In in the present day’s digital-first enterprise atmosphere, having the correct know-how isn’t simply a bonus—it’s important for survival. Portland companies face distinctive challenges that require tailor-made know-how options, not one-size-fits-all approaches. Whether or not you’re a producing plant on the economic eastside or a legislation agency downtown in Pioneer Sq., your IT technique should align together with your particular targets, trade calls for, and progress trajectory.
This complete information explores how producers {and professional} service companies throughout Portland can develop customized IT methods that handle their distinctive challenges, maximize operational effectivity, and safe their digital belongings in an more and more advanced know-how panorama.
Understanding Portland’s Enterprise Know-how Panorama
The Distinctive Know-how Wants of Portland Industries
Portland’s enterprise ecosystem is various—from superior manufacturing operations to specialised skilled service companies. Every sector faces distinct know-how challenges:
- Manufacturing corporations require programs that combine manufacturing workflows, stock administration, and provide chain visibility
- Regulation companies want safe doc and case administration, consumer portals, and compliance-ready programs
- Architectural companies rely on highly effective design software program, rendering capabilities, and collaborative platforms
- Engineering companies depend on specialised technical functions and data-intensive workflows
- Consulting organizations require versatile programs that assist distant collaboration and consumer engagement
Whereas nationwide know-how developments matter, Portland companies should navigate particular native components, together with the area’s expertise market, connectivity infrastructure, and aggressive panorama.
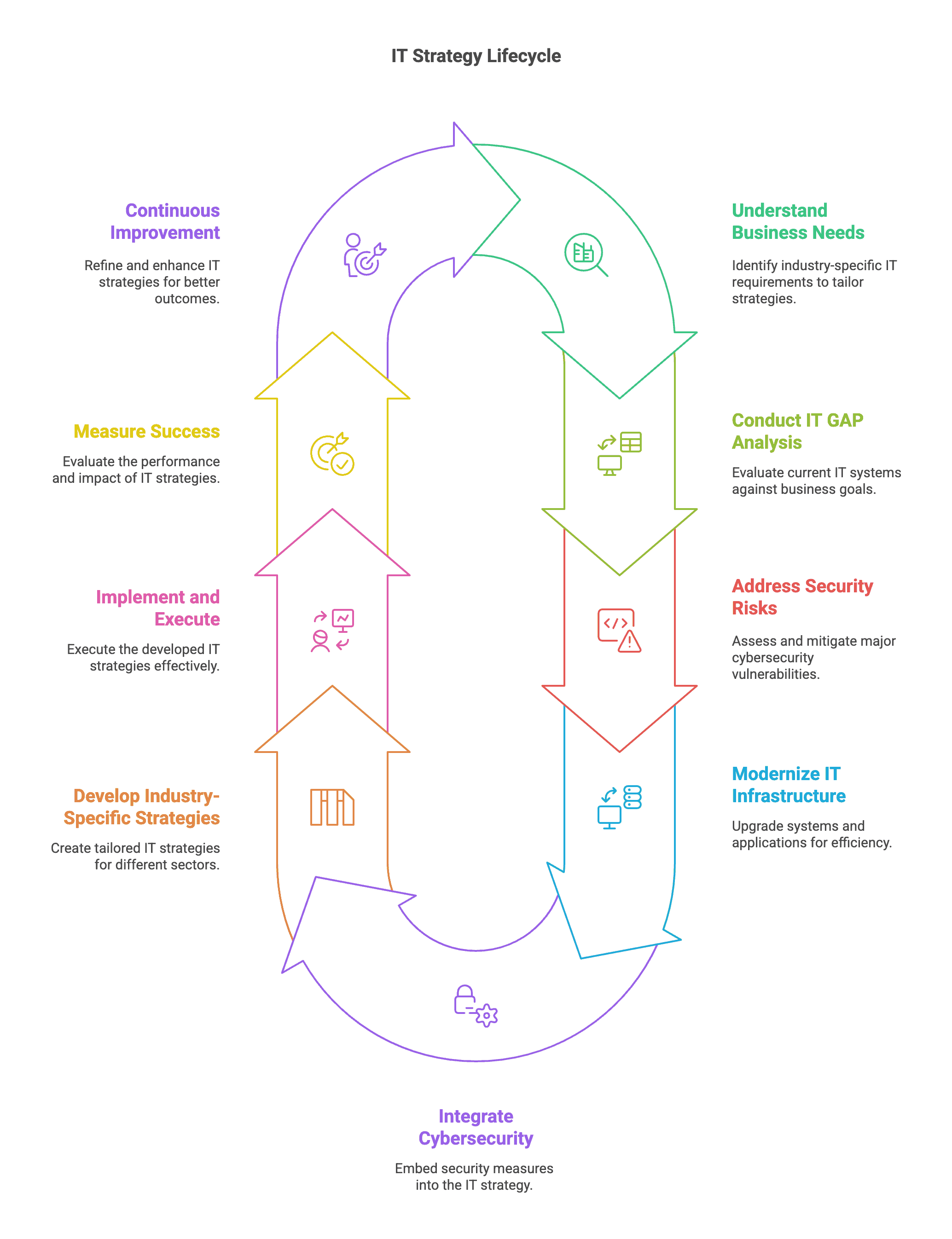
The Basis: IT GAP Evaluation for Portland Companies
What Is an IT GAP Evaluation?
An IT GAP Evaluation serves because the cornerstone of any efficient IT technique. This systematic evaluation compares your present know-how capabilities towards what you are promoting aims and trade necessities, figuring out:
- Underperforming programs that restrict productiveness
- Lacking capabilities required for future progress
