The shape and quiz-building instrument is a well-liked vector for social engineering and malware. Right here’s how you can keep protected.
23 Apr 2025
•
,
5 min. learn

When Google enters a selected market, it typically means dangerous information for the incumbents. So it was with Google Varieties, the tech large’s type and quiz-building instrument that launched in 2008. In response to one estimate, it now has a market share of practically 50%.
Nevertheless, with nice market share comes larger scrutiny from nefarious parts. Menace actors are previous masters at abusing in style expertise for their very own ends. And they’re doing so with Google Varieties to harvest delicate data from their victims and even trick them into putting in malware.
Why Google Varieties?
Malicious actors are all the time searching for methods so as to add legitimacy to scams and evade electronic mail safety filters. Google Varieties presents an excellent alternative to do each. It’s favored by cybercriminals as a result of it’s:
- Free, that means risk actors can launch campaigns at scale with a doubtlessly profitable return on their funding
- Trusted by customers, which will increase the possibilities of victims believing that the Google Type they’re being despatched or redirected to is reliable
- A reliable service, that means that malicious Google Varieties and hyperlinks to malicious types are sometimes waved by way of by conventional electronic mail safety instruments
- Simple to make use of, which is sweet for customers but in addition useful for cybercriminals – that means they’ll launch convincing phishing campaigns with little or no effort or prior data of the instrument
- Cybercriminals additionally make the most of the truth that Google Varieties communications are encrypted with TLS, which can make it more durable for safety instruments to look in and examine for any malicious exercise. Equally, the answer typically makes use of dynamic URLs, which can make it difficult for some electronic mail safety filters to identify malicious types.
What do Google Varieties assaults appear like?
Most Google Varieties threats use the instrument to trick customers into handing over their private and monetary data, though there are slight variations on how risk actors obtain this. Listed below are among the primary strategies to look out for:
Phishing-related types
Menace actors create Google Varieties designed to spoof reliable manufacturers, similar to log-in pages for social media websites, banks and universities, and even fee pages. As talked about, the benefit for the dangerous guys is that it’s faster, simpler and cheaper to take action than construct a devoted phishing website, and fewer more likely to be blocked by safety filters.
Usually, you’ll obtain a hyperlink to certainly one of these malicious Google Varieties through a phishing electronic mail, which itself could also be spoofed to impersonate a reliable model or sender. The e-mail might even come from a reliable account that has been hijacked. Both approach, the top aim is normally to:
- Harvest your log-ins, which may then be used to hijack accounts and commit id fraud
- Steal your card particulars or banking/crypto data with the intention to take over these accounts and drain them of funds or commit fee fraud
- Persuade you to click on on a hyperlink within the malicious Google Type that redirects you to a website which covertly installs malware in your machine
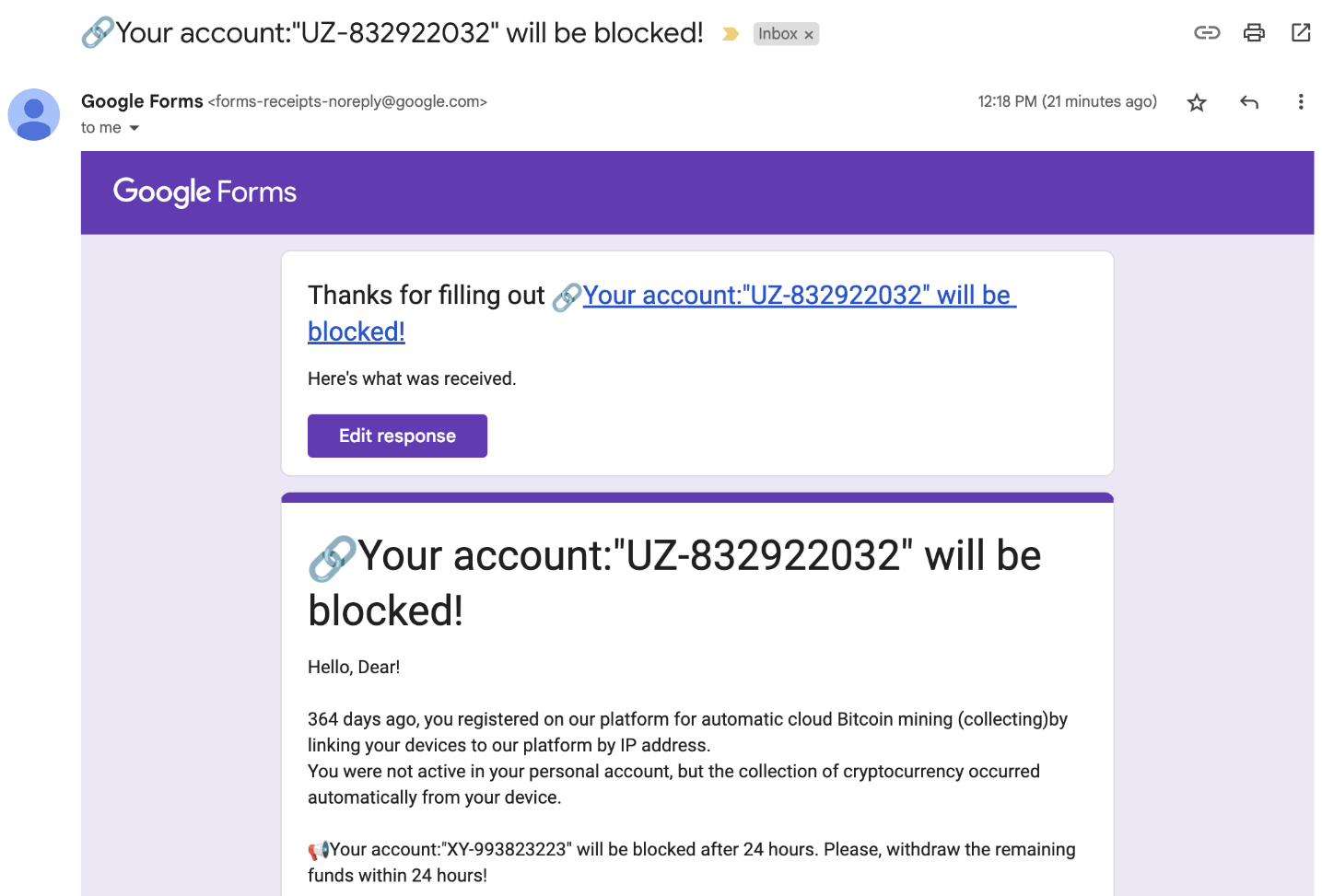
Name again phishing
Attackers ship you a malicious Google Type crafted to trick you into calling a cellphone quantity listed on it. The shape could also be spoofed to seem as if despatched from a financial institution or different trusted service supplier. A way of urgency is created to rush you into making a rash choice – calling the quantity with out pondering issues by way of first. Usually the shape will state that your account might be blocked or that cash was taken (or might be taken out of your account) until you get in contact.
