AsyncRAT has cemented its place as a cornerstone of contemporary malware and as a pervasive risk that has developed right into a sprawling community of forks and variants. Whereas its capabilities are usually not that spectacular on their very own, it’s the open-source nature of AsyncRAT that has actually amplified its affect. This blogpost gives an outline and evaluation of essentially the most related forks of AsyncRAT, drawing connections between them and displaying how they’ve developed.
Key factors of this blogpost:
- We offer distinctive insights into the panorama of AsyncRAT and its quite a few variants as a way to navigate the labyrinth of forks simply.
- Within the effort to map the huge hierarchy of AsyncRAT’s forks, we uncover their distinctive interconnections and doc how these variants may be distinguished.
- We discover much less frequent variants that function distinctive plugins, starting from a primary screamer plugin to a USB malware spreader.
Origins of AsyncRAT
You will have heard of AsyncRAT, quick for asynchronous distant entry trojan. This open-source RAT was launched on GitHub in 2019 by a person going by the title of NYAN CAT. Developed in C#, it presents a variety of typical RAT functionalities, together with keylogging, display capturing, credential theft, and extra. Its simplicity and open-source nature has made it a well-liked selection amongst cybercriminals, resulting in its widespread use in varied cyberattacks.
However the place does it come from? We imagine that the groundwork for AsyncRAT was laid earlier by the Quasar RAT, which has been out there on GitHub since 2015 and encompasses a related method. Each are written in C#; nonetheless, their codebases differ basically, suggesting that AsyncRAT was not only a mere fork of Quasar, however a whole rewrite. A fork, on this context, is a private copy of another person’s repository that one can freely modify with out affecting the unique undertaking. The principle hyperlink that ties them collectively lies within the customized cryptography lessons used to decrypt the malware configuration settings. Particularly, these are lessons Aes256 and Sha256, which fall underneath the Shopper.Algorithm namespace for AsyncRAT and the Quasar.Frequent.Cryptography namespace for Quasar. Determine 1 reveals an identical code being utilized in each implementations of Aes256.
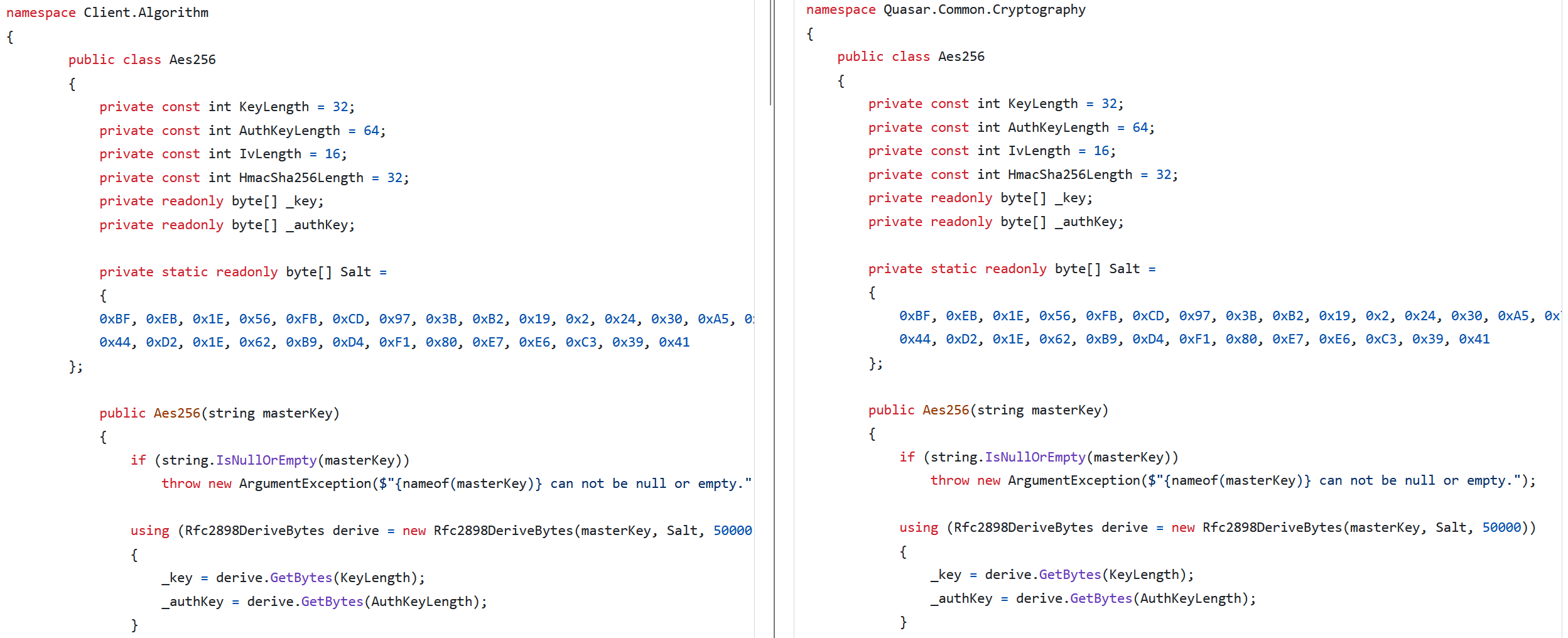
The identical code is usually copied and pasted, together with the identical salt worth and decryption settings. This class, along with Sha256, leads us to imagine that AsyncRAT was to some extent influenced by the Quasar RAT.
Aside from these similarities, AsyncRAT launched vital enhancements, significantly in its modular structure and enhanced stealth options, which make it extra adaptable and tougher to detect in fashionable risk environments. Its plugin-based structure and ease of modification have sparked the proliferation of many forks, pushing the boundaries even additional.
