ESET Analysis analyzes Gamaredon’s up to date cyberespionage toolset, new stealth-focused methods, and aggressive spearphishing operations noticed all through 2024
02 Jul 2025
•
,
6 min. learn
Since Russia’s full-scale invasion of Ukraine in February 2022, cyberespionage has performed a vital position within the broader threatscape. Russia-aligned superior persistent menace (APT) teams have relentlessly focused Ukrainian entities, using cyberattacks alongside disinformation campaigns. ESET Analysis has carefully monitored these actions, recurrently documenting cyber-operations carried out by numerous menace actors, together with the extremely lively Gamaredon group.
Key factors of this blogpost:
- Gamaredon refocused solely on concentrating on Ukrainian governmental establishments in 2024, abandoning prior makes an attempt towards NATO international locations.
- The group considerably elevated the dimensions and frequency of spearphishing campaigns, using new supply strategies akin to malicious hyperlinks and LNK recordsdata executing PowerShell from Cloudflare-hosted domains.
- Gamaredon launched six new malware instruments, leveraging PowerShell and VBScript, designed primarily for stealth, persistence, and lateral motion.
- Present instruments obtained main upgrades, together with enhanced obfuscation, improved stealth techniques, and complicated strategies for lateral motion and information exfiltration.
- Gamaredon operators managed to cover nearly their complete C&C infrastructure behind Cloudflare tunnels.
- Gamaredon more and more relied on third-party providers (Telegram, Telegraph, Cloudflare, Dropbox) and DNS-over-HTTPS (DoH) for shielding its C&C infrastructure.
In our earlier blogpost, Cyberespionage the Gamaredon manner: Evaluation of toolset used to spy on Ukraine in 2022 and 2023, we described Gamaredon’s aggressive cyberespionage actions towards Ukrainian governmental establishments. As a part of our continued investigation, we’ve carried out an intensive technical evaluation of Gamaredon’s operations all through 2024. The detailed outcomes and technical insights can be found in our newest white paper.
Our analysis reveals that the group stays extremely lively, persistently concentrating on Ukraine, however has notably tailored its techniques and instruments.
Focusing on Ukraine solely
Gamaredon, attributed by the Safety Service of Ukraine (SSU) to the 18th Middle of Data Safety of Russia’s Federal Safety Service (FSB), has focused Ukrainian governmental establishments since at the very least 2013. Whereas earlier years noticed occasional makes an attempt towards targets in different NATO international locations, throughout 2024 Gamaredon operators returned their focus solely to Ukrainian establishments.
This strongly aligns with the group’s historic goal as a cyberespionage actor aligned with Russian geopolitical pursuits. Given the continued battle and geopolitical tensions, we count on Gamaredon’s concentrating on of Ukraine to proceed unchanged within the foreseeable future.
Spearphishing campaigns develop bigger and extra frequent
Gamaredon’s spearphishing actions considerably intensified throughout the second half of 2024. Campaigns usually lasted one to 5 consecutive days, with emails containing malicious archives (RAR, ZIP, 7z) or XHTML recordsdata using HTML smuggling methods. These recordsdata delivered malicious HTA or LNK recordsdata that executed embedded VBScript downloaders akin to PteroSand. Determine 1 depicts the variety of distinctive samples of these HTA and LNK recordsdata delivered per thirty days in Gamaredon spearphishing campaigns in 2024.