When you name again, you’ll be chatting with a member of a voice phishing (vishing) gang that makes use of appeal to persuade you into handing over private and monetary data. They might additionally counsel downloading distant entry software program to your machine, which might give them full management over your laptop.
Quiz spam
Cybercriminals may abuse the quiz function in Google Varieties – by making a quiz and including your electronic mail handle. Hitting “launch scores” will generate a message which the risk actor can customise – presumably including hyperlinks to phishing, malware or rip-off websites.
Assaults within the wild
Among the many real-world campaigns safety researchers have seen lately are:
BazarCall
A vishing-type risk wherein victims obtained an electronic mail containing a malicious Google Type impersonating PayPal, Netflix, or certainly one of a number of different big-name manufacturers. The shape contained particulars of a pretend cost which is about to be utilized, until the recipient calls the cellphone quantity equipped.
Phishing focusing on US universities
Google detected a rise in assaults on the US schooling sector final yr. Victims obtained phishing emails containing a hyperlink to a malicious Google Type. Each the preliminary electronic mail and type had been spoofed to seem as if despatched by the college, by that includes logos, mascots and references to the college identify. The top aim was to reap logins and/or monetary particulars.
Protecting your defenses up
Consciousness is half the battle on the subject of mitigating the impression of social engineering threats like this. Now that you know the way the dangerous guys function, it ought to be more durable for them to trick you into making dangerous decisions on-line. To maintain Google Type threats at bay, contemplate the next:
- Use multi-layered safety software program from a good supplier on all computer systems and cell units. It will assist to make sure that, even should you click on on a malicious hyperlink, the malware obtain might be blocked. Good software program may also spot suspicious patterns, even when the Google Type itself seems reliable, in addition to scan your machine/system periodically and maintain you protected from something malicious.
- Keep alert to potential phishing scams. You shouldn’t belief something unsolicited which asks you to click on on a hyperlink or name a quantity urgently. As an alternative, take a deep breath, loosen up, and call the sender individually; not through the quantity or hyperlink supplied. One other helpful tactic is to hover over hyperlinks to examine the true vacation spot. Be certain your electronic mail safety answer
- Improve safety at log-in by utilizing robust, distinctive passwords for each account, saved in a password supervisor for simple recall. Then change on multi-factor authentication (MFA) for each account you utilize on-line. Because of this, even when hackers pay money for your password, they’ll’t entry your account. A hardware-based safety key or an authenticator app is finest.
- Concentrate: Google all the time shows a warning on Google Varieties, telling recipients “By no means submit passwords by way of Google Varieties”. Observe its recommendation.
If the worst occurs and also you assume you’ve fallen sufferer to a Google Varieties assault, change your passwords, run a malware scan, and inform your financial institution to freeze any playing cards (should you’ve submitted card particulars). Swap on MFA for all accounts should you’ve not already, and monitor your accounts for any uncommon exercise.
Just by studying this text, you can be in an excellent place on the subject of warding off the risk from malicious Google Varieties. Be skeptical of any unsolicited electronic mail you obtain – even when it’s from a trusted model.