Fork labyrinth
Ever because it was launched to the general public, AsyncRAT has spawned a large number of recent forks which have constructed upon its basis. A few of these new variations have expanded on the unique framework, incorporating extra options and enhancements, whereas others are primarily the identical model in several garments.
Fork hierarchy
Determine 2 illustrates how among the extra prevalent AsyncRAT forks have developed from each other over time.
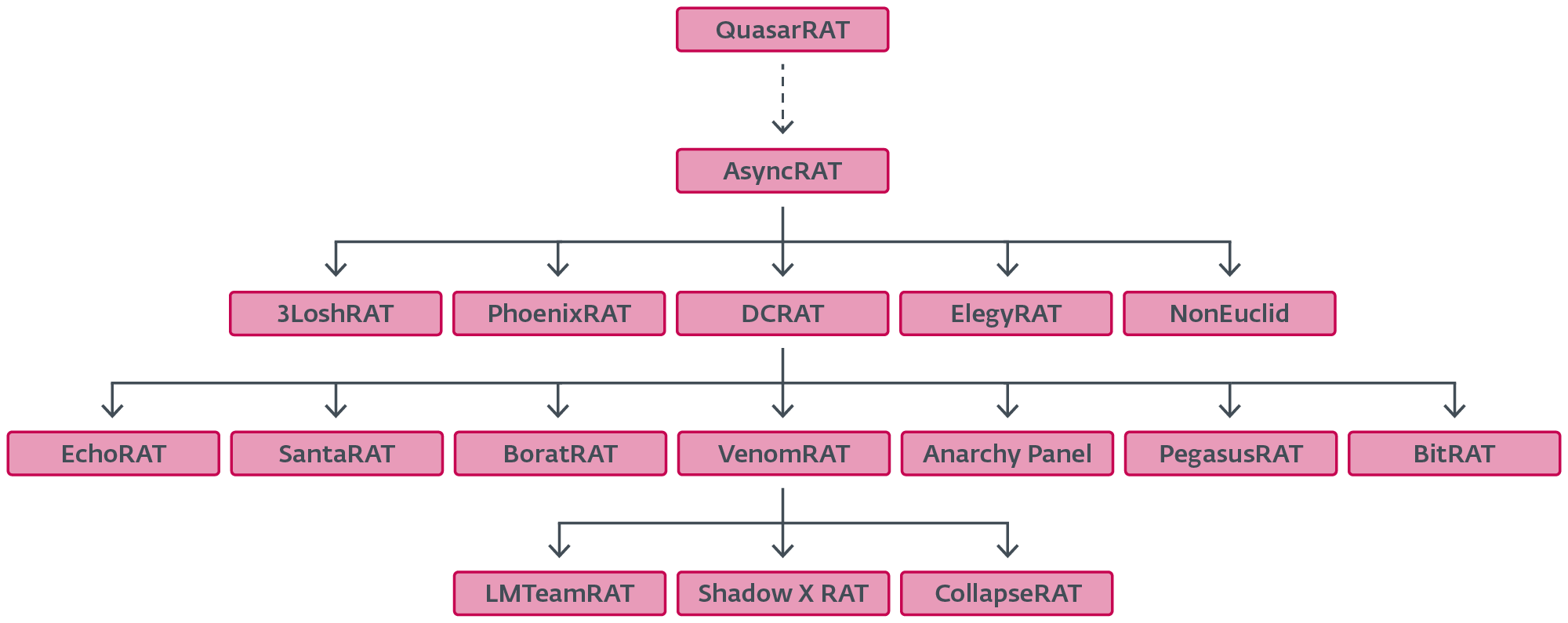
In the midst of the tree are DcRat and VenomRAT. Our evaluation has proven that they’re essentially the most broadly deployed variants, collectively accounting for a major variety of campaigns. Different lesser-known forks occupy smaller however nonetheless notable parts of the pie. Determine 3 depicts the distribution of essentially the most prevalent forks in accordance with our telemetry.
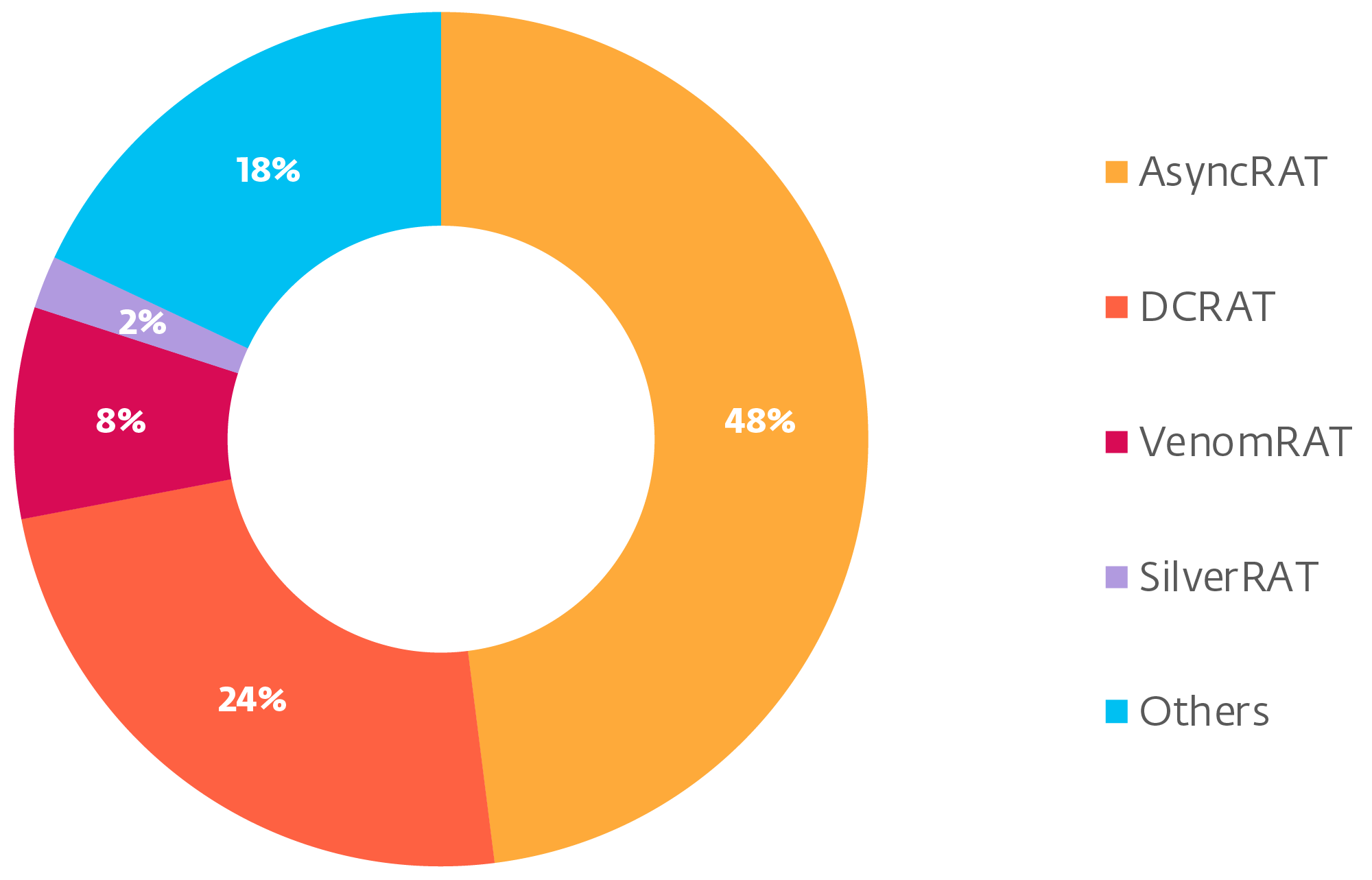
DcRat presents a notable enchancment over AsyncRAT by way of options and capabilities. One of many extra apparent adjustments is the info construction used for transferring knowledge forwards and backwards. It makes use of MessagePack, a well known open-source library for extra environment friendly binary knowledge serialization. DcRat additionally implements evasion strategies like AMSI and ETW patching, which work by disabling security measures that detect and log malicious conduct – AMSI patching prevents script scanning, whereas ETW patching blocks occasion tracing. Moreover, it options an antiprocess system whereby processes whose names match these in a denylist are terminated. Blocklisted applications embrace Taskmgr.exe, ProcessHacker.exe, MsMpEng.exe, Taskkill.exe, and so on.
It’s additionally value noting that DcRat’s plugin base builds upon AsyncRAT and additional extends its performance. Among the many added plugins are capabilities similar to webcam entry, microphone recording, Discord token theft, and “enjoyable stuff”, a set of plugins used for joke functions like opening and shutting the CD tray, blocking keyboard and mouse enter, transferring the mouse, turning off the monitor, and so on. Notably, DcRat additionally introduces a easy ransomware plugin that makes use of the AES-256 cipher to encrypt recordsdata, with the decryption key distributed solely as soon as the plugin has been requested. Aside from that, there seem like many small adjustments like a distinct selection of salt (a string as an alternative of a binary worth), intentionally modified variable names to additional evade detection, dynamic API decision, and plenty of extra.
