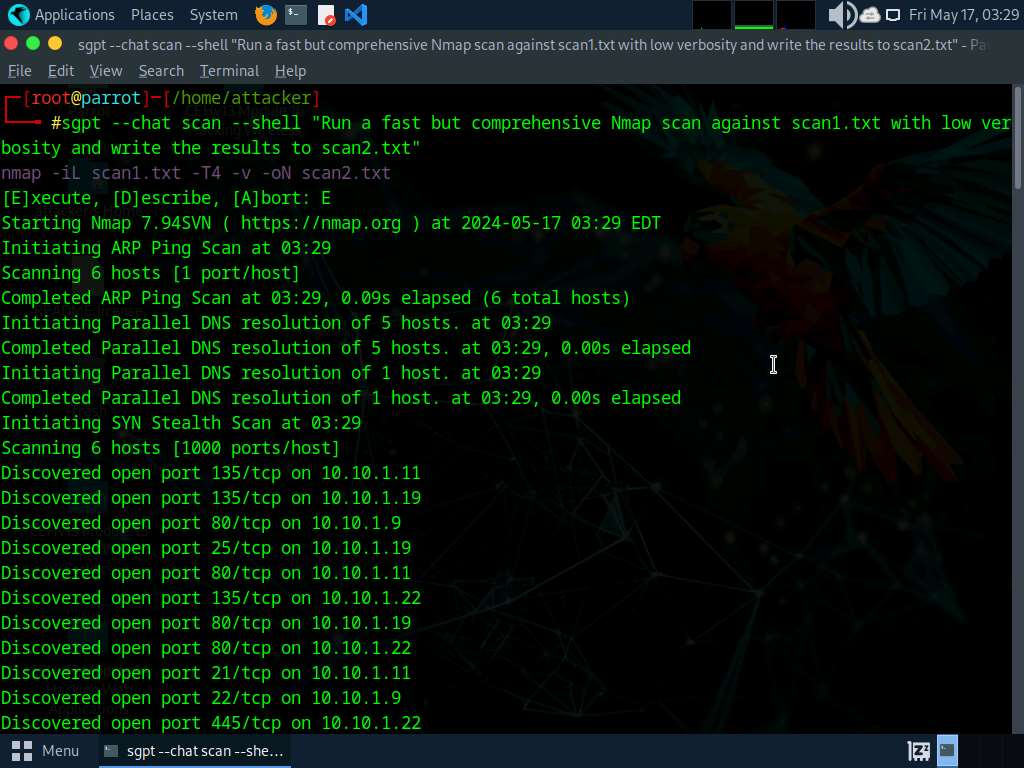
-
After the scan run pluma scan2.txt command to open scan2.txt file and think about the scan outcomes.
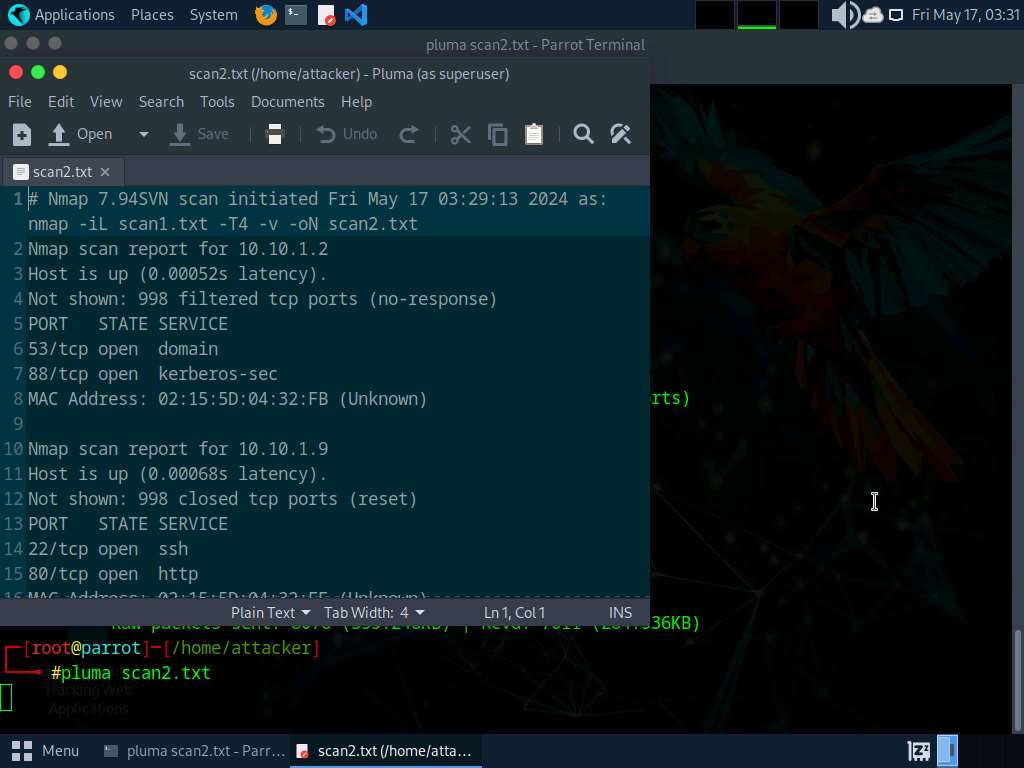
-
Shut the textual content editor window.
-
Run sgpt –chat scan –shell “Use nmap to carry out ICMP ECHO ping sweep on the goal community 10.10.1.0/24” command to carry out ICMP ECHO ping sweep on the goal community.
Within the immediate kind E and press Enter to execute the command.
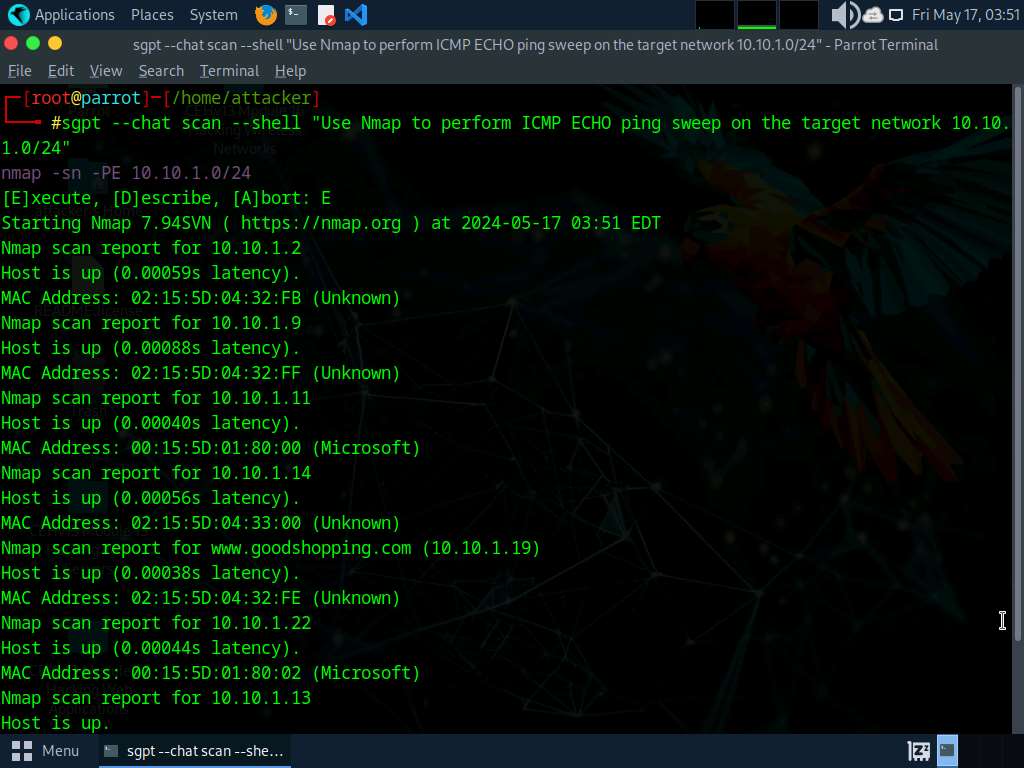
-
Now, we’ll carry out port scanning utilizing ShellGPT to take action, run sgpt –chat scan –shell “Use nmap to search out open ports heading in the right direction IP 10.10.1.11” command.
