Indicators of Compromise (IoCs) act as digital forensic breadcrumbs that time to knowledge breaches. IoCs assist determine malicious exercise, however conventional detection strategies principally react to incidents after they happen. A compromise possible occurs earlier than anybody spots an indicator. Organizations want instant detection capabilities to reduce harm and comprise safety threats earlier than they develop.
This piece will share confirmed methods for fast risk containment. We’ll get into the challenges of conventional indicators of compromise (IOC) detection strategies and present how organizations can construct incident response frameworks that reduce down detection and containment occasions.
What are Indicators of Compromise?
Indicators of Compromise (IOCs) function forensic breadcrumbs that safety professionals use to determine potential safety breaches in networks or techniques. These digital clues assist us observe malicious exercise and perceive cyber-attack patterns throughout risk searching.
Widespread Indicators of Compromise embody:
-
Malicious domains and IP addresses -
Suspicious registry modifications -
Suspicious file hashes -
Anomalous community site visitors patterns
Monitoring these indicators allows early detection of threats, permitting for swift response and mitigation.
Varieties of IOCs:
-
File-based IOCs: File hashes, registry key modifications, and unauthorized scripts. -
Community-based IOCs: Outbound site visitors to command-and-control servers, uncommon DNS requests. -
Behavioral IOCs: Uncommon login makes an attempt, a number of failed login makes an attempt, spikes in database reads, or distant entry request from odd geolocations.
Behavioral indicators of compromise (IOC) provide sturdy early-warning indicators. Not like static indicators, they’re tougher for attackers to disguise, making them important for real-time detection.
Safety groups also needs to monitor for surprising HTML response sizes, suspicious processes, and community site visitors anomalies from unusual geographic areas.
Challenges with Conventional indicators of compromise IOC Detection
Conventional indicators of compromise (IOC) detection strategies create main safety challenges regardless of their extensive use. Safety groups don’t deal very nicely with fundamental limitations that decelerate risk response. Our staff at Fidelis Safety has seen these roadblocks firsthand in safety operations of all sizes.
Delayed detection and response occasions
Most traditional Indicators of Compromise detection techniques react to threats as a substitute of stopping them. So safety groups usually discover threats hours or days after the unique compromise. This delay between an infection and detection provides attackers the possibility to dig in, transfer by means of networks, and steal delicate knowledge. Groups face a number of approval phases that stretch out repair occasions even after they spot a risk.
Handbook triage of alerts resulting in sluggish containment
Safety analysts deal with Indicators of Compromise alerts principally by hand, which creates bottlenecks throughout essential responses. Every alert wants particular person checking, verification, and escalation. These duties eat up precious time whereas threats hold spreading. Even profitable detection doesn’t remedy the containment drawback due to guide processes.
Fidelis Deception can velocity up detection by figuring out attackers throughout reconnaissance—usually earlier than any precise compromise happens. This permits preemptive containment.
Uncover how deception expertise helps you:
-
Use decoys to reveal hidden threats -
Monitor attacker conduct in real-time -
Shift from reactive to proactive protection
Siloed instruments and fragmented visibility
Organizations use separate safety instruments that can’t discuss to one another correctly. This break up creates harmful blind spots the place threats slip by means of unnoticed. To quote an occasion, community monitoring may catch suspicious site visitors with out seeing what’s occurring on endpoints. This makes an in depth risk evaluation virtually inconceivable. Safety groups can’t piece collectively the entire assault story from scattered knowledge factors.
Alert fatigue from false positives
The most important drawback could be the flood of false constructive alerts from conventional IOC safety techniques. Safety analysts wade by means of a whole bunch—possibly even 1000’s—of day by day safety alerts. Many come from innocent actions or regular enterprise operations. This fixed noise makes groups numb to actual threats and wastes assets. Alert fatigue turns into another excuse for missed detections and sluggish responses to Actual-Time IOC Detection and Response efforts.
Key Methods for Actual-Time IOC Detection and Menace Containment
.elementor-widget-image{text-align:middle}.elementor-widget-image a{show:inline-block}.elementor-widget-image a img[src$=”.svg”]{width:48px}.elementor-widget-image img{vertical-align:center;show:inline-block}
Safety groups want strategic approaches that mix expertise and course of to detect and reply to Indicators of Compromises successfully. A number of built-in methods assist determine and comprise threats quicker when groups wish to scale back dwell time.