VenomRAT, however, was possible impressed by DcRat, as evidenced within the Figuring out variations part. The malware is filled with so many options that it might be thought of a separate risk by itself. We have now chosen to group it underneath AsyncRAT as their consumer elements are similar to one another. VenomRAT’s options and plugins have been documented in additional element by different distributors, so we gained’t dive deep into them on this blogpost.
Not all RATs are critical in nature although, and this is applicable equally to AsyncRAT forks. Clones like SantaRAT or BoratRAT (see Determine 4) are supposed to be jokes. Within the case of the previous, its authors have themselves acknowledged that the undertaking was mainly “shamelessly ripped off of DcRat”. But, regardless of this, we have now discovered cases of real-world utilization of them within the wild.

Figuring out variations
Whereas doing the evaluation, we used varied strategies to establish and categorize every pattern. It needs to be famous that the analysis was totally on the consumer a part of the malware, as this binary is what finally ends up on victims’ machines. It incorporates helpful data similar to malware configuration and the place details about the C&C may be discovered.
The quickest and most simple method to establish a fork is to peek straight into the malware’s configuration, which may often be discovered within the InitializeSettings perform. The configuration values are encrypted with AES-256 and saved as base64 strings within the Settings class. Usually, the proper fork title is available and conveniently labeled as Model. In about 90% of our analyzed samples, the Model area incorporates some significant description of both the fork’s title or the malware writer’s pseudonym. The remaining samples had this area deliberately left clean. Determine 5 illustrates the everyday configuration initialization process present in DcRat and its derivatives (VenomRAT on this case).
