In September 2020, I created the Getting Packets Throughout the Community video as a part of the How Networks Actually Work webinar. This weblog put up is a Whisper transcript edited by ChatGPT and polished by Yours Really 😉
ChatGPT did an honest job modifying the transcript, however I ponder how far it pushed it towards the AI slop. Your feedback are extremely appreciated. Thanks!
After inspecting the complicated bridging/routing/switching terminology and a short detour into the management/knowledge aircraft particulars, let’s speak about how packets truly transfer throughout a community.
As all the time, issues had been less complicated when networks had been applied with a single cable. In that setup, all nodes had been instantly reachable, and the one problem was determining the vacation spot node’s handle; it didn’t matter whether or not it was a MAC handle, an IP handle, or a Fiber Channel handle. On a single cable, you can simply broadcast, like, “Who has this service?” and somebody would reply, “I’m the printer you’re searching for.” That’s what number of early non-IP protocols operated.
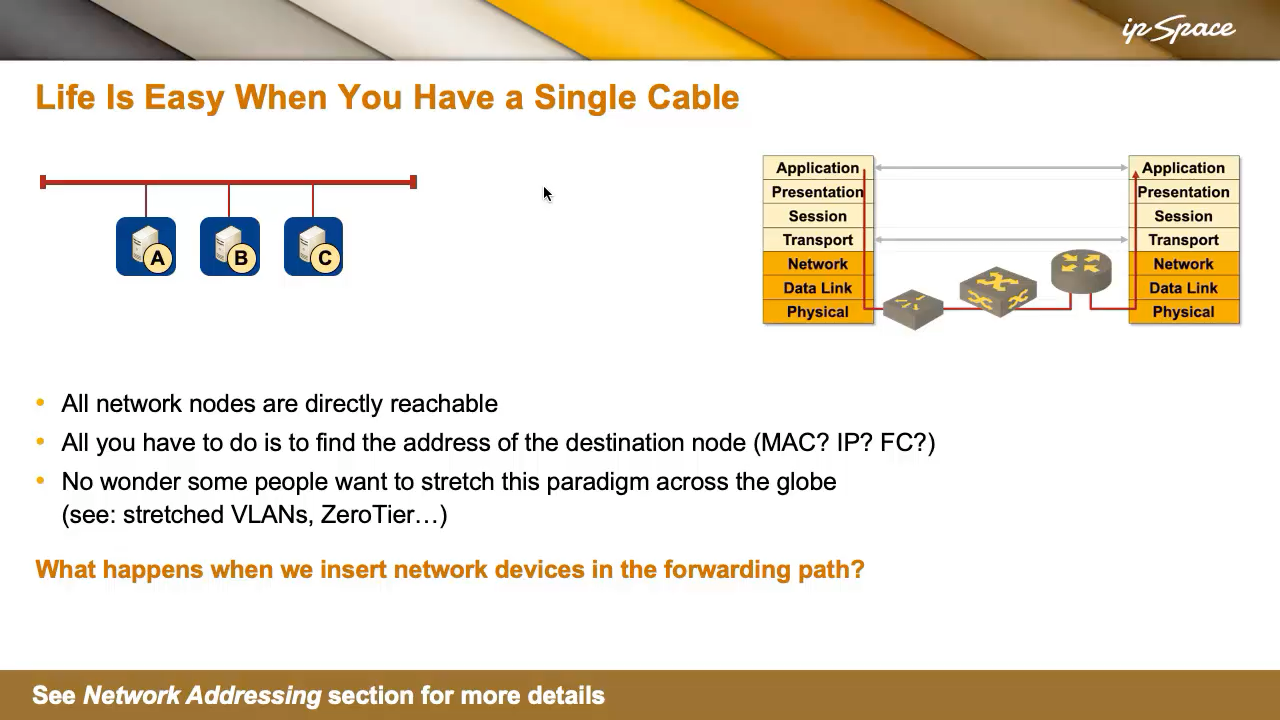
Life on a single cable was easy. You simply plugged issues in, and all of it labored—till it didn’t. No surprise some people needed to stretch that simplicity throughout the globe, leading to distributors singing the praises of stretched VLANs, and Thought Leaders telling you the way to prolong a VLAN into the general public cloud. Some VPN distributors even simulate bridging over a VPN. However let’s not dive into the implications of that simply but—we’ll come again to it when discussing routing versus bridging.