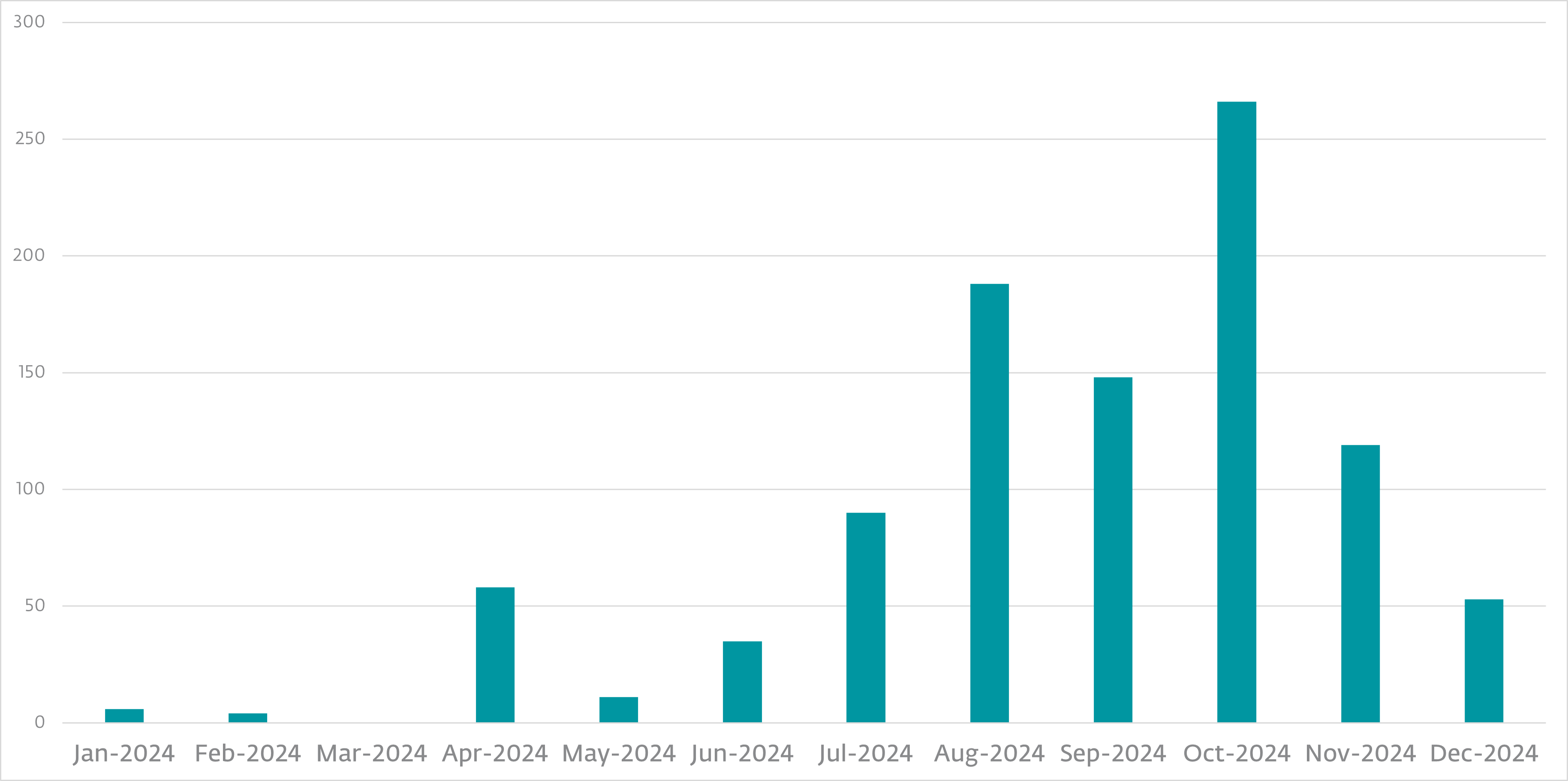
Surprisingly, in October 2024, we noticed a uncommon case the place spearphishing emails included malicious hyperlinks fairly than attachments – a deviation from Gamaredon’s standard techniques. Moreover, Gamaredon launched one other novel approach: utilizing malicious LNK recordsdata to execute PowerShell instructions straight from Cloudflare-generated domains, bypassing some conventional detection mechanisms.
Toolset evolution: New instruments and vital enhancements
Gamaredon’s toolset underwent notable updates. Whereas fewer new instruments have been launched (six in comparison with eight in 2022 and 9 in 2023), substantial assets went into updating and enhancing current instruments:
New instruments launched in 2024 embody:
- PteroDespair: A brief-lived PowerShell reconnaissance device found in January 2024, developed to gather diagnostic information on beforehand deployed malware.
- PteroTickle: A PowerShell weaponizer found in March 2024, concentrating on Python functions transformed into executables on fastened and detachable drives, facilitating lateral motion. It weaponizes Tcl scripts usually present in Python GUI apps utilizing Tkinter and constructed with PyInstaller.
- PteroGraphin: Found in August 2024, this PowerShell device initially used an unusual persistence technique involving Microsoft Excel add-ins. It creates an encrypted communication channel for payload supply, by the Telegraph API. Later variations simplified persistence by utilizing scheduled duties as a substitute.
- PteroStew: A brand new general-purpose VBScript downloader found in October 2024, much like beforehand recognized downloaders (e.g., PteroSand, PteroRisk), however that notably shops its code in alternate information streams related to benign recordsdata on the sufferer’s system.