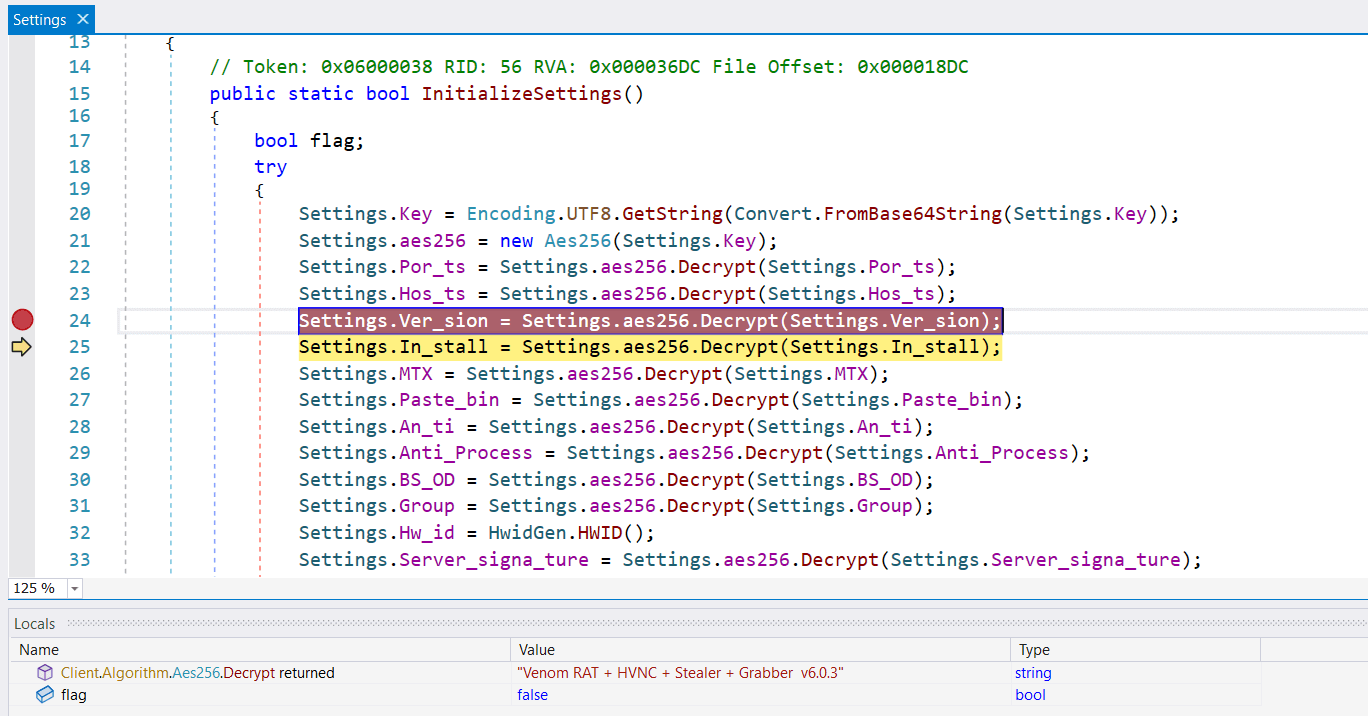
If the Model area is empty, typically it’s attainable to get one other clue by wanting on the Salt worth used for encrypting the configuration. Attackers typically neglect this parameter when copy-pasting their very own fork. The Salt worth may be discovered within the Shopper.Algorithm.Aes256 class, as seen in Determine 6.
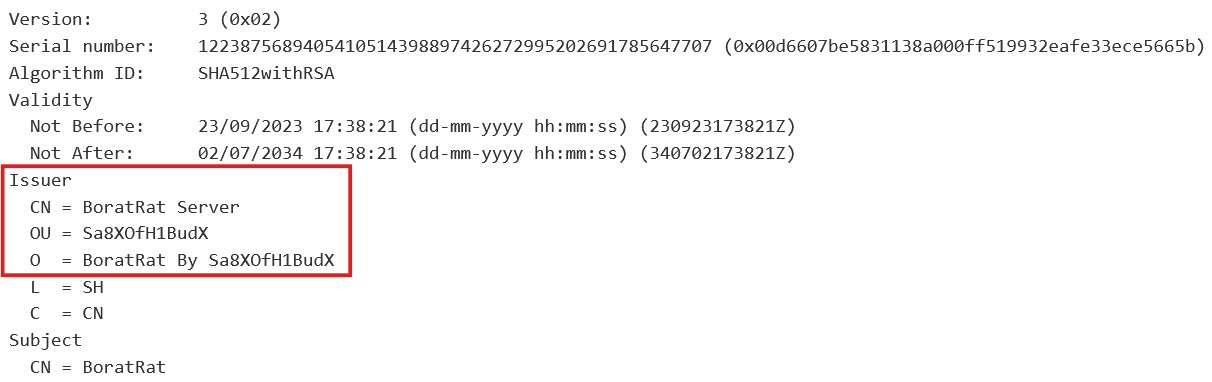
One more method to get extra perception is to search for the embedded certificates used to authenticate the C&C server. It’s additionally situated within the configuration as a base64-encoded worth. Unpacking this worth typically reveals additional details about the server, similar to frequent title, group, and organizational unit. If a selected fork has its personal title within the Model area, it’s typically attainable to hint again the earlier fork upon which it was possible primarily based by wanting on the CN area. Determine 7 reveals a DER-encoded certificates that reveals the BoratRAT fork, after extraction and decoding.
The strategies talked about above primarily apply to trivial instances the place malware authors both didn’t trouble to take away traces or used a default certificates. A extra refined methodology for figuring out AsyncRAT servers exists, which includes sending a specifically crafted packet to the C&C server. This method is defined intimately on this Axel Mahr blogpost.
Ought to the whole lot else fail, figuring out the pattern origin can in the end be accomplished the old school approach, by manually inspecting the code. This includes an in depth evaluation of the code’s construction, syntax, and performance, evaluating them towards the patterns of beforehand categorized samples.
In depth fork checklist
We have now highlighted right here among the extra distinguished AsyncRAT forks. As a result of sheer variety of out there forks, it isn’t possible to cowl each single one. For completeness, Determine 8 gives an prolonged checklist of AsyncRAT forks identified for use for malicious functions, as seen in ESET telemetry thus far.