- Redundant applied sciences that enhance prices with out including worth
- Safety vulnerabilities that put what you are promoting in danger
For Portland companies, an IT GAP Evaluation gives essential perception into how your present know-how stack measures towards each your strategic targets and native trade requirements.
Conducting an Efficient IT GAP Evaluation
A complete IT GAP Evaluation for Portland companies sometimes entails:
- Documentation of present programs: Stock all {hardware}, software program, networking gear, and cloud companies
- Enterprise targets alignment: Map how present know-how helps (or hinders) crucial enterprise aims
- Trade benchmarking: Examine your capabilities towards Portland rivals and trade requirements
- Person expertise analysis: Collect suggestions from workers about know-how ache factors and desires
- Future wants evaluation: Establish upcoming enterprise initiatives that can require know-how assist
This course of reveals the “gaps” between your present capabilities and what your Portland enterprise really must succeed—forming the inspiration for strategic know-how planning.
From Evaluation to Motion
When you’ve accomplished your IT GAP Evaluation, prioritize recognized points primarily based on:
- Enterprise influence (how considerably they have an effect on operations)
- Safety implications (potential danger publicity)
- Price concerns (each funding required and potential financial savings)
- Implementation complexity (time and sources wanted)
This prioritization ensures your customized IT technique addresses probably the most crucial wants first, maximizing the return in your know-how investments.
Modernization: Creating Your Customized IT Modernization Technique
Indicators Your Portland Enterprise Wants IT Modernization
Portland companies typically show clear warning indicators when their know-how infrastructure requires modernization:
- Methods continuously crash or function slowly
- Employees depend on handbook workarounds for routine duties
- Growing upkeep prices for legacy programs
- Incapability to assist distant or hybrid work fashions
- Issue integrating with buyer or vendor programs
- Falling behind rivals in know-how capabilities
If these signs sound acquainted, it’s time to develop a focused IT Modernization Technique.
