A intelligent malware deployment scheme first noticed in focused assaults final 12 months has now gone mainstream. On this rip-off, dubbed “ClickFix,” the customer to a hacked or malicious web site is requested to differentiate themselves from bots by urgent a mix of keyboard keys that causes Microsoft Home windows to obtain password-stealing malware.
ClickFix assaults mimic the “Confirm You’re a Human” exams that many web sites use to separate actual guests from content-scraping bots. This specific rip-off normally begins with a web site popup that appears one thing like this:
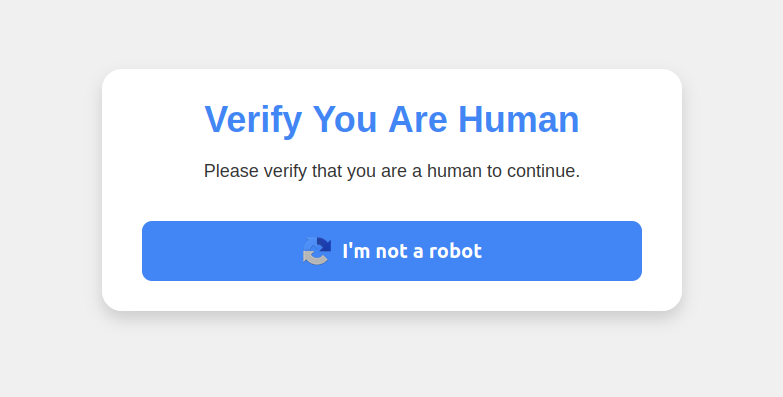
This malware assault pretends to be a CAPTCHA supposed to separate people from bots.
Clicking the “I’m not a robotic” button generates a pop-up message asking the consumer to take three sequential steps to show their humanity.