Within the immediate kind E and press Enter to execute the command.
-
The scan outcomes will seem displaying all of the open ports, pertaining to the goal IP handle.
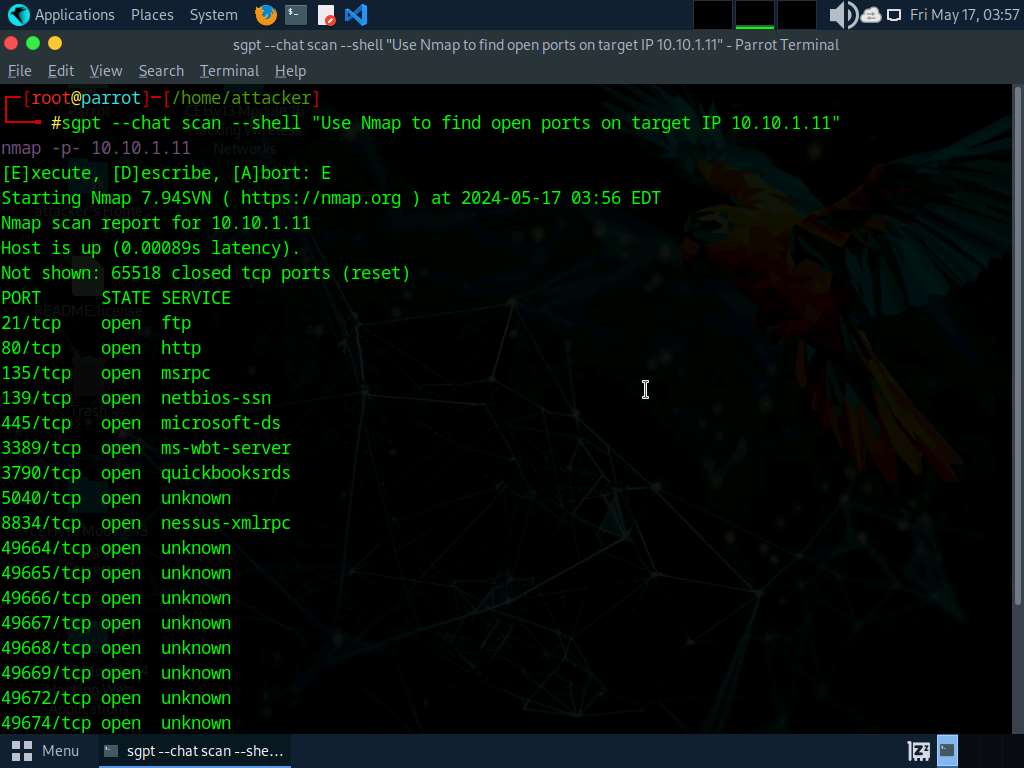
-
Now, we’ll carry out stealth scan on a goal IP, to take action, run sgpt –chat scan –shell “Carry out stealth scan heading in the right direction IP 10.10.1.11 and show the outcomes” command.
Within the immediate kind E and press Enter to execute the command.
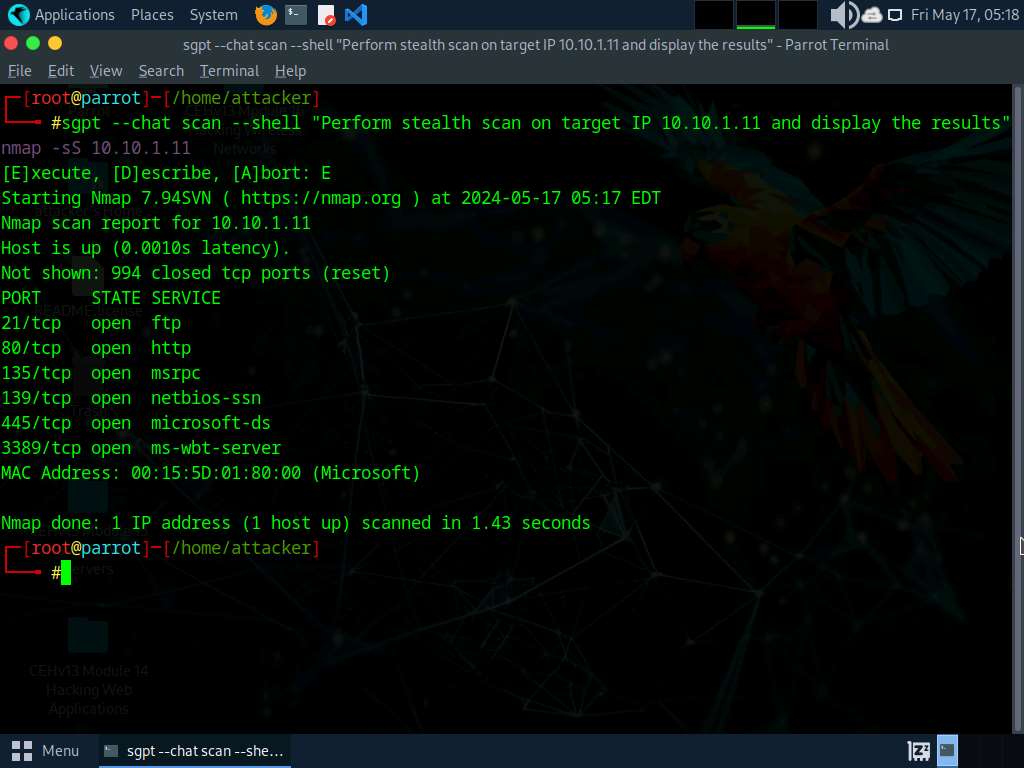
-
To carry out XMAS scan on a goal IP handle, run sgpt –chat scan –shell “Carry out an XMAS scan heading in the right direction IP 10.10.1.11” command.