Automated Cyber Menace Intelligence Integration
Menace containment begins with easy automation of risk intelligence feeds. Organizations get essential benefits in detection velocity once they routinely ingest and normalize indicators of compromise from a number of sources. Safety groups can match present actions in opposition to identified risk patterns and flag potential matches for investigation or automated response.
Endpoint and Community Telemetry Integration
Community safety knowledge alone doesn’t present sufficient visibility for contemporary threats. A mixture of endpoint and community telemetry creates a whole image of potential compromise. Endpoint telemetry reveals course of injections, PowerShell abuse, and different fileless malware methods that community monitoring may miss. Community telemetry captures communication patterns that endpoint detection may overlook. These knowledge sources assist safety groups determine suspicious exercise earlier within the cyber kill chain. This built-in telemetry strategy supplies the context to tell apart real threats from benign actions.
Whereas automation and telemetry are key pillars, Fidelis Deception can add one other essential layer to real-time IOC detection.
Automated Response and Containment Playbooks
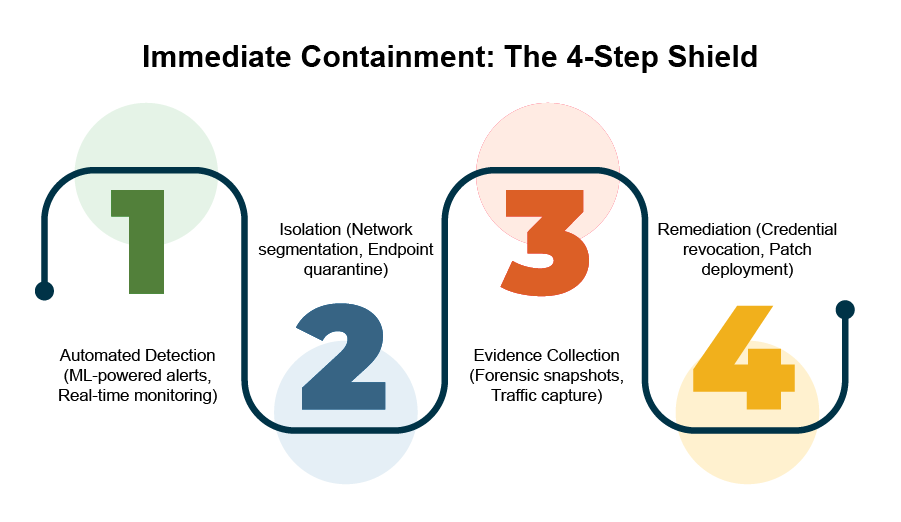
Swift containment prevents lateral motion and limits harm after risk detection. Automated response playbooks change this course of from hours to minutes by executing predefined actions with out guide intervention. Efficient playbooks usually embody:
- Isolation of affected techniques from essential networks
- Blocking of malicious IP addresses and weird domains
- Revocation of compromised credentials
- Assortment of forensic proof for investigation
These simplified processes steadiness velocity with acceptable human oversight to make sure containment actions match risk severity. Nicely-designed playbooks assist safety groups reply to threats at machine velocity when you retain management over containment choices.
Fast Containment Methods
Organizations simply want strategic approaches to comprise threats with out disrupting enterprise operations. Safety groups should arrange response frameworks that steadiness fast motion with accuracy throughout incidents.
Constructing your IOC detection staff construction
A well-defined staff construction with specialised roles makes indicators of compromise (IOC) detection work higher. A tiered analyst system works finest—Tier 1 handles monitoring, Tier 2 takes care of investigations, and Tier 3 focuses on superior risk searching. This setup will give a transparent path for points to maneuver up the chain whereas making the very best use of everybody’s expertise. Fidelis Safety suggests central administration mixed with spread-out response groups to help operations worldwide.