Executing this sequence of keypresses prompts Home windows to obtain password-stealing malware.
Step 1 includes concurrently urgent the keyboard key with the Home windows icon and the letter “R,” which opens a Home windows “Run” immediate that may execute any specified program that’s already put in on the system.
Step 2 asks the consumer to press the “CTRL” key and the letter “V” on the identical time, which pastes malicious code from the location’s digital clipboard.
Step 3 — urgent the “Enter” key — causes Home windows to obtain and launch malicious code by “mshta.exe,” a Home windows program designed to run Microsoft HTML utility recordsdata.
“This marketing campaign delivers a number of households of commodity malware, together with XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT,” Microsoft wrote in a weblog publish on Thursday. “Relying on the precise payload, the precise code launched by mshta.exe varies. Some samples have downloaded PowerShell, JavaScript, and moveable executable (PE) content material.”
In keeping with Microsoft, hospitality staff are being tricked into downloading credential-stealing malware by cybercriminals impersonating Reserving.com. The corporate stated attackers have been sending malicious emails impersonating Reserving.com, typically referencing adverse visitor critiques, requests from potential visitors, or on-line promotion alternatives — all in a bid to persuade folks to step by one among these ClickFix assaults.
In November 2024, KrebsOnSecurity reported that a whole bunch of resorts that use reserving.com had been topic to focused phishing assaults. A few of these lures labored, and allowed thieves to acquire management over reserving.com accounts. From there, they despatched out phishing messages asking for monetary info from individuals who’d simply booked journey by the corporate’s app.
Earlier this month, the safety agency Arctic Wolf warned about ClickFix assaults concentrating on folks working within the healthcare sector. The corporate stated these assaults leveraged malicious code stitched into the broadly used bodily remedy video web site HEP2go that redirected guests to a ClickFix immediate.
An alert (PDF) launched in October 2024 by the U.S. Division of Well being and Human Providers warned that the ClickFix assault can take many kinds, together with faux Google Chrome error pages and popups that spoof Fb.
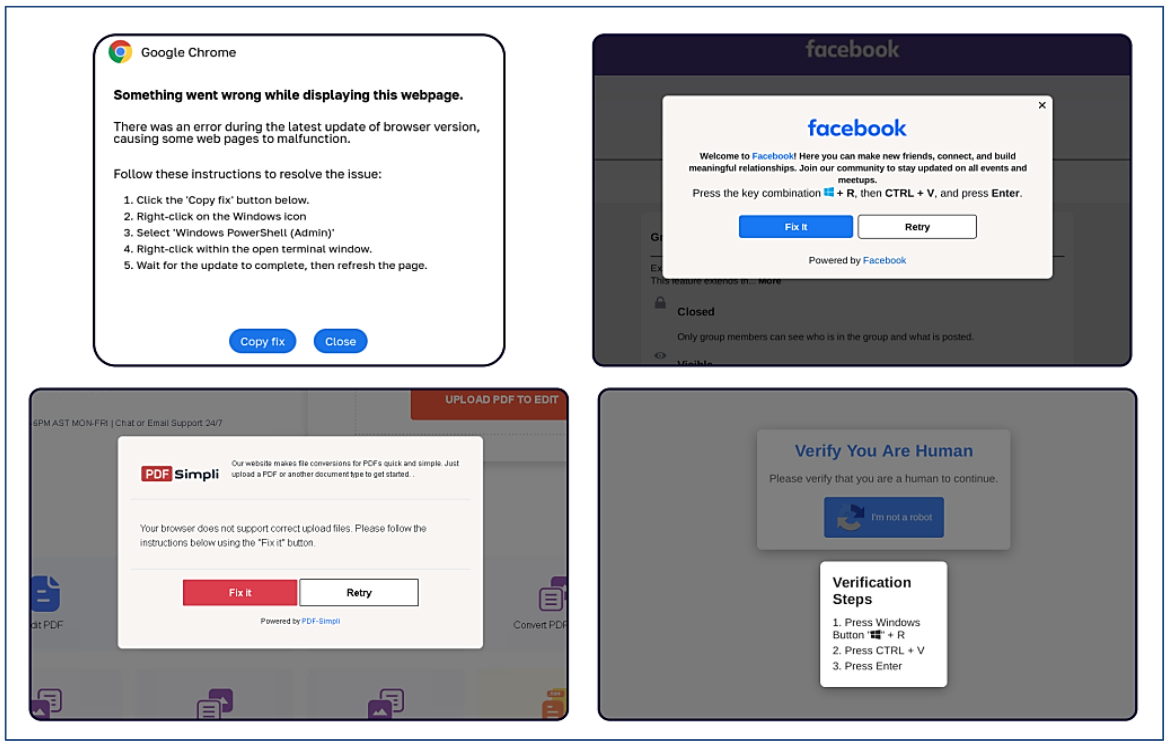
ClickFix tactic utilized by malicious web sites impersonating Google Chrome, Fb, PDFSimpli, and reCAPTCHA. Supply: Sekoia.
The ClickFix assault — and its reliance on mshta.exe — is harking back to phishing strategies employed for years that hid exploits inside Microsoft Workplace macros. Malicious macros grew to become such a typical malware risk that Microsoft was pressured to start out blocking macros by default in Workplace paperwork that attempt to obtain content material from the online.
Alas, the e-mail safety vendor Proofpoint has documented loads of ClickFix assaults by way of phishing emails that embody HTML attachments spoofing Microsoft Workplace recordsdata. When opened, the attachment shows a picture of Microsoft Phrase doc with a pop-up error message directing customers to click on the “Resolution” or “Methods to Repair” button.
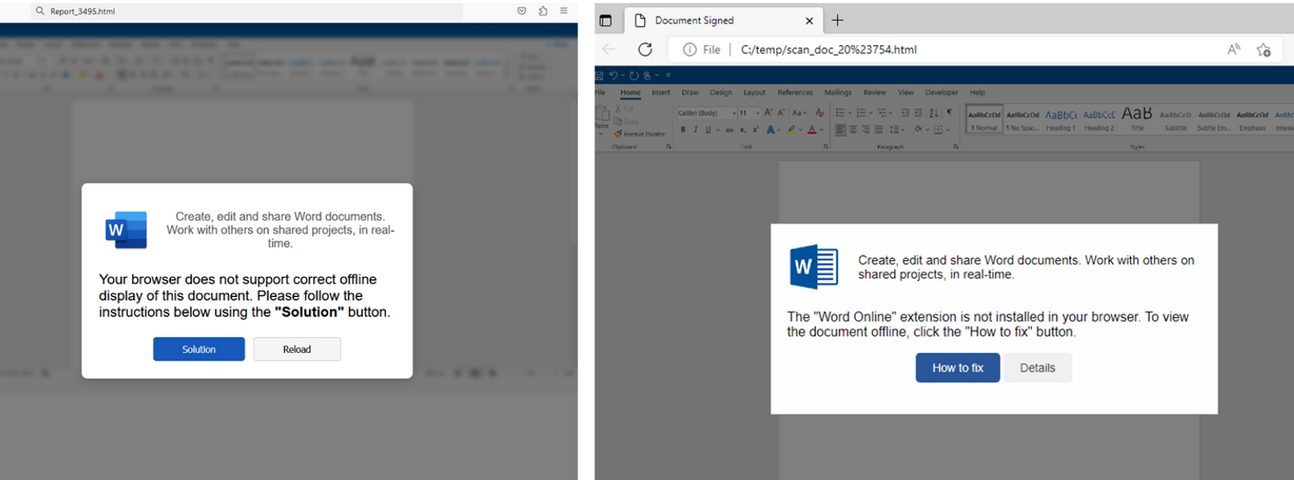
HTML recordsdata containing ClickFix directions. Examples for attachments named “Report_” (on the left) and “scan_doc_” (on the appropriate). Picture: Proofpoint.
Organizations that want to take action can benefit from Microsoft Group Coverage restrictions to stop Home windows from executing the “run” command when customers hit the Home windows key and the “R” key concurrently.
A intelligent malware deployment scheme first noticed in focused assaults final 12 months has now gone mainstream. On this rip-off, dubbed “ClickFix,” the customer to a hacked or malicious web site is requested to differentiate themselves from bots by urgent a mix of keyboard keys that causes Microsoft Home windows to obtain password-stealing malware.
ClickFix assaults mimic the “Confirm You’re a Human” exams that many web sites use to separate actual guests from content-scraping bots. This specific rip-off normally begins with a web site popup that appears one thing like this:

This malware assault pretends to be a CAPTCHA supposed to separate people from bots.
Clicking the “I’m not a robotic” button generates a pop-up message asking the consumer to take three sequential steps to show their humanity.

Executing this sequence of keypresses prompts Home windows to obtain password-stealing malware.
Step 1 includes concurrently urgent the keyboard key with the Home windows icon and the letter “R,” which opens a Home windows “Run” immediate that may execute any specified program that’s already put in on the system.
Step 2 asks the consumer to press the “CTRL” key and the letter “V” on the identical time, which pastes malicious code from the location’s digital clipboard.
Step 3 — urgent the “Enter” key — causes Home windows to obtain and launch malicious code by “mshta.exe,” a Home windows program designed to run Microsoft HTML utility recordsdata.
“This marketing campaign delivers a number of households of commodity malware, together with XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT,” Microsoft wrote in a weblog publish on Thursday. “Relying on the precise payload, the precise code launched by mshta.exe varies. Some samples have downloaded PowerShell, JavaScript, and moveable executable (PE) content material.”
In keeping with Microsoft, hospitality staff are being tricked into downloading credential-stealing malware by cybercriminals impersonating Reserving.com. The corporate stated attackers have been sending malicious emails impersonating Reserving.com, typically referencing adverse visitor critiques, requests from potential visitors, or on-line promotion alternatives — all in a bid to persuade folks to step by one among these ClickFix assaults.
In November 2024, KrebsOnSecurity reported that a whole bunch of resorts that use reserving.com had been topic to focused phishing assaults. A few of these lures labored, and allowed thieves to acquire management over reserving.com accounts. From there, they despatched out phishing messages asking for monetary info from individuals who’d simply booked journey by the corporate’s app.
Earlier this month, the safety agency Arctic Wolf warned about ClickFix assaults concentrating on folks working within the healthcare sector. The corporate stated these assaults leveraged malicious code stitched into the broadly used bodily remedy video web site HEP2go that redirected guests to a ClickFix immediate.
An alert (PDF) launched in October 2024 by the U.S. Division of Well being and Human Providers warned that the ClickFix assault can take many kinds, together with faux Google Chrome error pages and popups that spoof Fb.

ClickFix tactic utilized by malicious web sites impersonating Google Chrome, Fb, PDFSimpli, and reCAPTCHA. Supply: Sekoia.
The ClickFix assault — and its reliance on mshta.exe — is harking back to phishing strategies employed for years that hid exploits inside Microsoft Workplace macros. Malicious macros grew to become such a typical malware risk that Microsoft was pressured to start out blocking macros by default in Workplace paperwork that attempt to obtain content material from the online.
Alas, the e-mail safety vendor Proofpoint has documented loads of ClickFix assaults by way of phishing emails that embody HTML attachments spoofing Microsoft Workplace recordsdata. When opened, the attachment shows a picture of Microsoft Phrase doc with a pop-up error message directing customers to click on the “Resolution” or “Methods to Repair” button.

HTML recordsdata containing ClickFix directions. Examples for attachments named “Report_” (on the left) and “scan_doc_” (on the appropriate). Picture: Proofpoint.
Organizations that want to take action can benefit from Microsoft Group Coverage restrictions to stop Home windows from executing the “run” command when customers hit the Home windows key and the “R” key concurrently.