The subject of this weblog put up is less complicated: what occurs once we break that single cable into two and insert a community machine within the forwarding path? How will we nonetheless get packets from A to B now that there’s one thing within the center?
Three basic applied sciences could make that occur, and we’ll study them utilizing a easy community from the next diagram.
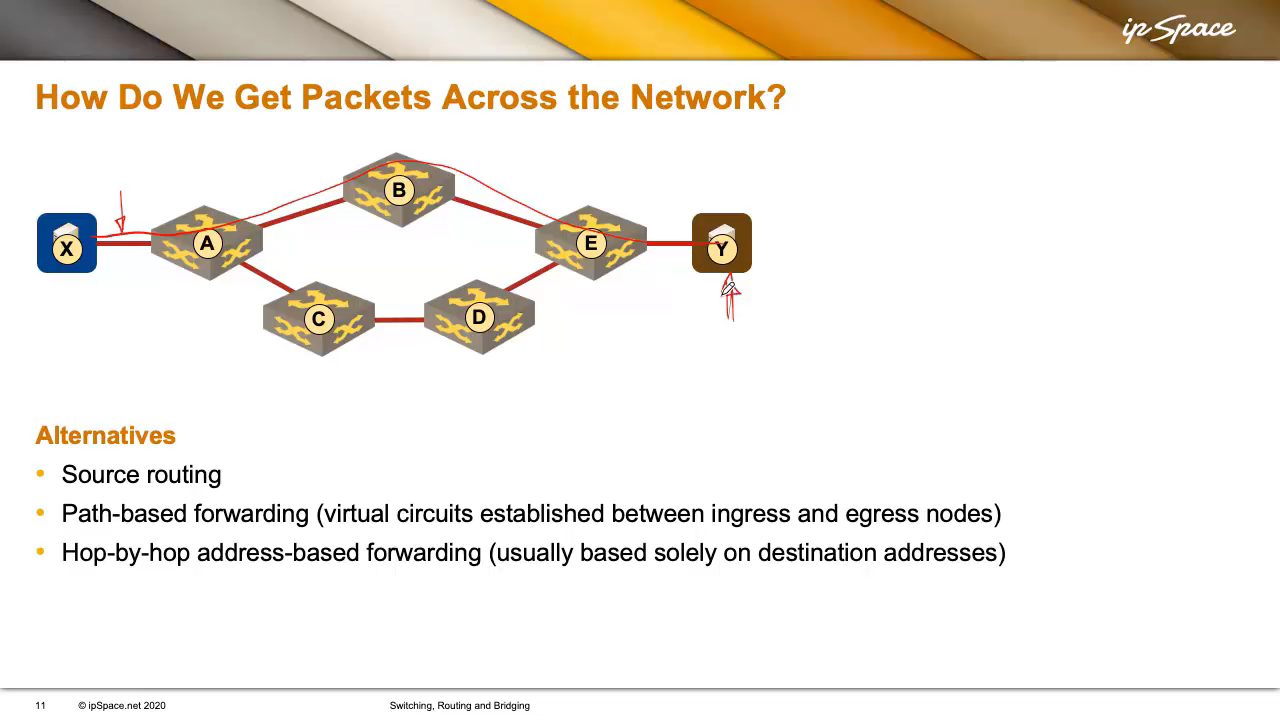
Suppose X is attempting to succeed in Y. X can attain Y through two doable paths: A-B-E or A-C-D-E. So somebody has to determine which path to make use of. These are the generally used choices:
-
Supply Routing: X (by means of some unspecified mechanism) figures out its packets should cross by means of A, B, and E to succeed in Y.
-
Path-Primarily based Forwarding (Digital Circuits) Somebody might arrange a digital hyperlink (or circuit) between X and Y and inform X: “If you wish to ship packets to Y, simply use this digital circuit.” Digital circuits are equal to telephone calls: you dial the quantity, a connection is made, and also you begin speaking.
You might say, “Isn’t that what TCP does at the moment?” and also you’d be proper. However within the previous days, digital circuits had been the solely strategy to talk—till IP got here alongside and stated, “Overlook telephone calls. Networking must be extra like parcel supply.”