- PteroQuark: One other VBScript downloader found in October 2024, launched as a brand new part throughout the VBScript model of the PteroLNK weaponizer.
- PteroBox: A PowerShell file stealer found in November 2024, carefully resembling PteroPSDoor however exfiltrating stolen recordsdata to Dropbox. It leverages WMI occasion subscriptions to detect newly inserted USB drives and exfiltrates chosen recordsdata utilizing the Dropbox API. The stolen recordsdata are meticulously tracked to keep away from redundant uploads, highlighting Gamaredon’s growing consideration to stealth and effectivity.
Main updates to current instruments in 2024
Along with new instruments, Gamaredon operators considerably upgraded current instruments of their arsenal:
- PteroPSDoor: A serious improve launched superior stealth methods, akin to monitoring file modifications by way of the IO.FileSystemWatcher object fairly than constantly scanning directories, considerably lowering visibility. It additionally applied WMI occasion subscriptions to detect new USB insertions, making file exfiltration extra focused and stealthier. Moreover, the newest variations retailer code solely in registry keys as a substitute of in recordsdata, additional complicating detection.
- PteroLNK (VBScript model): This device was enhanced in early 2024 to weaponize not solely USB drives but additionally mapped community drives, increasing its lateral motion capabilities. All through the second half of 2024, it obtained a number of incremental updates, together with improved obfuscation, extra advanced strategies for LNK file creation, and registry-based methods to cover recordsdata and file extensions from victims. This weaponizer has change into one among Gamaredon’s most incessantly up to date and actively maintained instruments.
- PteroVDoor: This VBScript file stealer continued for use in two variants (obfuscated and unobfuscated). All through 2024, Gamaredon operators repeatedly up to date the device, introducing new exterior platforms akin to Codeberg repositories to dynamically distribute command and management (C&C) server data, complicating defensive measures.
- PteroPSLoad: Gamaredon notably transitioned again to utilizing Cloudflare tunnels as a substitute of ngrok for its C&C infrastructure. This marked the start of Gamaredon hiding nearly its complete C&C infrastructure behind Cloudflare-generated domains, considerably enhancing its operational safety.
Uncommon payloads: Russian propaganda by way of malware?
A very intriguing discovering was the invention in July 2024 of a singular advert hoc VBScript payload, delivered by Gamaredon downloaders. This payload had no espionage performance; fairly, its sole function was to robotically open a Telegram propaganda channel named Guardians of Odessa, which spreads pro-Russian messaging concentrating on the Odessa area. Whereas uncommon for Gamaredon’s typical operations, we attribute this payload to Gamaredon with excessive confidence.
Community infrastructure and evasion methods
All through 2024, Gamaredon confirmed persistent dedication to evading network-based defenses:
- The group continued, albeit at a diminished scale, to leverage fast-flux DNS methods, incessantly rotating IP addresses behind its domains. Nonetheless, the variety of domains that it registered declined notably from over 500 in 2023 to about 200 in 2024.
- Gamaredon more and more relied on third-party providers akin to Telegram, Telegraph, Codeberg, and Cloudflare tunnels to obfuscate and dynamically distribute its C&C infrastructure. Cloudflare-generated subdomains grew to become the group’s main communication endpoints, with conventional domains relegated principally to fallback use.
- A number of DoH providers (Google and Cloudflare) and third-party resolver web sites (akin to nslookup.io, who.is, dnswatch.information, and check-host.web) have been recurrently leveraged to bypass domain-based blocking.
- Gamaredon additionally launched new methods akin to dropping embedded HTA and VBScript recordsdata into short-term directories and executing them individually to resolve C&C domains, additional complicating automated detection efforts.
Regardless of observable capability limitations and abandoning older instruments, Gamaredon stays a major menace actor as a result of its steady innovation, aggressive spearphishing campaigns, and chronic efforts to evade detections. So long as the Russia’s battle towards Ukraine continues, we anticipate Gamaredon will persistently evolve its techniques and intensify its cyberespionage operations towards Ukrainian establishments.
For an in depth technical breakdown of Gamaredon’s 2024 actions, updates, and malware analyses, learn our full white paper.
A complete checklist of indicators of compromise (IoCs) might be present in our GitHub repository and the Gamaredon white paper.
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis provides personal APT intelligence reviews and information feeds. For any inquiries about this service, go to the ESET Risk Intelligence web page.