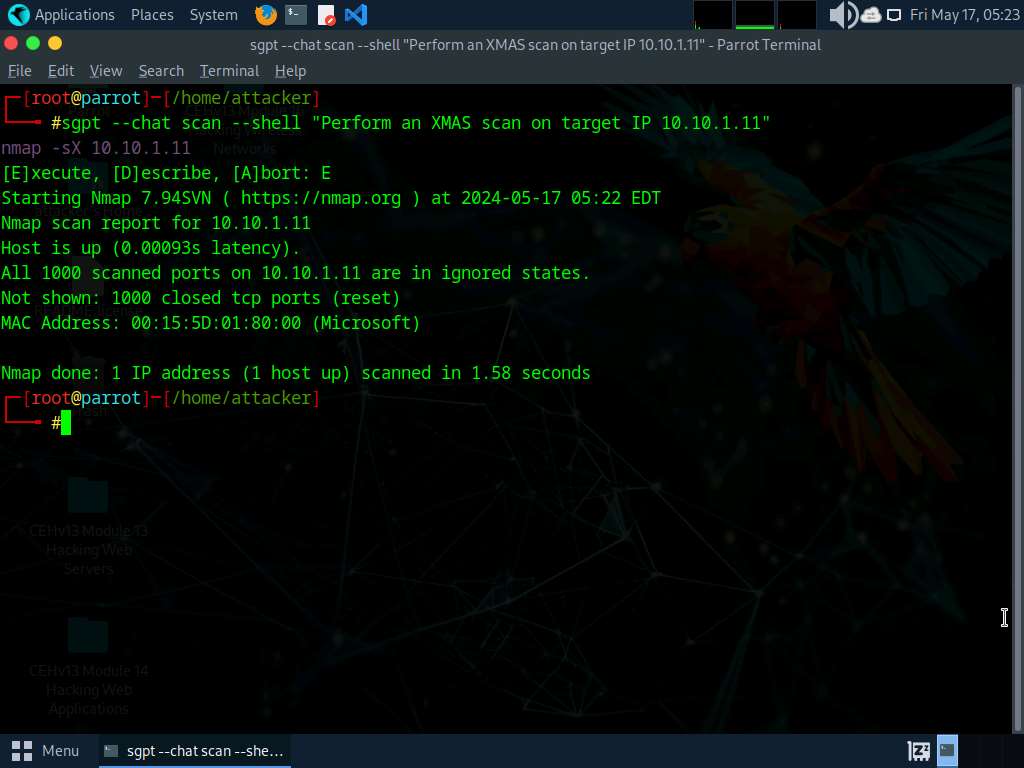
-
Run sgpt –chat scan –shell “Use Nmap to scan for open ports and companies in opposition to a listing of IP addresses in scan1.txt and duplicate solely the port, service and model data with the respective IP handle to a brand new file referred to as scan3.txt” command to scan for open companies and ports in opposition to the record of IP addresses acquired in Step#6.
Within the immediate kind E and press Enter to execute the command.
-
As soon as the scan is completed run pluma scan3.txt command to view the scan outcomes.
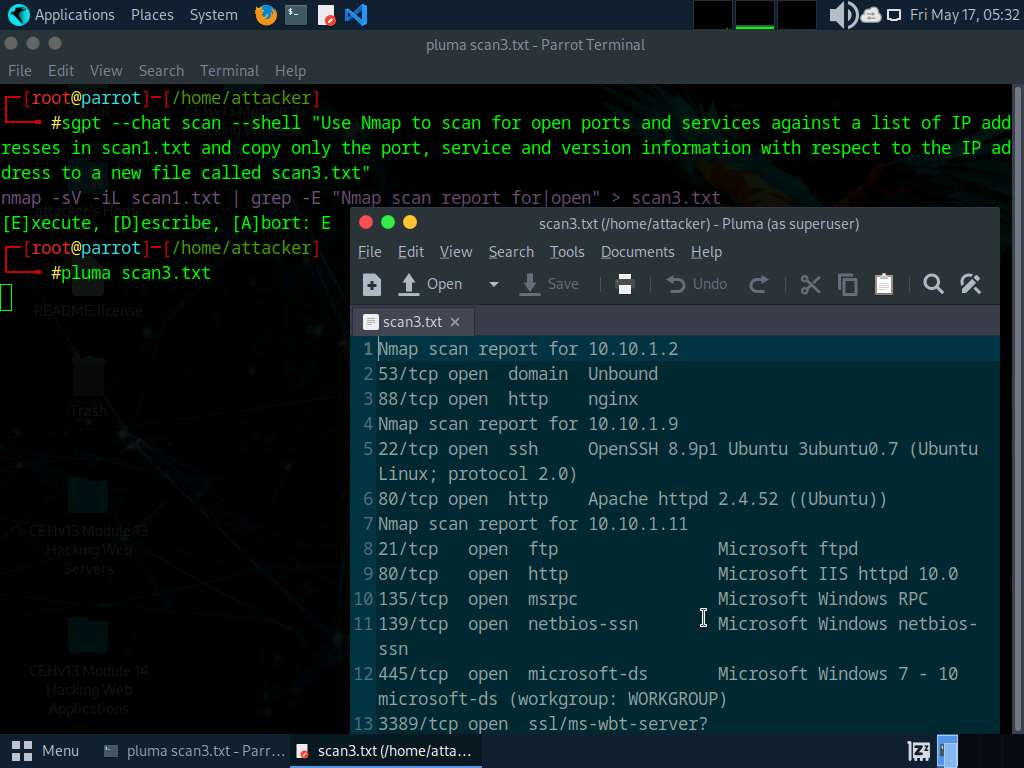
-
Shut the textual content editor window.
-
Now we’ll use Metasploit to find open ports on a goal system, run sgpt –chat scan –shell “Use Metasploit to find open ports on the IP handle 10.10.1.22” command.
Within the immediate kind E and press Enter to execute the command.
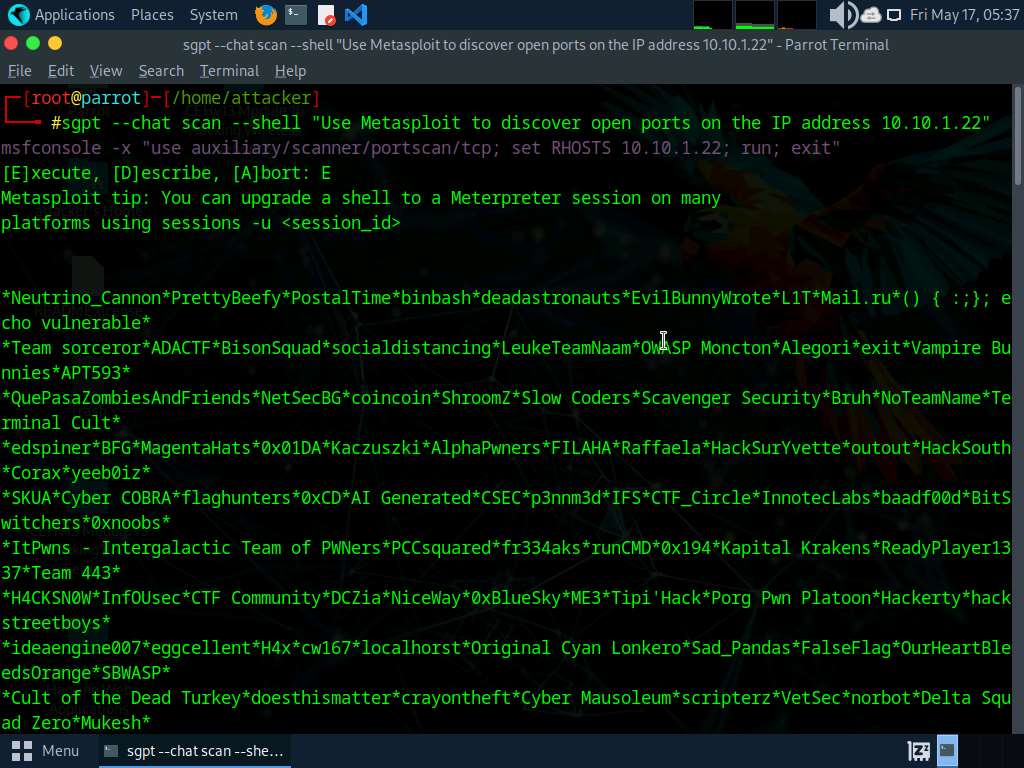