ML-based Alert Prioritization
Alert fatigue stays the most important drawback for safety groups. Machine studying algorithms assist by discovering patterns in previous alert knowledge to chop down false alarms. The system can rank alerts by how critical they’re, how a lot they have an effect on enterprise, and which belongings they aim. This lets analysts deal with actual threats. Fidelis Elevate® XDR makes use of good ML algorithms to chop by means of the noise and spot real safety points.
Community segmentation as a primary response
Community segmentation stops risk actors from transferring sideways by means of your techniques immediately. Networks with correct segments hold threats from transferring previous the place they first received in. This methodology retains knowledge breaches or safety occasions caught in particular areas. Groups can reply quicker as a result of they will see precisely which zones are affected.
Endpoint isolation protocols
Fast endpoint isolation turns into important as soon as a system reveals indicators of compromise. Good isolation protocols can reduce off contaminated gadgets however nonetheless allow you to watch what’s occurring. Fidelis Elevate® lets groups isolate Home windows techniques selectively, to allow them to comprise threats whereas protecting enterprise working.
Designing automated containment workflows
Good containment wants examined response playbooks that spell every little thing out beforehand. These automated techniques ought to record precise steps to isolate, accumulate proof, and repair points. Response occasions get for much longer with out these techniques, which suggests extra harm can occur.
Balancing automated vs. human-driven response
Human judgment issues simply as a lot as automation. Automated techniques deal with routine threats whereas safety groups sort out advanced circumstances. This combine makes use of expertise’s velocity however retains human perception accessible for tough conditions that want context to know correctly.
How Fidelis Prolonged Detection and Response can Assist
Deep visibility throughout endpoint, community, cloud, and deception layers
Fidelis Elevate® provides you unmatched visibility by analyzing telemetry from endpoints, networks, cloud environments, and deception applied sciences directly. This multi-layered viewpoint displays each assault vector, no matter their origin.
The platform relates seemingly unconnected indicators of compromise all through your digital world. These indicators map to the MITRE ATT&CK® framework and supply helpful context. This connection is a good way to get insights when risk actors attempt to conceal their suspicious actions throughout a number of techniques—a tactic that normally defeats siloed safety instruments.
Automated incident response by way of Fidelis Endpoint Detection and Response
Fast risk containment wants automation, which Fidelis Elevate® delivers by means of its built-in elements. Fidelis Endpoint® watches system for suspicious actions and isolates compromised techniques earlier than threats unfold. Fidelis Community® examines packets deeply to identify command-and-control communications and knowledge theft makes an attempt up-to-the-minute.
These elements allow full automated responses:
- Fast endpoint isolation with out dropping visibility
- Automated blocking of malicious community connections
- Proof assortment for each instant response and future digital forensic knowledge evaluation
Integration with risk intel feeds and deception applied sciences
Fidelis Elevate® enhances indicators of compromise (IOC) detection by merging with exterior risk intelligence sources. This characteristic retains your protection mechanisms prepared in opposition to new threats.
The platform makes use of deception applied sciences to put convincing decoys all through your surroundings. These decoys act as early-warning tripwires. They alert safety groups to attacker presence and reveal their ways, methods, and procedures. This info turns into precious intelligence that strengthens your general safety posture.
Conclusion
Fast IOC detection serves as an important protect in opposition to fashionable cyber threats. Our staff at Fidelis Safety is aware of that profitable risk containment wants easy integration of automated risk detection, fast response capabilities, and full visibility in all safety layers.
Fidelis Elevate® XDR tackles widespread Indicators of Compromise detection points by bringing collectively endpoint, community, and cloud safety. The platform’s automated response options reduce down containment occasions when you retain management of human oversight. ML-based alert prioritization helps safety groups utilizing Fidelis Elevate® deal with actual cyber threats as a substitute of false positives.
Safety groups trying to enhance their IOC detection and response ought to bear in mind these factors:
- Automated risk intelligence integration hastens risk detection
- Endpoint and community telemetry working collectively provides full visibility
- Prepared-to-use response playbooks permit fast containment
- The correct mix of automation and human oversight results in higher response
- Unified risk detection
- Actual-time response
- Constructed-in deception
The submit IOC Detection and Response: Methods for Fast Menace Containment appeared first on Fidelis Safety.




