Some employment scams take an surprising flip as cybercriminals shift from “hiring” to “firing” employees
18 Feb 2025
•
,
5 min. learn

Most of us are in a job or in search of one. Or each. That’s largely why employment and work-from-home scams are so widespread amongst cybercriminals (and even some state-aligned risk actors). The schemes sometimes lure the consumer by providing wonderful job or informal employment alternatives. However in actuality, all of the scammers often need is your private and monetary data. In some instances, victims could even find yourself unwittingly receiving and re-shipping stolen items, or permitting their financial institution accounts to be used for cash laundering.
Nonetheless, less-well identified is the employment termination rip-off. This turns the thought on its head: utilizing the specter of dropping your job quite than the lure of gaining a brand new one to catch your consideration. So what do they appear to be and how will you keep secure?
What do job termination scams appear to be?
At their easiest, job termination scams are a kind of phishing assault designed to trick you into handing over your private and monetary data, or on clicking on a malicious hyperlink which may set off a malware obtain. Social engineering techniques utilized in phishing intention to create a way of urgency within the sufferer, in order that they act with out considering issues by first. And you’ll’t get extra pressing than a discover informing you that you’ve been dismissed.
It may arrive within the type of an e mail from HR, or an authoritative third-party exterior the corporate. It could let you know that your companies are now not required. Or it might declare to embody particulars about your colleagues which can be too arduous to withstand studying. The top objective is to steer you to click on on a malicious hyperlink or open an attachment, maybe by claiming that it consists of particulars of severance funds and termination dates.
When you click on by/open the attachment, you would possibly discover that:
Along with your work logins, adversaries may hijack your e mail or different accounts to entry delicate company knowledge and networks for theft and extortion. And for those who reuse these logins throughout a number of accounts, they might even have the ability to run credential stuffing campaigns to unlock these accounts, too.
Why do they work so properly?
Termination scams are efficient as a result of they exploit the credulity of human beings, creating a way of dread among the many sufferer, and instilling an pressing want for motion. You’d be arduous pressed to search out an worker that didn’t wish to know extra about their very own termination, or probably contrived particulars of supposed misconduct.
It’s no coincidence that phishing stays a top-three preliminary entry tactic for ransomware actors and has contributed to 1 / 4 (25%) of financially motivated cyber-incidents over the previous two years.
Within the wild
A number of variations of this rip-off have been noticed circulating within the wild. These embody:
- An e mail impersonating the UK’s Courts & Tribunals Service, purporting to include a hyperlink to an employment termination doc. Clicking by hundreds a spoofed web site with the Microsoft brand designed to steer the sufferer into opening it on a Home windows gadget. It triggers a obtain of the Casbaneiro (aka Metamorfo) banking trojan.
- An e mail purporting to return from the sufferer’s HR division, which claims to include a employees termination record and particulars on new positions, as an attachment. Opening the faux PDF triggers a faux DocuSign login kind requesting the sufferer enters their e mail handle and password to entry it.
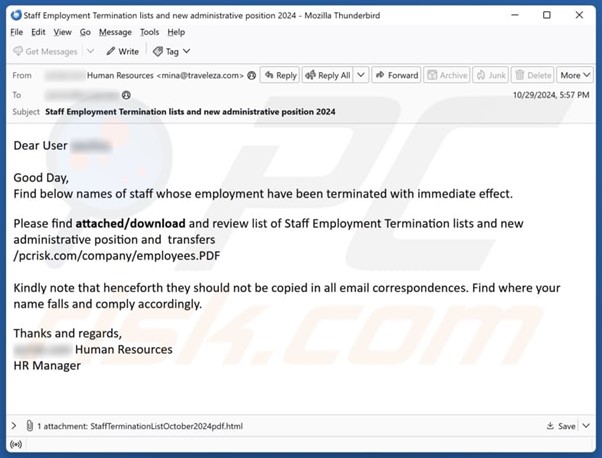
Methods to spot a job termination rip-off
As with all phishing assault, there are a couple of warning indicators which ought to flash pink if such an e mail results in your inbox. Take a deep breath and look out for giveaways akin to:
- An uncommon sender handle that doesn’t match the acknowledged sender. Hover your mouse over the “from” handle to see what pops up. It could be one thing utterly totally different, or it might be an try to mimic the impersonated firm’s area, utilizing typos and different characters (e.g., m1crosoft.com, @microsfot.com)
- A generic greeting (e.g., “expensive worker/consumer”), which is actually not the tone a authentic termination letter would take.
- Hyperlinks embedded within the e mail or attachments to open. These are sometimes a tell-tale signal of a phishing try. In the event you hover over the hyperlink and it doesn’t look proper, all of the extra cause to not click on.
- Hyperlinks or attachments that don’t open instantly, however request you to enter logins. By no means achieve this in response to an unsolicited message.
- Pressing language. Phishing messages will all the time attempt to rush you into making a rash choice.
- Misspellings, grammatical or different errors within the letter. These have gotten rarer as cybercriminals undertake generative AI instruments to jot down their phishing emails, however they’re nonetheless price looking for.
- Going ahead, be in your guard for AI-aided schemes the place scammers may use deepfake audio and video likenesses of precise folks (that of your boss, maybe) to trick you into giving up confidential company data.
Staying secure
To make sure you don’t get caught out by job termination scams, perceive the warning indicators listed above. And likewise take into account the next:
- Use sturdy, distinctive passwords for each account, ideally saved in a password supervisor
- Remember to change on two-factor authentication (2FA) for an additional layer of entry safety
- Make certain all your work and private gadgets are repeatedly patched and updated
- In case your IT division presents, be part of common phishing simulation workout routines to grasp what to look out for
- In the event you obtain a suspect message, by no means click on on embedded hyperlinks or open the attachment
- Contact the sender by different channels for those who’re involved – however not by replying to the e-mail or utilizing the contact particulars listed on it
- Report any suspect emails to your employer’s IT division
- Examine whether or not colleagues have obtained the identical message
Employment termination scams have been round for a while. But when they’re nonetheless doing the rounds, they have to nonetheless be working. At all times be sceptical of something hitting your inbox.