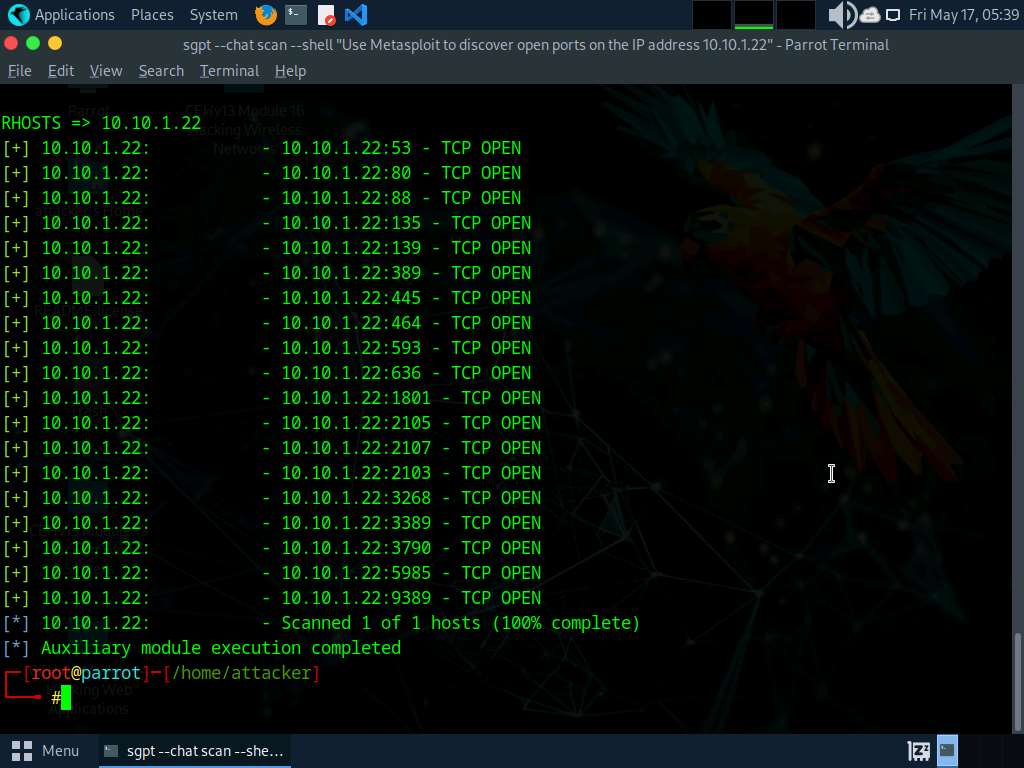
-
To carry out service model discovery on a goal system run sgpt –chat scan –shell “Use Nmap to scan open ports, MAC particulars, companies operating on open ports with their variations heading in the right direction IP 10.10.1.11” command.
Within the immediate kind E and press Enter to execute the command.
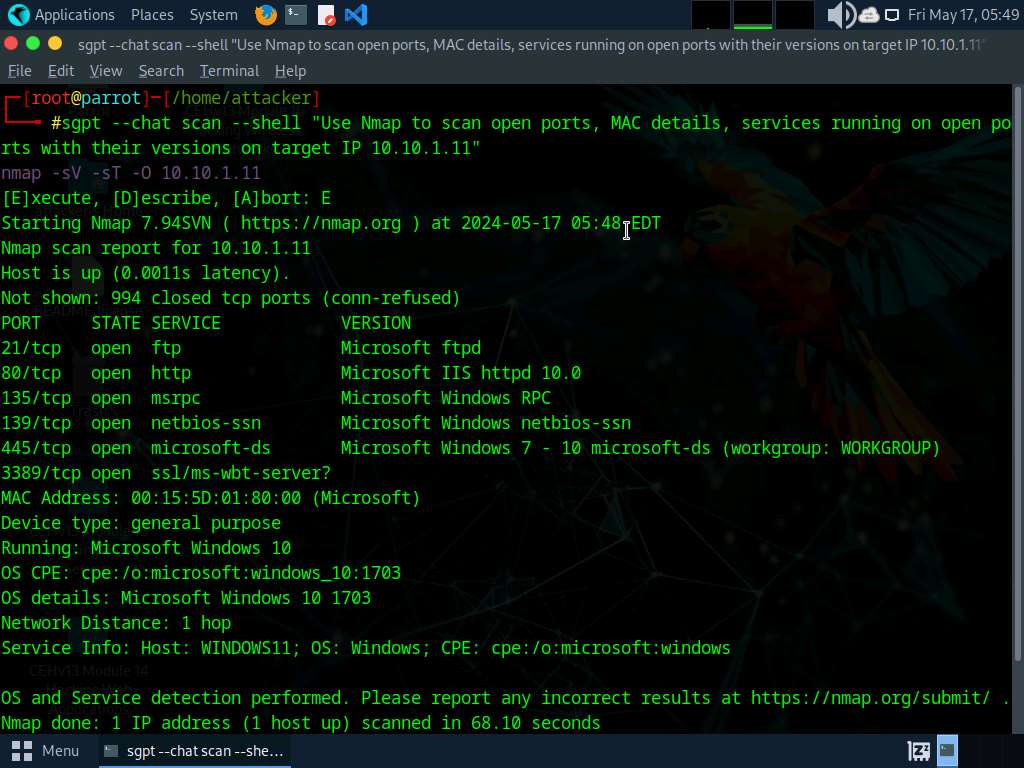
-
We’ll now carry out OS discovery utilizing ShellGPT, to take action run sgpt –chat scan –shell “Use TTL worth and establish the working system operating on the goal IP handle 10.10.1.11, show the TTL worth and OS” command.
Within the immediate kind E and press Enter to execute the command.
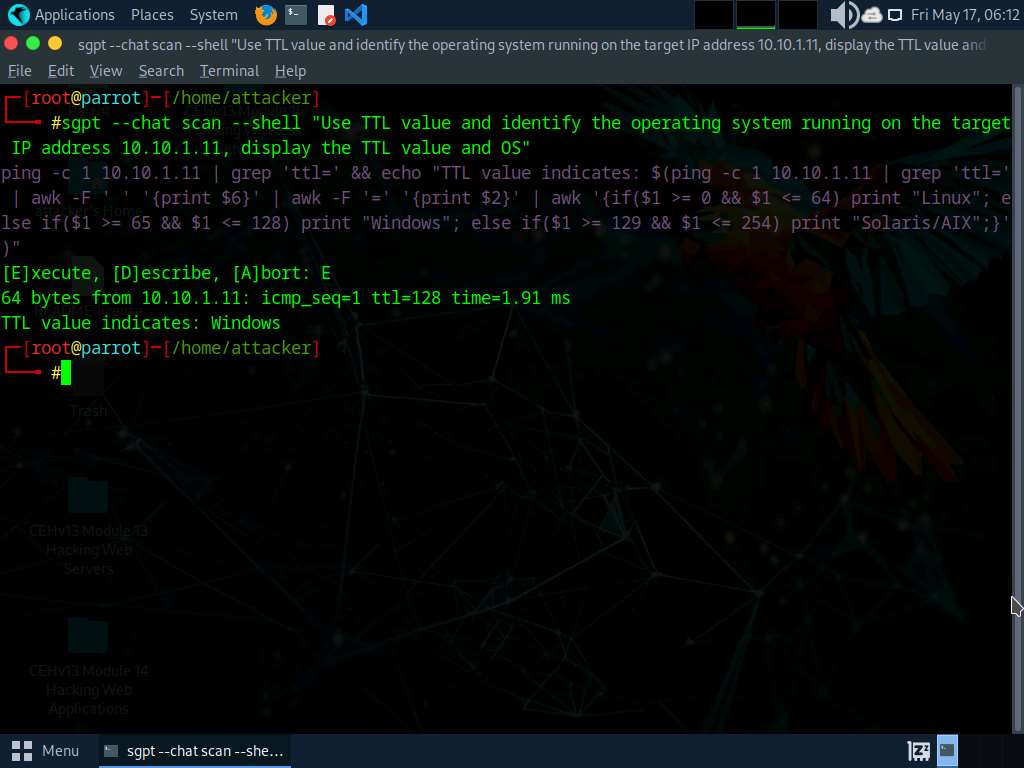
-
Run sgpt –chat scan –shell “Use TTL worth and establish the working system operating on the goal IP handle 10.10.1.9, show the TTL worth and OS”
Within the immediate kind E and press Enter to execute the command.
