One of the infamous suppliers of abuse-friendly “bulletproof” website hosting for cybercriminals has began routing its operations by networks run by the Russian antivirus and safety agency Kaspersky Lab, KrebsOnSecurity has discovered.
Safety consultants say the Russia-based service supplier Prospero OOO (the triple O is the Russian model of “LLC”) has lengthy been a persistent supply of malicious software program, botnet controllers, and a torrent of phishing web sites. Final yr, the French safety agency Intrinsec detailed Prospero’s connections to bulletproof companies marketed on Russian cybercrime boards beneath the names Securehost and BEARHOST.
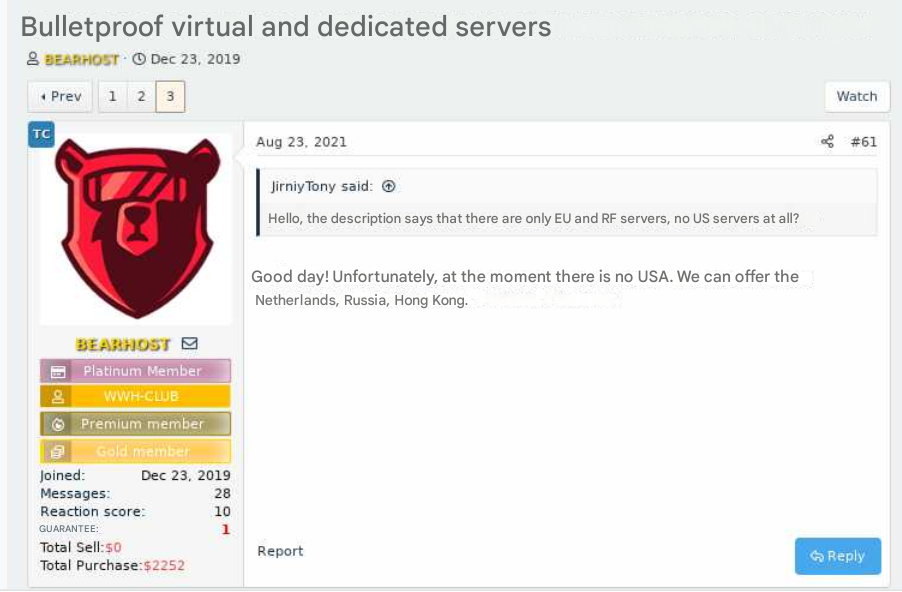
The bulletproof internet hosting supplier BEARHOST. This screenshot has been machine-translated from Russian. Picture: Ke-la.com.
Bulletproof hosts are so named after they earn or domesticate a repute for ignoring authorized calls for and abuse complaints. And BEARHOST has been cultivating its repute since at the least 2019.
“Should you want a server for a botnet, for malware, brute, scan, phishing, fakes and another duties, please contact us,” BEARHOST’s advert on one discussion board advises. “We utterly ignore all abuses with out exception, together with SPAMHAUS and different organizations.”
Intrinsec discovered Prospero has courted a few of Russia’s nastiest cybercrime teams, internet hosting management servers for a number of ransomware gangs over the previous two years. Intrinsec mentioned its evaluation confirmed Prospero often hosts malware operations comparable to SocGholish and GootLoader, that are unfold primarily by way of faux browser updates on hacked web sites and infrequently lay the groundwork for extra severe cyber intrusions — together with ransomware.
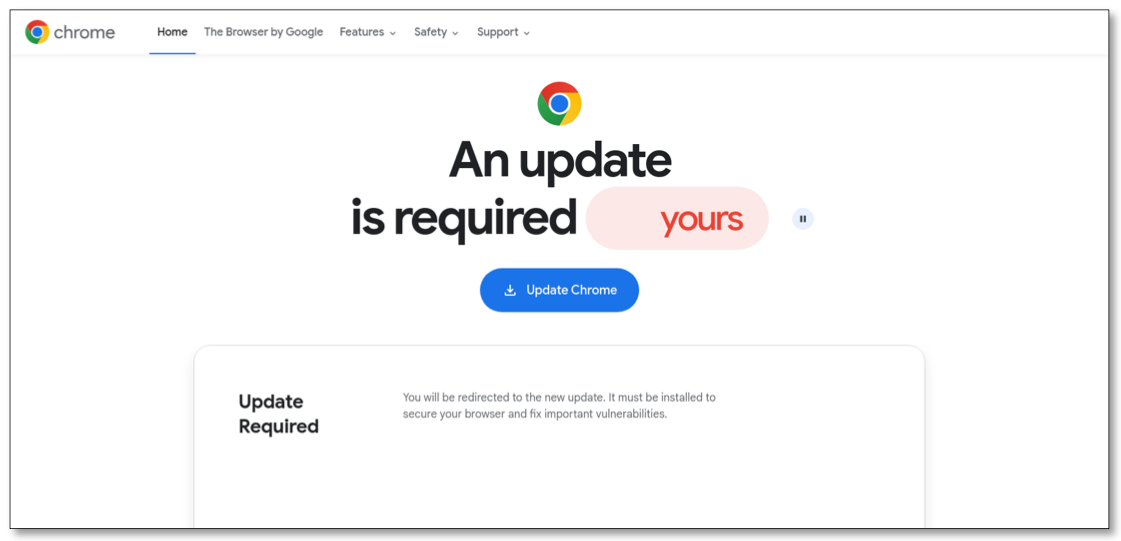
A faux browser replace web page pushing cell malware. Picture: Intrinsec.