Exploring lesser-known variants
To date, we’ve talked about among the main forks that dominate the panorama. On this part, we have now cherry-picked some lesser-known forks that improve AsyncRAT’s performance past the options included within the default variations. These unique forks are sometimes the work of 1 particular person or group and so they make up lower than 1% of the quantity of AsyncRAT samples.
NonEuclid RAT
This fork stands out primarily for its inclusion of recent plugins, on high of the default ones. Whereas some plugins may appear trivial or geared in the direction of “enjoyable stuff”, others, like WormUsb.dll, have distinctly malicious functions. Desk 1 lists a choice of NonEuclid RAT plugins that deviate from the usual plugin base seen in common forks.
Desk 1. Collection of NonEuclid RAT plugins we deemed attention-grabbing
| Plugin title | Description |
| Screamer.dll | Bounce scare plugin. |
| Piano.dll | Generic audio participant. |
| Service.dll | Home windows providers administration. |
| Maps.dll | Collects geolocation information from the person. |
| WormUsb.dll | Malware spreader plugin. |
| Brute.dll | SSH and FTP brute forcer. |
| Signature Antivirus.dll | Easy signature-based file matcher. |
| cliper.dll | Replaces clipboard knowledge with attacker’s cryptocurrency pockets addresses. |
Screamer.dll
There are 5 bounce scare photos constructed into the plugin. An attacker sends a command that signifies which picture they need to use, together with the WAV file to be performed, and the delay after which the bounce scare is triggered. Determine 9 reveals the primary three prebundled photos an attacker might select from.



Piano.dll
This plugin performs arbitrary WAV recordsdata. All sound recordsdata are saved in %appdatapercentPiano. piano.dll helps three instructions:
- SetSound – provides a brand new sound file to %appdatapercentPiano,
- PlayMisc – performs a requested sound file from %appdatapercentPiano, and
- ClientAdd – retrieves a number of sound recordsdata from the C&C server.
Service.dll
This plugin facilitates managing Home windows providers, similar to beginning, stopping, and pausing providers.
Maps.dll
It is a easy plugin to gather geolocation data from the sufferer. It makes use of the .NET GeoCoordinateWatcher class to register a callback perform to gather knowledge every time the situation is out there. Among the many collected data are latitude, longitude, username, and pc title.
WormUsb.dll
This plugin compromises PE recordsdata with an arbitrary payload specified by the attacker.
Regardless of the time period Usb in WormUsb.dll, this plugin targets a number of areas primarily based on the command offered:
- InfectExe – compromises a person PE file,
- InfectExeInWindows – targets PE recordsdata in private folders (Desktop, Paperwork, Downloads, My Music), and
- InfectUsbExe – targets PE recordsdata in all drives excluding the C drive.
Beneath the hood, it really works by transferring the unique file to a brief location. Then it drops a small stub instead of the unique file. This stub’s useful resource part is then populated to include each the unique file and the required payload, each of that are compressed and encrypted with a per-file key, generated on the time of development. Following this, the malware then obfuscates the stub by introducing proxy strategies, including customized management move obfuscation, and variable renaming. As a remaining contact, it embeds the unique icon and metadata within the modified stub. Determine 10 reveals the perform, with the unique methodology names, liable for compromising a single file.
When such a compromised file is executed, it first decrypts, unpacks and runs the payload program, then proceeds to do the identical with the unique program.
Brute.dll
This plugin helps brute forcing of each SSH and FTP protocols from the consumer aspect. The attacker feeds it three parameters: host, login, and password, and the plugin will attempt to join utilizing these credentials. If the connection succeeds, the credentials are despatched again to the attacker with a flag indicating success. It’s not tough to think about a situation whereby an attacker would possibly use this type of assault to distribute brute forcing throughout a big pool of compromised machines, thus circumventing restrictions primarily based solely on the IP handle.
Signature Antivirus.dll
The title of the plugin implies it might need one thing to do with antivirus performance. Whereas that is technically true, it’s also a case of essentially the most primitive, handbook antivirus resolution ever created. The plugin receives an inventory of MD5 hashes from the attacker and compares them to the hashes of all EXE recordsdata it finds on each disk. If an identical file is discovered, it triggers the oddly named DetectVirus perform, which merely deletes the file with none additional evaluation. This makes the title of the plugin very doubtful at greatest. Within the arms of the malware writer, it could have been used to delete competitor malware, or actually simply any arbitrary file.