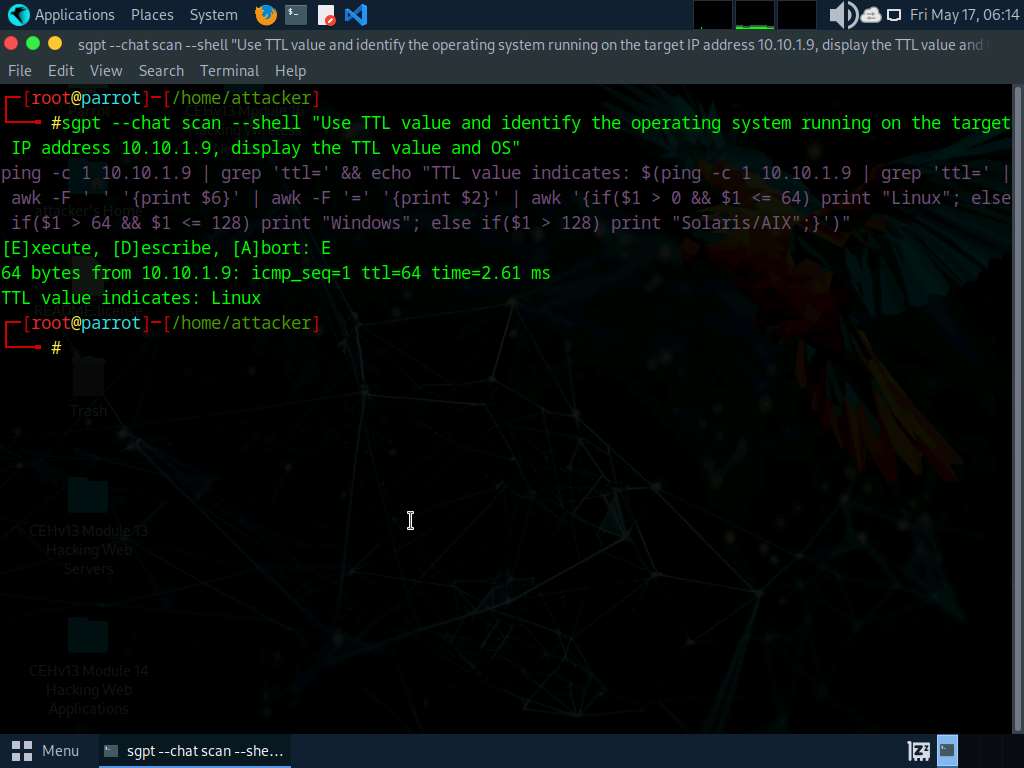
-
We’ll now carry out OS discovery utilizing Nmap on the record of IP addresses acquired in Step#6, to take action run sgpt –chat scan –shell “Use Nmap script engine to carry out OS discovery on the goal IP addresses in scan1.txt”
Within the immediate kind E and press Enter to execute the command.
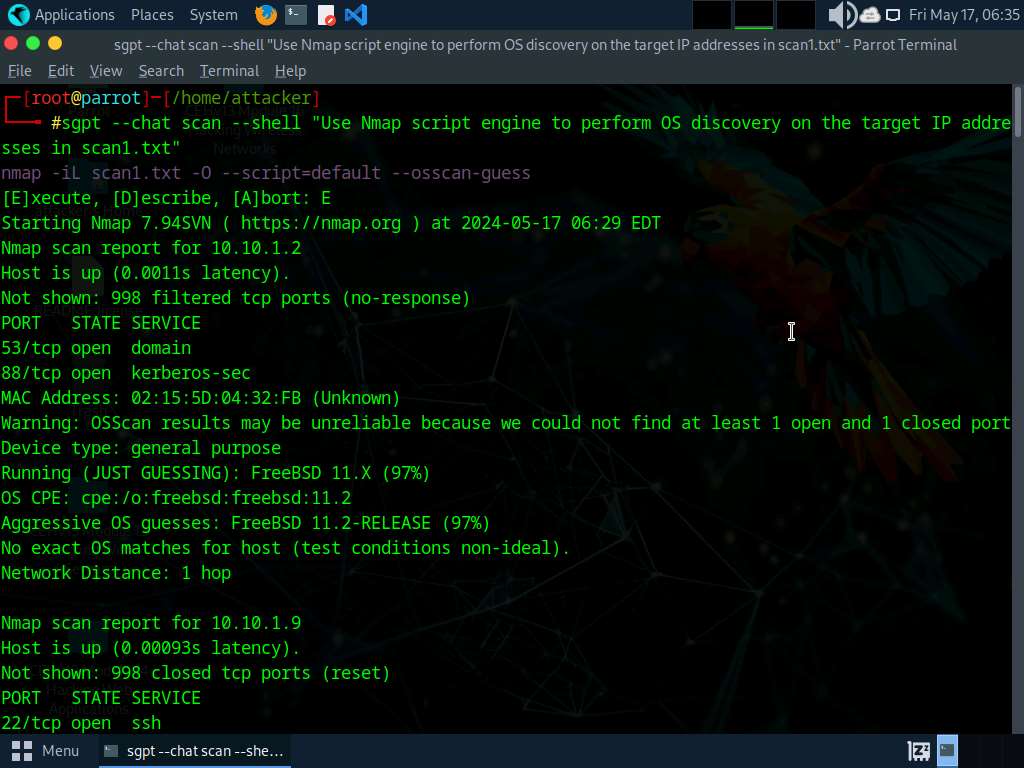
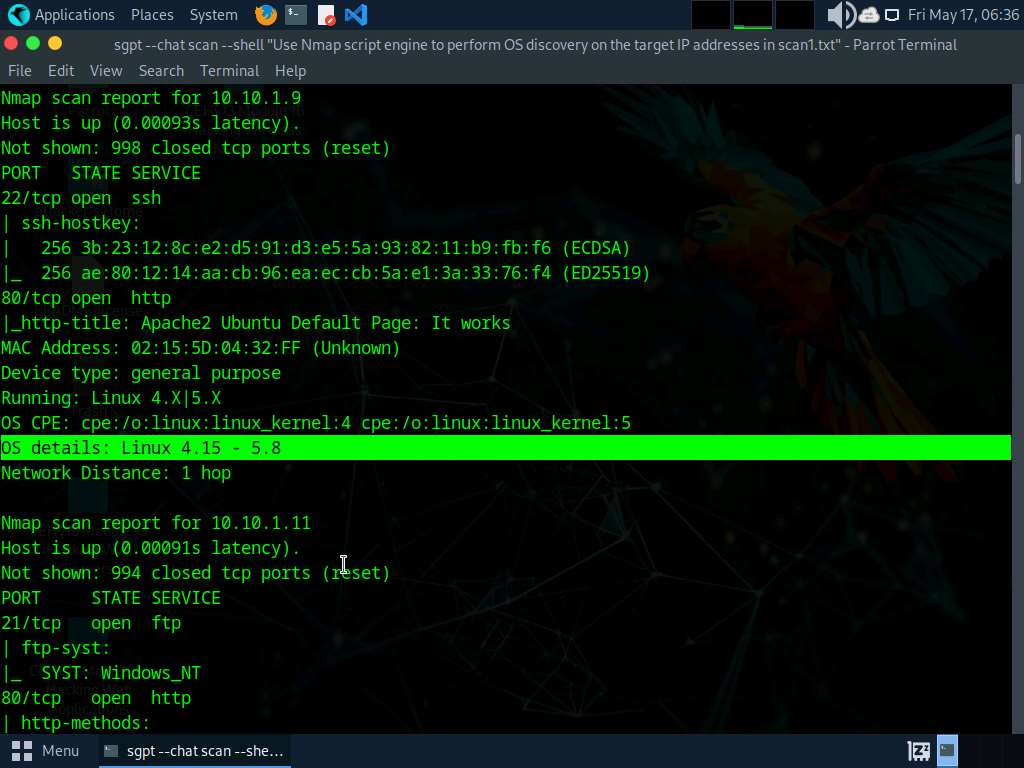
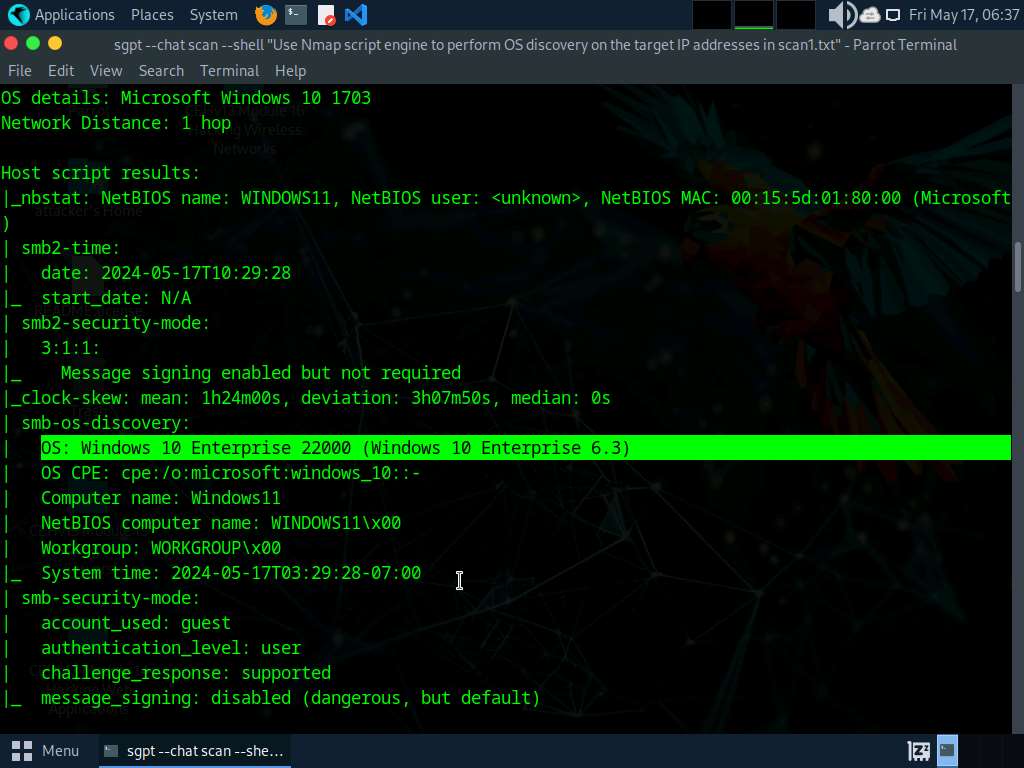
-
We’ll automate varied community scanning duties by create customized script that may run mechanically and fetch the specified consequence.
-