-
Hop-By-Hop Vacation spot-Solely Forwarding Think about X is Amazon, and Y is you at house, out of bathroom paper. You order some, specify your handle, and Amazon places collectively a packet and sticks your handle on it. The packet will get handed from one supply individual to the following, with each checking the handle and forwarding it independently. That’s how IP forwarding works: hop-by-hop, with every machine making an unbiased forwarding determination based mostly solely on the vacation spot handle.
Normally, hop-by-hop forwarding is completed purely on the vacation spot handle. However there are extra advanced schemes that additionally contemplate high quality of service, and even the supply handle, to make forwarding choices. These hybrid schemes can ship packets to the identical vacation spot alongside completely different paths (for instance, relying on the supply handle), although that provides loads of complexity and bloats the lookup tables.
Supply Routing
The simplest forwarding mechanism is supply routing (extra exactly, strict supply routing), the place the supply node is aware of the total path to the vacation spot. We’re not but asking how the supply node will get this info (we’ll get to that later); we’re simply specializing in forwarding proper now.
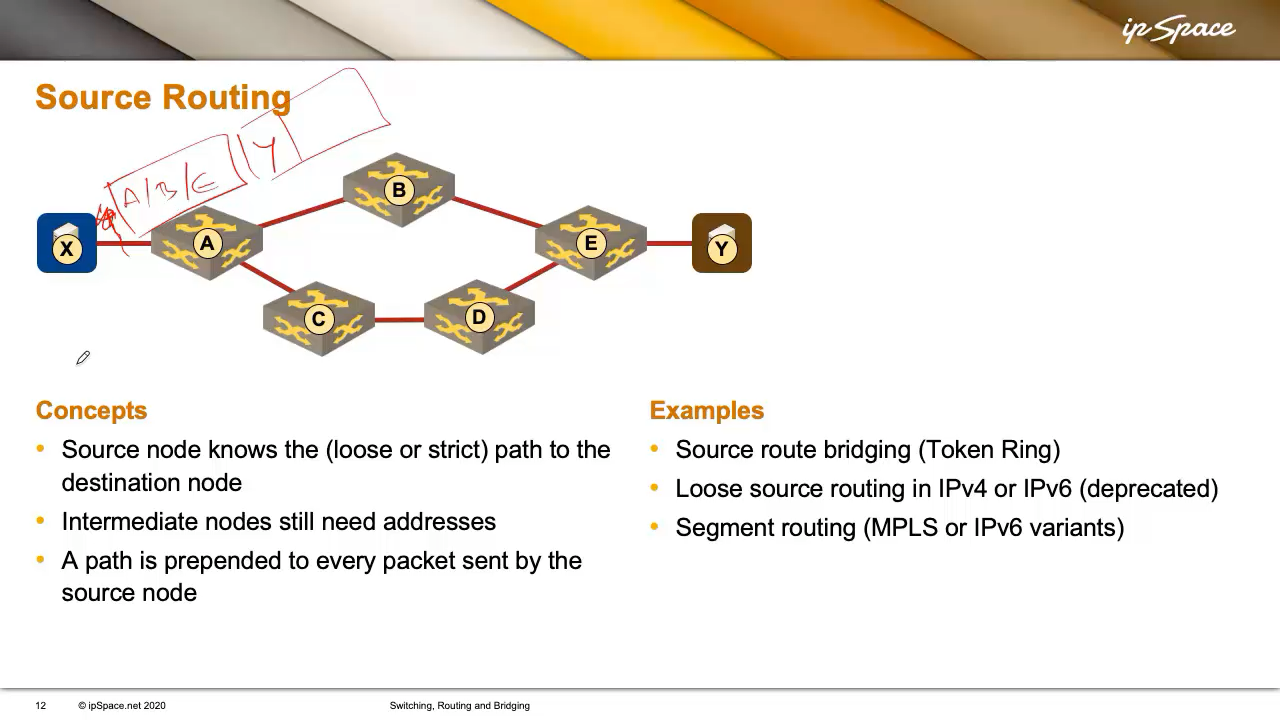
So, the supply (X) is aware of the trail to the vacation spot (Y): by means of A, B, and E. Intermediate nodes would possibly solely know the following hop—A would possibly know the place B is, however not E. So, X prepends a routing header to every packet: “This has to undergo A, B, E.” Each packet will get this routing header.