cliper.dll
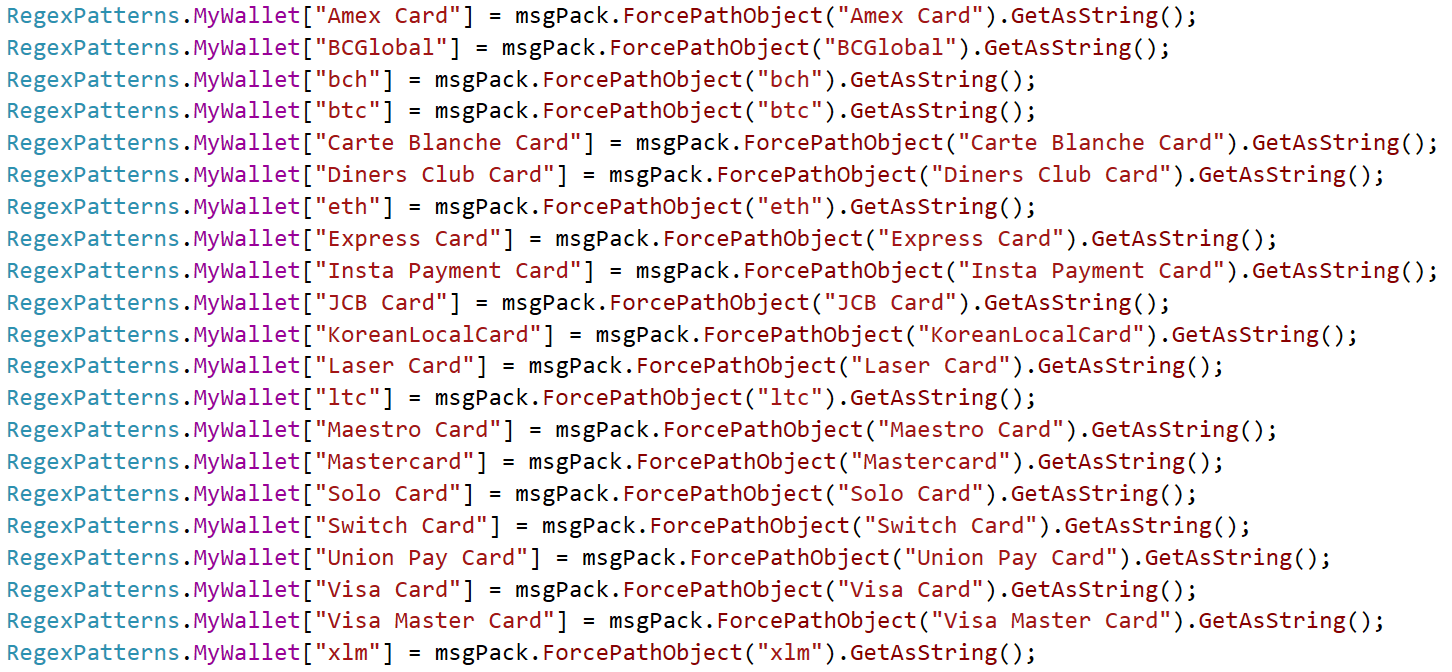
It is a standalone clipper that constantly screens the sufferer’s clipboard, and if a cryptocurrency pockets handle is detected, it’s changed with one offered by the attacker. Attacker-provided wallets are solely despatched when the plugin is first requested; they don’t seem to be hardcoded within the plugin. Moreover, in Determine 11, we will additionally see some bank card entries. This plugin incorporates an intensive checklist of regexes that may detect each cryptocurrency wallets and bank cards, and within the case of the latter they only get despatched again to the attacker.
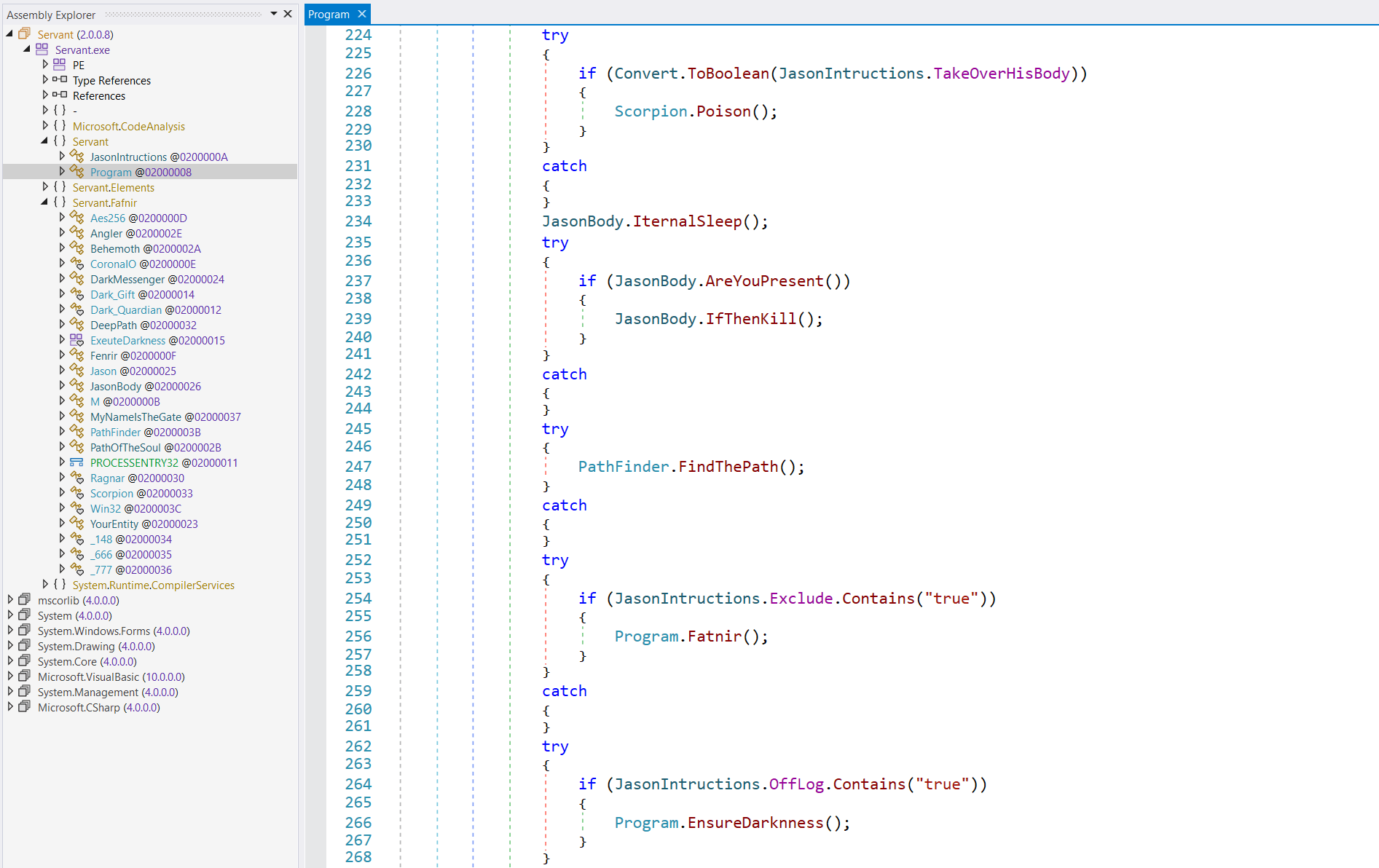
JasonRAT
Recognized in 2024, this variant reveals continued indicators of exercise. It’s attention-grabbing in that it employs obscure variable-naming conventions paying homage to “satanic” phrases from what the malware writer refers to because the Guide of Jason. In Determine 12, you possibly can see typical AsyncRAT configuration values (in base64), however with renamed variables, whereas Determine 13 reveals the logic of the principle entry level of the malware. In addition to the standard configuration values, this variant additional extends the consumer by introducing nation concentrating on.