Within the terminal window run sgpt –chat scan –shell “Develop a script which can automate community scanning efforts and discover out stay programs, open ports, operating companies, service variations, and so on. heading in the right direction IP vary 10.10.1.0/24” command.
Within the immediate kind E and press Enter to execute the command.
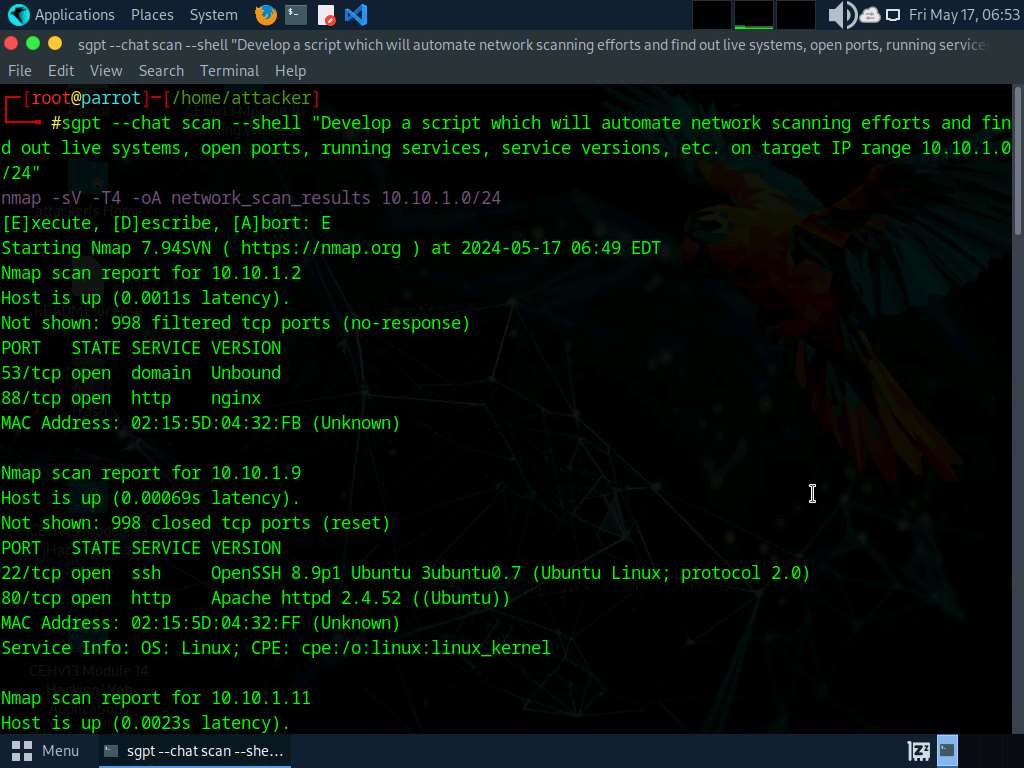
-
To make use of the IP Handle Decoy approach to scan run sgpt –chat scan –shell “To evade an IDS/Firewall, use IP handle decoy approach to scan the goal IP handle 10.10.1.22” command.
Within the immediate kind E and press Enter to execute the command.