BEARHOST prides itself on the flexibility to evade blocking by Spamhaus, a corporation that many Web service suppliers around the globe depend on to assist establish and block sources of malware and spam. Earlier this week, Spamhaus mentioned it observed that Prospero was out of the blue connecting to the Web by routing by networks operated by Kaspersky Lab in Moscow.
Replace, March 1, 9:43 a.m. ET: In a written assertion, Kaspersky mentioned it’s conscious of the general public declare concerning the firm allegedly offering companies to a “bulletproof” website hosting supplier. Right here is their full assertion:
“Kaspersky denies these claims as the corporate doesn’t work and has by no means labored with the service supplier in query. The routing by networks operated by Kaspersky doesn’t by default imply provision of the corporate’s companies, as Kaspersky’s computerized system (AS) path may seem as a technical prefix within the community of telecom suppliers the corporate works with and gives its DDoS companies.”
“Kaspersky pays nice consideration to conducting enterprise ethically and making certain that its options are used for his or her authentic function of offering cybersecurity safety. The corporate is at present investigating the state of affairs to tell the corporate whose community may have served as a transit for a “bulletproof” website hosting supplier in order that the previous takes the mandatory measures.”
Kaspersky started promoting antivirus and safety software program in the US in 2005, and the corporate’s malware researchers have earned accolades from the safety neighborhood for a lot of vital discoveries over time. However in September 2017, the Division of Homeland Safety (DHS) barred U.S. federal companies from utilizing Kaspersky software program, mandating its elimination inside 90 days.
Cybersecurity reporter Kim Zetter notes that DHS didn’t cite any particular justification for its ban in 2017, however media reviews quoting nameless authorities officers referenced two incidents. Zetter wrote:
In line with one story, an NSA contractor growing offensive hacking instruments for the spy company had Kaspersky software program put in on his dwelling pc the place he was growing the instruments, and the software program detected the supply code as malicious code and extracted it from his pc, as antivirus software program is designed to do. A second story claimed that Israeli spies caught Russian authorities hackers utilizing Kaspersky software program to look buyer methods for recordsdata containing U.S. secrets and techniques.
Kaspersky denied that anybody used its software program to seek for secret info on buyer machines and mentioned that the instruments on the NSA employee’s machine had been detected in the identical means that each one antivirus software program detects recordsdata it deems suspicious after which quarantines or extracts them for evaluation. As soon as Kaspersky found that the code its antivirus software program detected on the NSA employee’s machine weren’t malicious packages however supply code in growth by the U.S. authorities for its hacking operations, CEO Eugene Kaspersky says he ordered employees to delete the code.
Final yr, the U.S. Commerce Division banned the sale of Kaspersky software program within the U.S. efficient July 20, 2024. U.S. officers argued the ban was wanted as a result of Russian regulation requires home corporations to cooperate in all official investigations, and thus the Russian authorities may pressure Kaspersky to secretly collect intelligence on its behalf.
Phishing knowledge gathered final yr by the Interisle Consulting Group ranked internet hosting networks by their measurement and focus of spambot hosts, and discovered Prospero had a better spam rating than another supplier by far.

AS209030, owned by Kaspersky Lab, is offering connectivity to the bulletproof host Prospero (AS200593). Picture: cidr-report.org.
It stays unclear why Kaspersky is offering transit to Prospero. Doug Madory, director of Web evaluation at Kentik, mentioned routing information present the connection between Prospero and Kaspersky began at first of December 2024.
Madory mentioned Kaspersky’s community seems to be internet hosting a number of monetary establishments, together with Russia’s largest — Alfa-Financial institution. Kaspersky sells companies to assist defend clients from distributed denial-of-service (DDoS) assaults, and Madory mentioned it may very well be that Prospero is just buying that safety from Kaspersky.
But when that’s the case, it doesn’t make the state of affairs any higher, mentioned Zach Edwards, a senior menace researcher on the safety agency Silent Push.
“In some methods, offering DDoS safety to a widely known bulletproof internet hosting supplier could also be even worse than simply permitting them to hook up with the remainder of the Web over your infrastructure,” Edwards mentioned.
One of the infamous suppliers of abuse-friendly “bulletproof” website hosting for cybercriminals has began routing its operations by networks run by the Russian antivirus and safety agency Kaspersky Lab, KrebsOnSecurity has discovered.
Safety consultants say the Russia-based service supplier Prospero OOO (the triple O is the Russian model of “LLC”) has lengthy been a persistent supply of malicious software program, botnet controllers, and a torrent of phishing web sites. Final yr, the French safety agency Intrinsec detailed Prospero’s connections to bulletproof companies marketed on Russian cybercrime boards beneath the names Securehost and BEARHOST.