An fascinating facet impact is that X can use each paths: it would ship some packets through A-B-E and others through A-C-D-E. It might even choose the trail based mostly on visitors kind—voice over one path, internet visitors over the opposite. The choice is fully as much as X.
This concept was first utilized by IBM in Token Ring networks with Supply Route Bridging, the place small rings had been related by bridges. The supply nodes specified the total path to the vacation spot, itemizing all bridges and rings alongside the best way.
One thing comparable existed in each IPv4 and IPv6. It was later deprecated (which in IETF-speak means “we hope it dies, however it most likely gained’t”) on account of critical safety dangers. For instance, an attacker might spoof being a trusted node and use a supply routing header to sneak visitors by means of unauthorized paths. That’s why IPv4 supply routing was disabled, and IPv6 adopted swimsuit years later with robust deprecation language: nodes should not acknowledge supply routing headers.
After all, unhealthy concepts by no means actually die; they simply get reinvented. Enter phase routing, which has two flavors:
- MPLS-based phase routing makes use of MPLS labels to information packets alongside a particular path. It’s a pretty affordable thought and broadly used.
- IPv6-based phase routing makes use of IPv6 addresses as a substitute of labels. It reintroduces a few of the similar spoofing considerations, although proponents declare safety by means of digital signatures. Not everyone seems to be satisfied, and real-world deployments are restricted.
Digital Circuit-Primarily based Forwarding
When networking was new within the ’70s, individuals thought when it comes to voice calls, leading to applied sciences that (identical to a telephone name) established a digital circuit between two endpoints earlier than sending knowledge.
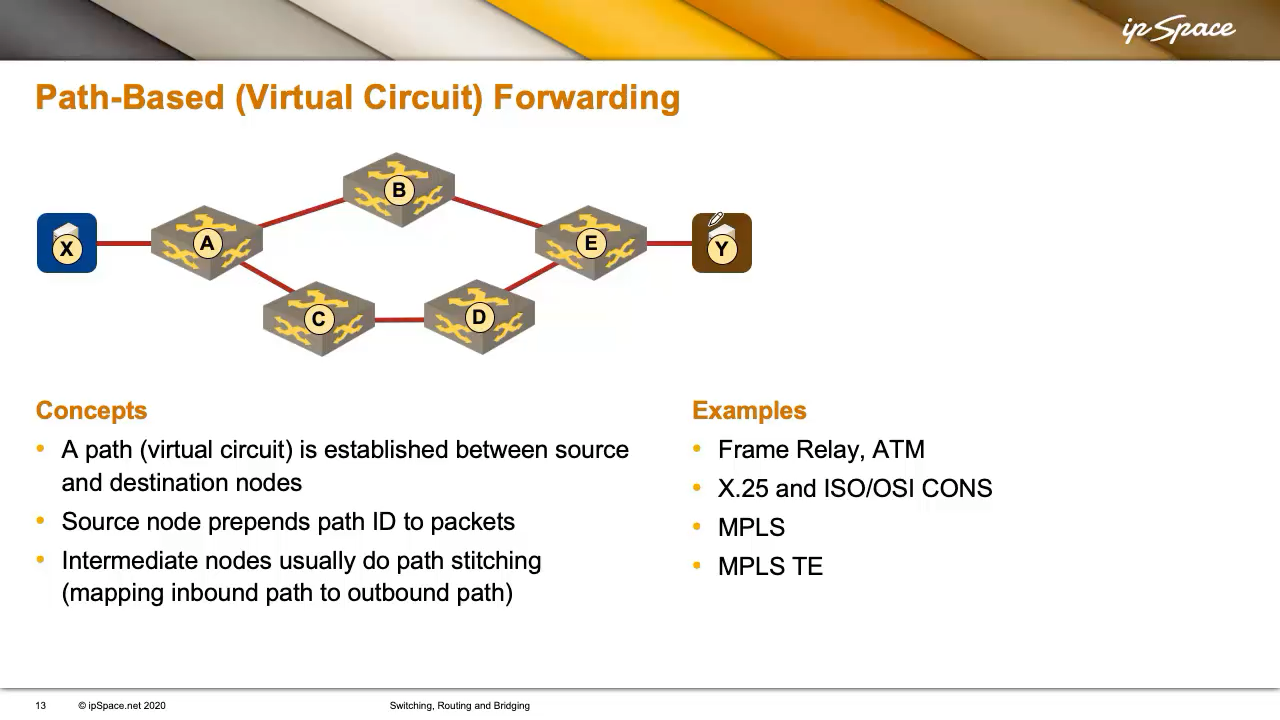
X desires to speak to Y, so a digital circuit is ready up (utilizing a signalling protocol, a central controller, or handbook configuration), and each intermediate node is aware of about it. X then sends packets with a circuit ID as a substitute of a vacation spot handle. The digital circuit ID was referred to as DLCI in Body Relay, and Digital Path/Digital Circuit identifier (VPI/VCI) in ATM.