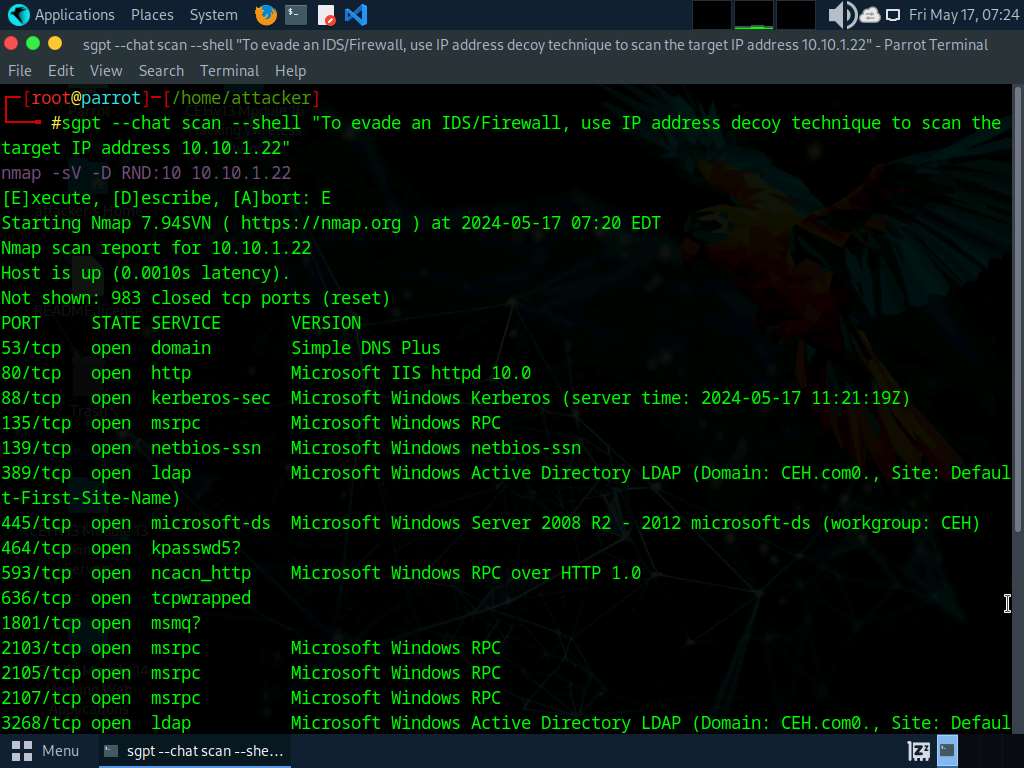
-
Now, run sgpt –chat scan –shell “Inside scan1.txt file take away 10.10.1.14 and 10.10.1.13 entries, then show outcomes” command to take away IP handle from scan1.txt file and show consequence.
Within the immediate kind E and press Enter to execute the command.
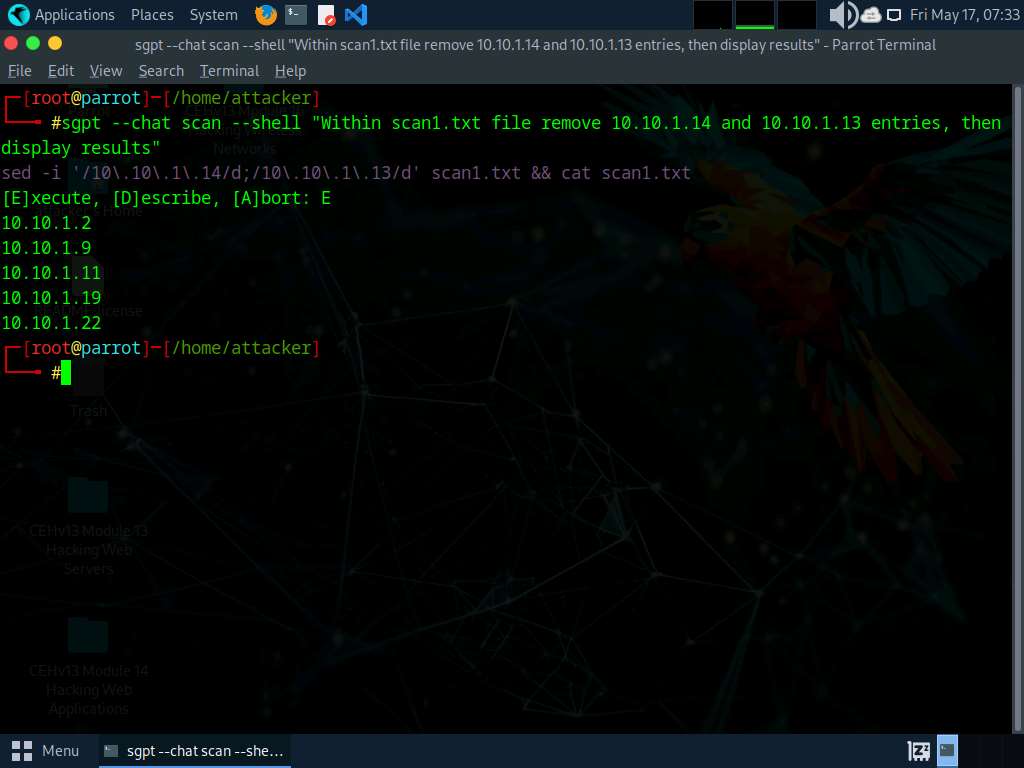
-
Run sgpt –chat scancode –code “Create a python script to run a quick however complete Nmap scan on the IP addresses in scan1.txt after which execute vulnerability scanning utilizing nikto in opposition to every IP handle in scan1.txt” command to create a python script which performs Nmap scan.
Within the immediate kind E and press Enter to execute the command.
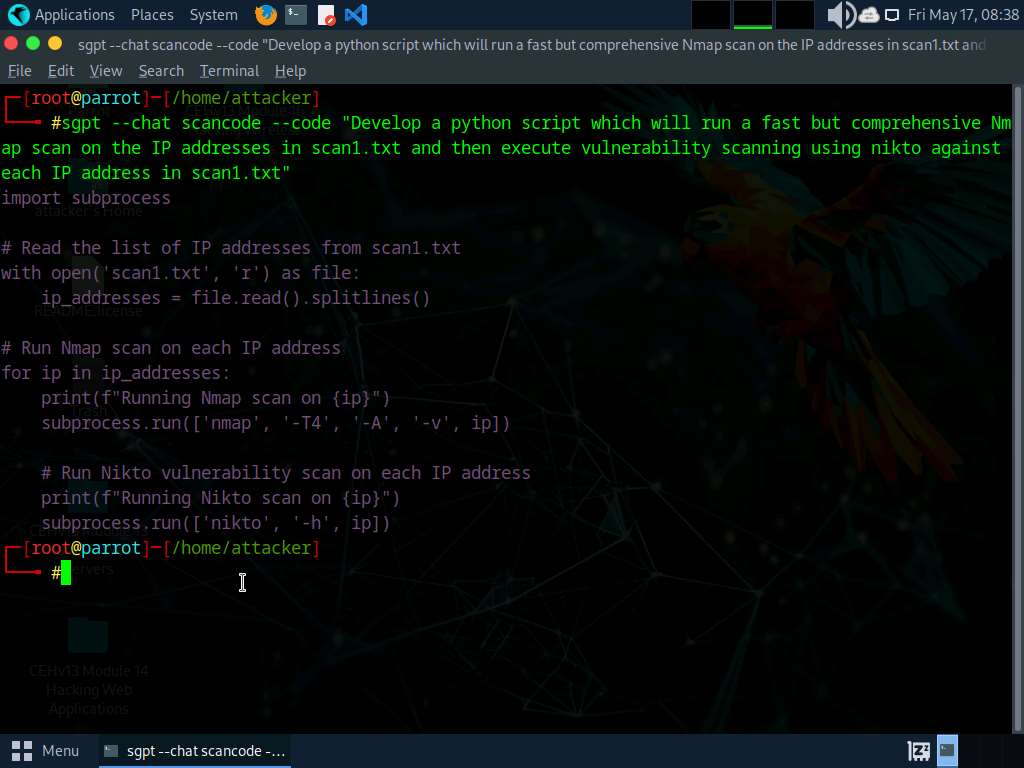
-
Now, copy the python code and sort pluma python_scan.py within the terminal. A Textual content editor window opens paste the code within the textual content editor window, save the file and shut it.