The bulletproof internet hosting supplier BEARHOST. This screenshot has been machine-translated from Russian. Picture: Ke-la.com.
Bulletproof hosts are so named after they earn or domesticate a repute for ignoring authorized calls for and abuse complaints. And BEARHOST has been cultivating its repute since at the least 2019.
“Should you want a server for a botnet, for malware, brute, scan, phishing, fakes and another duties, please contact us,” BEARHOST’s advert on one discussion board advises. “We utterly ignore all abuses with out exception, together with SPAMHAUS and different organizations.”
Intrinsec discovered Prospero has courted a few of Russia’s nastiest cybercrime teams, internet hosting management servers for a number of ransomware gangs over the previous two years. Intrinsec mentioned its evaluation confirmed Prospero often hosts malware operations comparable to SocGholish and GootLoader, that are unfold primarily by way of faux browser updates on hacked web sites and infrequently lay the groundwork for extra severe cyber intrusions — together with ransomware.

A faux browser replace web page pushing cell malware. Picture: Intrinsec.
BEARHOST prides itself on the flexibility to evade blocking by Spamhaus, a corporation that many Web service suppliers around the globe depend on to assist establish and block sources of malware and spam. Earlier this week, Spamhaus mentioned it observed that Prospero was out of the blue connecting to the Web by routing by networks operated by Kaspersky Lab in Moscow.
Replace, March 1, 9:43 a.m. ET: In a written assertion, Kaspersky mentioned it’s conscious of the general public declare concerning the firm allegedly offering companies to a “bulletproof” website hosting supplier. Right here is their full assertion:
“Kaspersky denies these claims as the corporate doesn’t work and has by no means labored with the service supplier in query. The routing by networks operated by Kaspersky doesn’t by default imply provision of the corporate’s companies, as Kaspersky’s computerized system (AS) path may seem as a technical prefix within the community of telecom suppliers the corporate works with and gives its DDoS companies.”
“Kaspersky pays nice consideration to conducting enterprise ethically and making certain that its options are used for his or her authentic function of offering cybersecurity safety. The corporate is at present investigating the state of affairs to tell the corporate whose community may have served as a transit for a “bulletproof” website hosting supplier in order that the previous takes the mandatory measures.”
Kaspersky started promoting antivirus and safety software program in the US in 2005, and the corporate’s malware researchers have earned accolades from the safety neighborhood for a lot of vital discoveries over time. However in September 2017, the Division of Homeland Safety (DHS) barred U.S. federal companies from utilizing Kaspersky software program, mandating its elimination inside 90 days.
Cybersecurity reporter Kim Zetter notes that DHS didn’t cite any particular justification for its ban in 2017, however media reviews quoting nameless authorities officers referenced two incidents. Zetter wrote:
In line with one story, an NSA contractor growing offensive hacking instruments for the spy company had Kaspersky software program put in on his dwelling pc the place he was growing the instruments, and the software program detected the supply code as malicious code and extracted it from his pc, as antivirus software program is designed to do. A second story claimed that Israeli spies caught Russian authorities hackers utilizing Kaspersky software program to look buyer methods for recordsdata containing U.S. secrets and techniques.
Kaspersky denied that anybody used its software program to seek for secret info on buyer machines and mentioned that the instruments on the NSA employee’s machine had been detected in the identical means that each one antivirus software program detects recordsdata it deems suspicious after which quarantines or extracts them for evaluation. As soon as Kaspersky found that the code its antivirus software program detected on the NSA employee’s machine weren’t malicious packages however supply code in growth by the U.S. authorities for its hacking operations, CEO Eugene Kaspersky says he ordered employees to delete the code.
Final yr, the U.S. Commerce Division banned the sale of Kaspersky software program within the U.S. efficient July 20, 2024. U.S. officers argued the ban was wanted as a result of Russian regulation requires home corporations to cooperate in all official investigations, and thus the Russian authorities may pressure Kaspersky to secretly collect intelligence on its behalf.
Phishing knowledge gathered final yr by the Interisle Consulting Group ranked internet hosting networks by their measurement and focus of spambot hosts, and discovered Prospero had a better spam rating than another supplier by far.

AS209030, owned by Kaspersky Lab, is offering connectivity to the bulletproof host Prospero (AS200593). Picture: cidr-report.org.
It stays unclear why Kaspersky is offering transit to Prospero. Doug Madory, director of Web evaluation at Kentik, mentioned routing information present the connection between Prospero and Kaspersky began at first of December 2024.
Madory mentioned Kaspersky’s community seems to be internet hosting a number of monetary establishments, together with Russia’s largest — Alfa-Financial institution. Kaspersky sells companies to assist defend clients from distributed denial-of-service (DDoS) assaults, and Madory mentioned it may very well be that Prospero is just buying that safety from Kaspersky.
But when that’s the case, it doesn’t make the state of affairs any higher, mentioned Zach Edwards, a senior menace researcher on the safety agency Silent Push.
“In some methods, offering DDoS safety to a widely known bulletproof internet hosting supplier could also be even worse than simply permitting them to hook up with the remainder of the Web over your infrastructure,” Edwards mentioned.