Bandwidth was costly within the heyday of switched WAN applied sciences, so we wasted as few bits as doable on the digital circuit identifiers. They had been often domestically vital (typically even restricted to a single interface), and the intermediate nodes would construct end-to-end circuits by mapping inbound circuit identifiers into next-hop identifiers. For instance, A would inform X to make use of circuit identifier C, A would map it to C2, B to C3, and so forth. Every node would preserve a neighborhood mapping (e.g., C2 → C3), very like MPLS does at the moment.
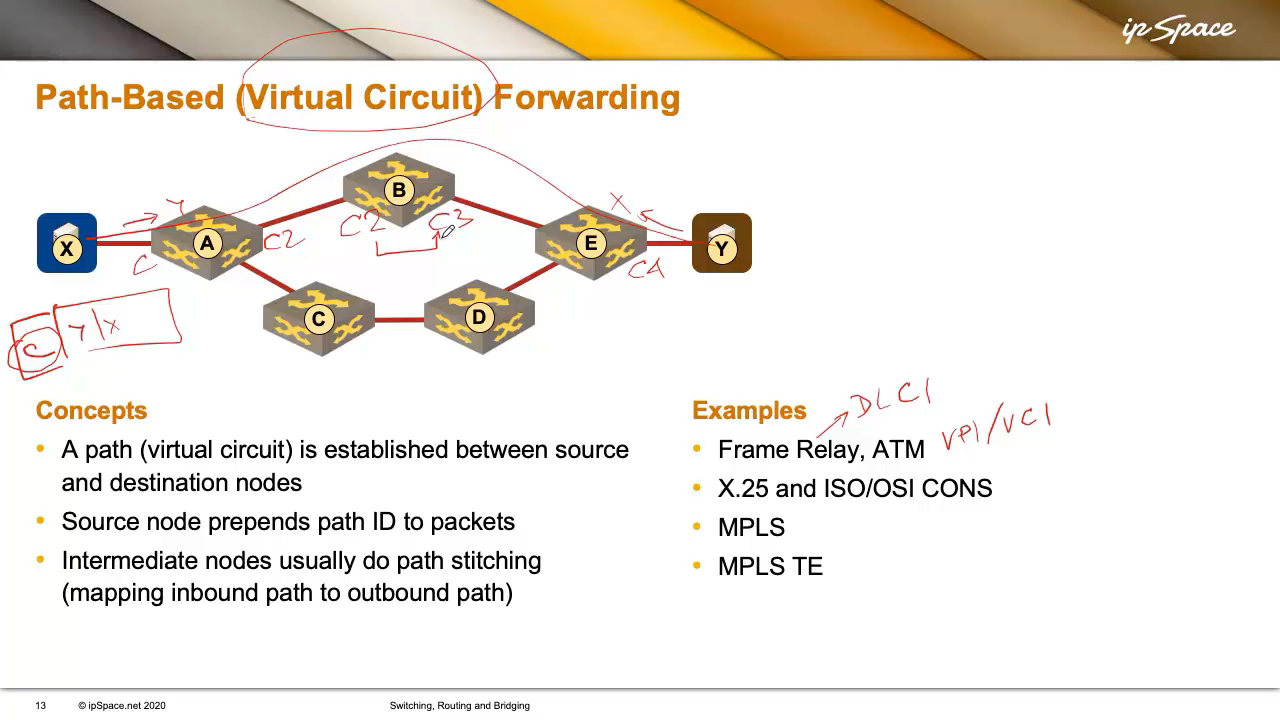
MPLS didn’t come out of nowhere. It was constructed on older concepts like Body Relay, ATM, and X.25. Whereas most of those are gone (besides perhaps at some airport nonetheless utilizing X.25 for check-in machines), MPLS and MPLS-TE are alive and properly.