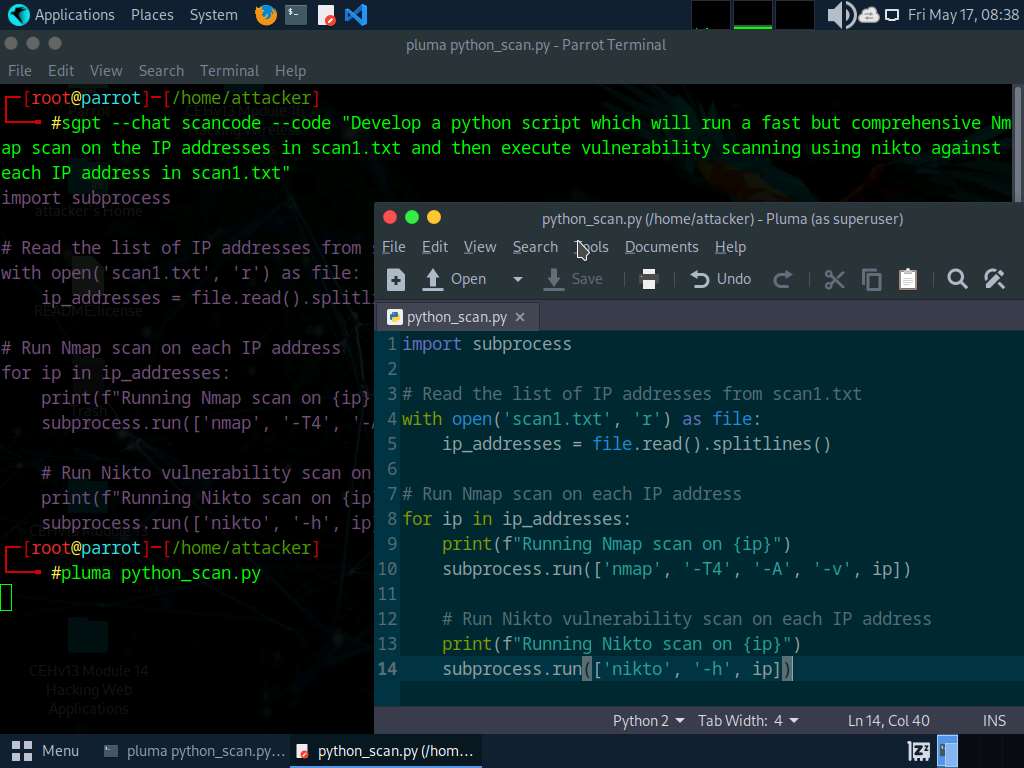
-
Now, within the terminal window, kind python3 python_scan.py to run the script.
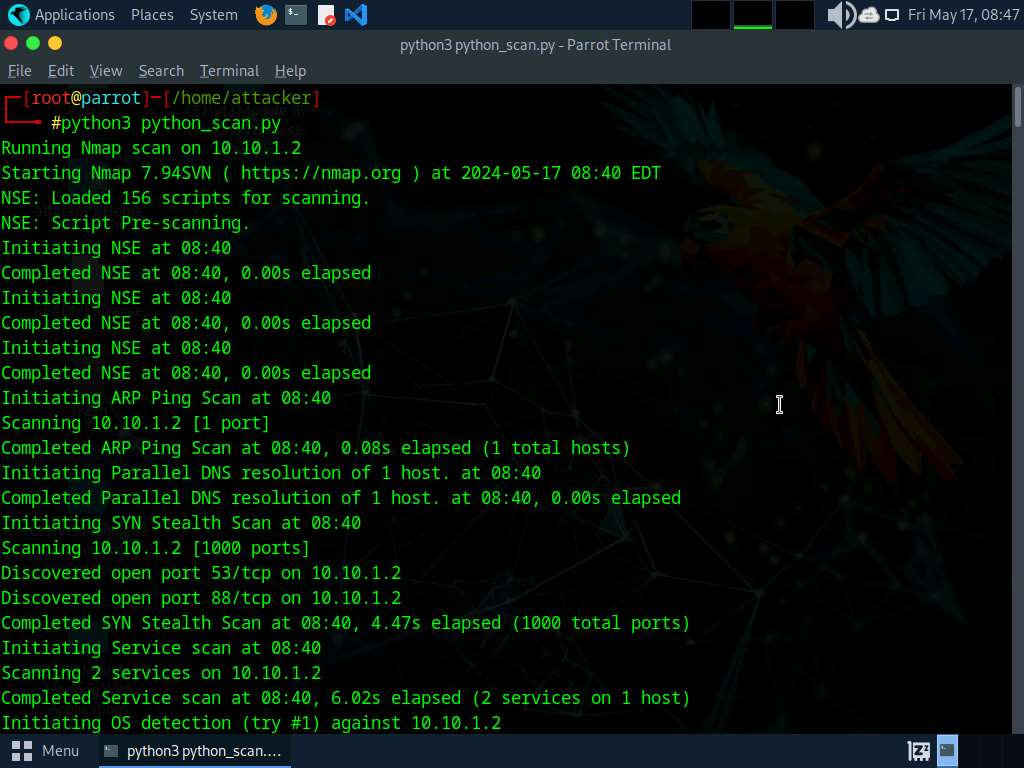
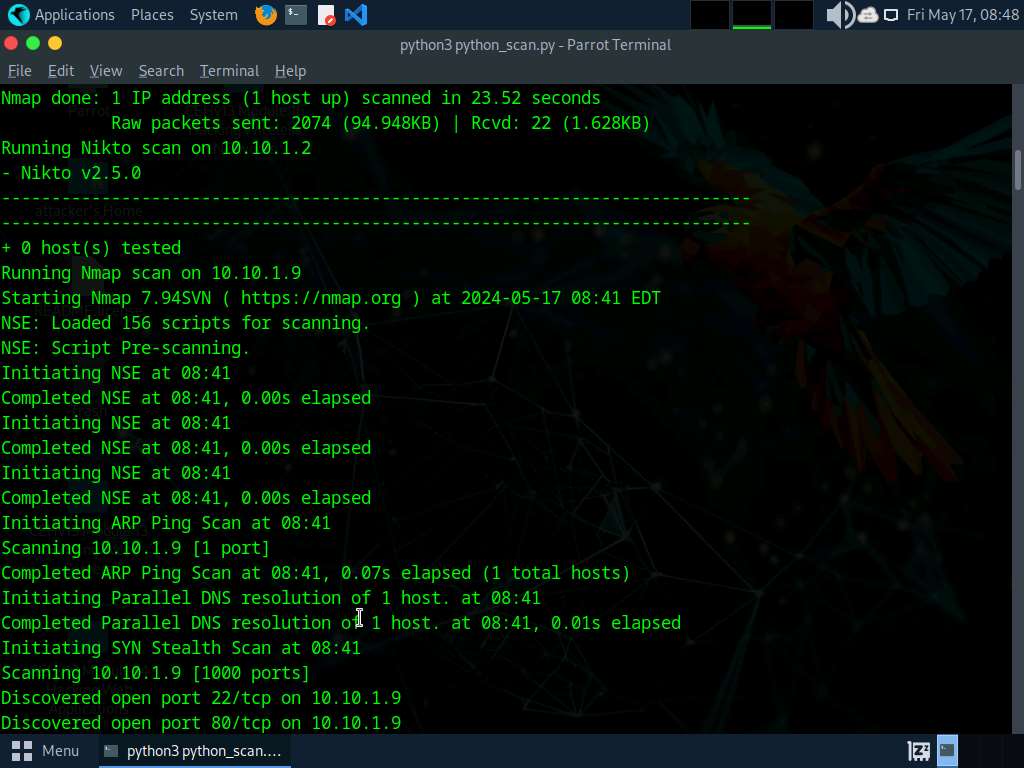
-
Aside from the aforementioned instructions, you may additional discover further choices inside the ShellGPT software and make the most of varied different instruments to conduct Community Scanning on the goal machine.