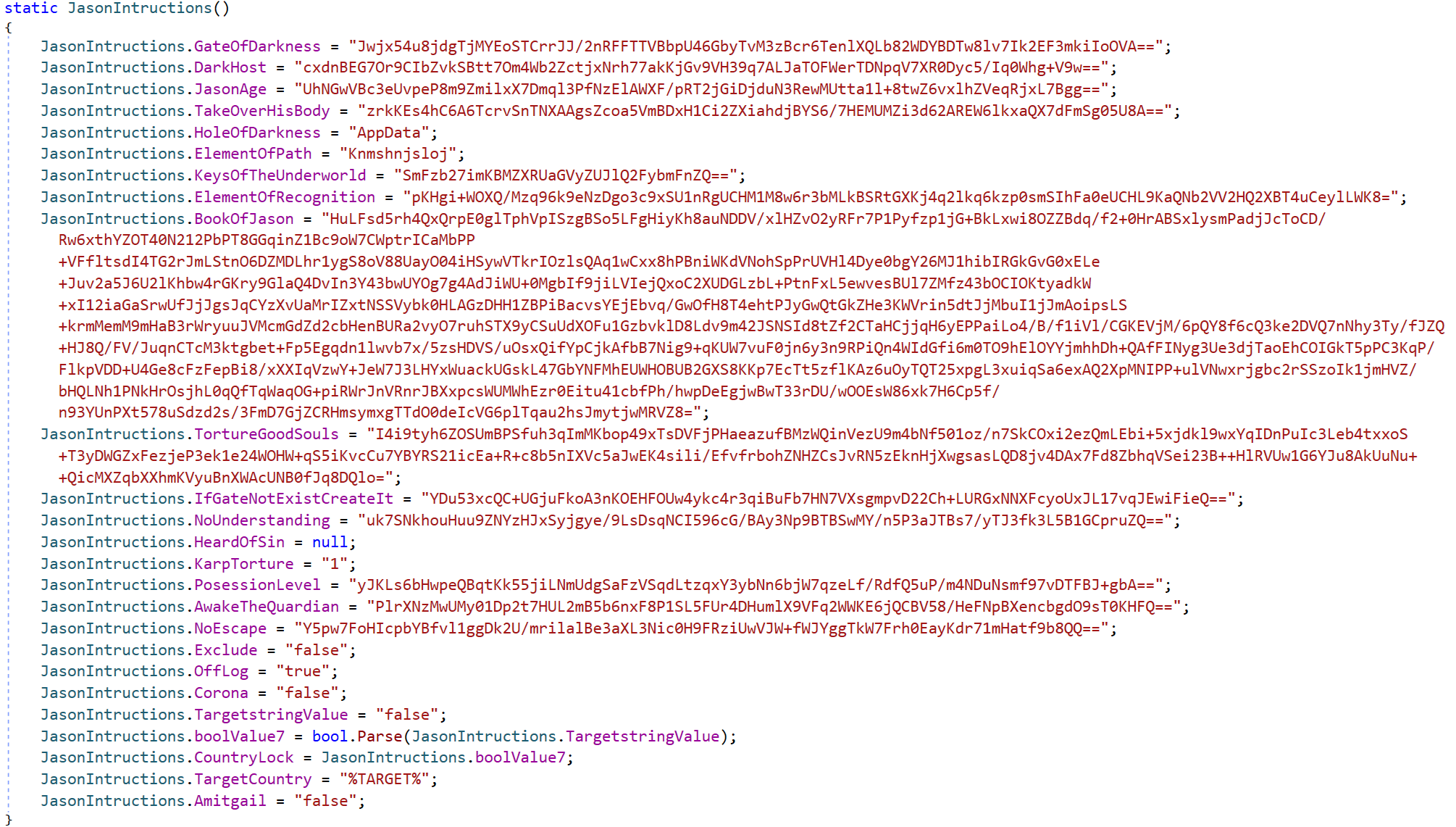
One other unusual function is the selection of string obfuscation. A subset of the strings employs an additional layer of obfuscation by using an prolonged variant of Morse code. Each uppercase and lowercase letters are included, in addition to some particular characters. Determine 14 reveals the encoded registry key string utilizing an prolonged mapping.
XieBroRAT
It is a RAT with Chinese language localization. It introduces a brand new plugin, BrowserGhost.dll, which is a browser-credential stealer. One other plugin, Abstain.dll, gives interplay with Cobalt Strike servers by making a reverse connection.
To extend the protection, the malware gives the supply chain in a number of completely different languages. The usual .NET consumer binary may be wrapped and distributed through shellcode, VBS, or JavaScript.
Lastly, the writer additional prolonged the malware by borrowing closely from open-source initiatives, integrating instruments like mimikatz, SharpWifiGrabber, SharpUnhooker, and so on.