Hop-by-Hop Forwarding
That is the forwarding methodology most trendy networks use. Every router or change is aware of the way to attain all locations, or makes use of a default route towards a node with extra granular info. Each machine makes an unbiased determination based mostly solely on the vacation spot handle. In our community, X can’t management how A forwards the packet to Y.
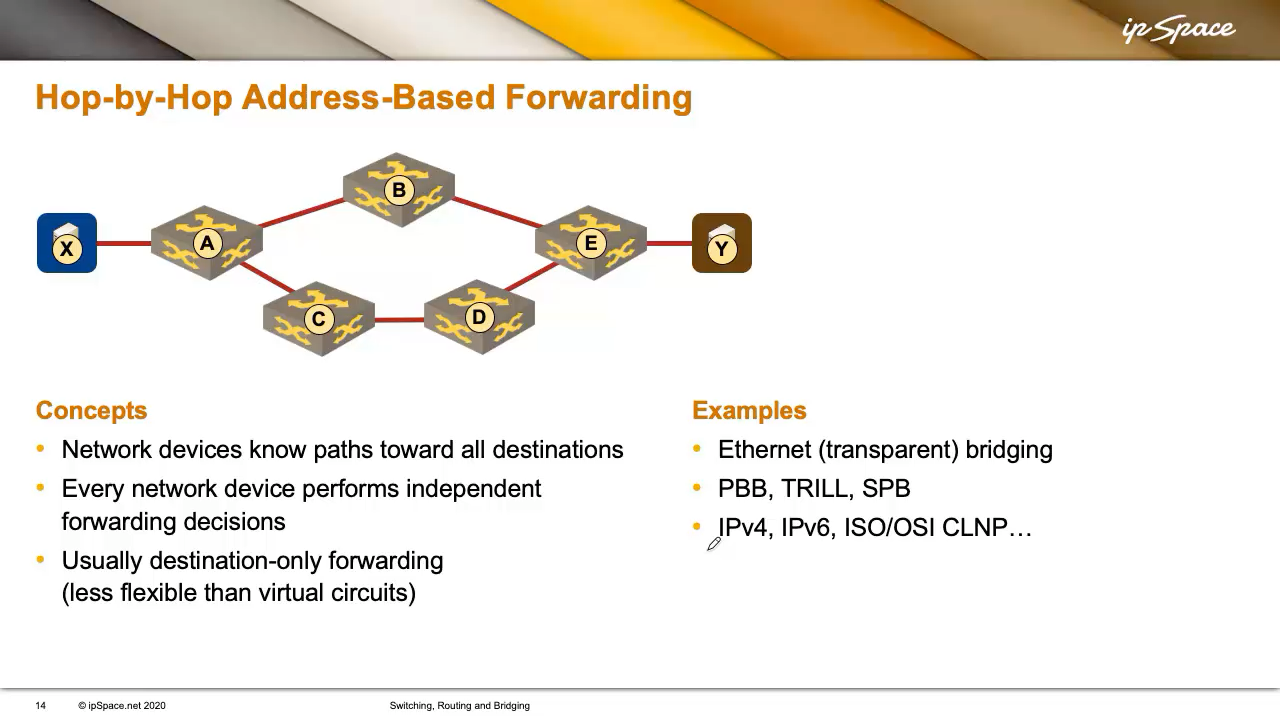
The unbiased native choices make hop-by-hop forwarding much less versatile than digital circuits. In a virtual-circuit world, X might select which path to make use of. In a community utilizing hop-by-hop forwarding, X has no affect on the forwarding path. If A thinks B is the perfect subsequent hop, X can’t change that, even when a greater path exists through C and D.
Applied sciences utilizing this mannequin embrace:
- IPv4 and IPv6
- CLNP (for the three individuals nonetheless operating OSI to handle their SONET/SDH gear)
- Clear bridging
- Extra superior bridging protocols like Supplier Spine Bridging (PBB), TRILL, and SPB