Conclusion
AsyncRAT’s rise and its subsequent forks spotlight the inherent dangers of open-source malware frameworks. Our evaluation revealed a various and evolving ecosystem of derivatives, starting from persistent threats like DcRat and VenomRAT to lesser-known novelty forks like JasonRAT and BoratRAT, which appear to serve extra as curiosities than credible threats. All of those forks not solely prolong AsyncRAT’s technical capabilities but additionally show how rapidly and creatively risk actors can adapt and repurpose open-source code.
The widespread availability of such frameworks considerably lowers the barrier to entry for aspiring cybercriminals, enabling even novices to deploy refined malware with minimal effort. This democratization of malware growth – particularly contemplating the rising recognition of LLMs and potential to misuse their capabilities – additional accelerates the creation and customization of malicious instruments, contributing to a quickly increasing and more and more complicated risk panorama.
In mild of those developments, it’s cheap to anticipate that future forks might incorporate extra superior obfuscation, modularity, and evasion capabilities. This potential evolution underscores the significance of proactive detection methods and deeper behavioral evaluation to successfully handle rising threats.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis presents non-public APT intelligence stories and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete checklist of indicators of compromise (IoCs) may be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| F8E31B338123E38757F8 |
Screamer.dll | MSIL/AsyncRAT.C | NonEuclid bounce scare plugin. |
| 98223D2F8DF2F9E832AE |
Piano.dll | MSIL/AsyncRAT.C | NonEuclid audio participant plugin. |
| CDEC9A1C73E3E21B1D70 |
Maps.dll | MSIL/AsyncRAT.C | NonEuclid geolocation plugin. |
| 932C49EEE087D432D0DA |
Service.dll | MSIL/AsyncRAT.C | NonEuclid Home windows service administration plugin. |
| 2FA98D088486BAC57FF6 |
WormUsb.dll | MSIL/AsyncRAT.C | NonEuclid malware spreader plugin. |
| 62C9FEFA84067F695032 |
Brute.dll | MSIL/AsyncRAT.C | NonEuclid SSH and FTP brute forcer plugin. |
| FAD946F7ACF017F0C50C |
Signature |
MSIL/AsyncRAT.C | NonEuclid signature-based file matcher plugin. |
| 51B8A5818B7031EDB59A |
cliper.dll | MSIL/AsyncRAT.C | NonEuclid clipboard hijacker plugin. |
| 4FB0CAAD6E345947EE2D |
Stub.exe | MSIL/AsyncRAT.A | AsyncRAT consumer. |
| FD9CF01CEA7DE8631C34 |
Stub.exe | MSIL/AsyncRAT.A | 3LoshRAT consumer. |
| B8AB93E958E0DE4BE276 |
Shopper.exe | MSIL/AsyncRAT.A | DcRat consumer. |
| 68B58483D0E4E7CC2478 |
Microsoft_Edge |
MSIL/AsyncRAT.A | VenomRAT consumer. |
| 4F69E0CE283D273B724C |
Shopper.exe | MSIL/AsyncRAT.C | BoratRAT consumer. |
| E4F87568473536E35006 |
Shopper.exe | MSIL/AsyncRAT.A | Anarchy Panel consumer. |
| D10B8197732437E9BF84 |
Shopper.exe | MSIL/AsyncRAT.A | CollapseRAT consumer. |
| 0DC28EA51F0D96E0D1BC |
dwm.exe | MSIL/AsyncRAT.A | Shadow X RAT consumer. |
| E5B511E7550CBADE74E7 |
ClientAny.exe | MSIL/AsyncRAT.A | LMTeamRAT consumer. |
| 3124F58428184FDF75E2 |
Stub.exe | MSIL/AsyncRAT.A | PhoenixRAT consumer. |
| 8402AA507CF5B1BBFAB5 |
Shopper.exe | MSIL/AsyncRAT.A | EchoRAT consumer. |
| AB2C6F9695346FAA9495 |
Shopper.exe | MSIL/AsyncRAT.A | XieBroRAT consumer. |
| 3E6CD9D07B8ECE706697 |
tempClient.exe | MSIL/AsyncRAT.C | NonEuclid RAT consumer. |
| FF4592A8BCB58F5CF6BD |
Servant.exe | MSIL/AsyncRAT.A | JasonRAT consumer. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 17 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Protection Evasion | T1562.001 | Impair Defenses: Disable or Modify Instruments | DcRat terminates safety instruments similar to Taskmgr.exe and MsMpEng.exe. |
| T1562.004 | Impair Defenses: Disable or Modify System Firewall | DcRat leverages AMSI and ETW bypass strategies to evade detection. | |
| T1027.013 | Obfuscated Recordsdata or Info: Encrypted/Encoded File | JasonRAT employs modified Morse code and obscure variable names to hinder evaluation. | |
| Credential Entry | T1539 | Steal Net Session Cookie | DcRat leverages a plugin to steal Discord tokens from compromised machines. |
| T1555.003 | Credentials from Password Shops: Credentials from Net Browsers | XieBroRAT makes use of a plugin to gather browser credentials. | |
| T1110.003 | Brute Power: Password Spraying | NonEuclid makes use of a plugin to brute drive SSH and FTP credentials. | |
| Discovery | T1614.001 | System Location Discovery: System Language Discovery | NonEuclid makes use of a plugin that collects geolocation knowledge from compromised programs. |
| Assortment | T1123 | Audio Seize | DcRat has a microphone plugin that allows audio seize from the sufferer’s machine. |
| T1125 | Video Seize | DcRat features a webcam plugin that enables distant entry to the sufferer’s digital camera. | |
| T1115 | Clipboard Knowledge | NonEuclid makes use of a plugin that screens the clipboard to intercept and substitute cryptocurrency pockets addresses. | |
| Influence | T1486 | Knowledge Encrypted for Influence | DcRat encompasses a ransomware plugin able to encrypting recordsdata on the sufferer’s system. |