Core Elements of an IT Modernization Technique
Infrastructure Modernization
Consider whether or not your present {hardware}, networking gear, and amenities meet enterprise wants. Contemplate:
- Cloud migration alternatives that cut back on-premise infrastructure
- Community upgrades to assist trendy functions and workflows
- Modernized information storage options that enhance accessibility and safety
Software Modernization
Evaluation your software program portfolio for modernization alternatives:
- Exchange legacy functions with trendy cloud-based alternate options
- Combine disparate programs to enhance information stream
- Implement APIs to attach crucial enterprise programs
- Automate handbook processes via workflow software program
Digital Expertise Modernization
Improve how workers and clients work together together with your know-how:
- Enhance person interfaces for inner programs
- Develop cell capabilities for field-based workers
- Create customer-facing digital instruments that streamline interactions
- Implement self-service portals for widespread requests
Phased Implementation Strategy
For Portland producers {and professional} service companies, a phased modernization strategy sometimes works finest:
- Section 1: Tackle crucial vulnerabilities and rapid enterprise wants
- Section 2: Implement core system enhancements that improve day by day operations
- Section 3: Deploy superior capabilities that present aggressive benefits
- Section 4: Set up steady enchancment processes for ongoing modernization
This sequential strategy manages danger whereas delivering incremental advantages all through the modernization journey.
Cybersecurity: Integrating Danger Assessments into Your IT Technique
The Portland Cybersecurity Panorama
Portland companies face an evolving set of cybersecurity challenges:
- Focused ransomware assaults towards native companies
- Growing compliance necessities throughout industries
- Provide chain vulnerabilities that have an effect on producers
- Consumer confidentiality issues for skilled service companies
- Superior persistent threats focusing on mental property
A customized IT technique for should embrace strong cybersecurity measures tailor-made to your particular danger profile and trade necessities.
The Cybersecurity Danger Evaluation Course of
A complete Cybersecurity Danger Evaluation sometimes contains:
- Asset stock: Documenting all programs, information repositories, and entry factors
- Risk evaluation: Figuring out potential threats particular to what you are promoting and trade
- Vulnerability evaluation: Evaluating weaknesses in your present safety posture
- Influence evaluation: Figuring out potential enterprise penalties of safety breaches
- Danger prioritization: Rating recognized dangers primarily based on chance and potential influence
- Mitigation planning: Growing particular methods to deal with precedence dangers
This evaluation ought to take into account native components like bodily safety at your amenities, regional cybersecurity sources, and Portland-specific regulatory necessities.
Constructing Safety Into Your IT Technique
Based mostly in your Cybersecurity Danger Evaluation, combine these safety components into your broader IT technique:
- Safety structure: Design programs with safety controls in-built from the beginning
- Entry administration: Implement role-based entry controls and multi-factor authentication
- Knowledge safety: Develop complete information classification and safety mechanisms
- Incident response: Create detailed plans for responding to safety incidents
- Safety consciousness: Practice workers on safety finest practices and menace recognition
- Steady monitoring: Implement programs to detect and alert on safety anomalies
By approaching safety as an integral part of your IT technique quite than an afterthought, Portland companies can defend precious belongings whereas enabling operational effectivity.
Trade-Particular IT Technique Insights
Customized IT Methods for Producers
Portland’s manufacturing sector—from steel fabrication to superior electronics—requires specialised know-how approaches:
- Manufacturing programs integration: Join store ground gear with administration programs
- Provide chain visibility: Implement real-time monitoring and forecasting capabilities
- High quality assurance know-how: Deploy programs to watch and enhance product high quality
- Predictive upkeep: Use IoT sensors and analytics to forestall gear failures
- Workforce enablement: Present digital instruments that improve employee productiveness and security
Customized IT Methods for Skilled Companies
For Portland’s legislation companies, architectural practices, engineering corporations, and consultancies, efficient IT methods sometimes emphasize:
- Consumer collaboration: Safe platforms for sharing deliverables and speaking
- Data administration: Methods to seize, set up, and leverage institutional experience
- Undertaking administration: Built-in instruments to trace timelines, sources, and deliverables
- Safe mobility: Options that allow safe work from wherever
- Enterprise intelligence: Analytics capabilities to measure efficiency and determine alternatives
Implementation: Bringing Your Customized IT Technique to Life
Creating Your Implementation Roadmap
Translating technique into motion requires an in depth implementation roadmap that features:
- Undertaking phases with clear timelines and milestones
- Useful resource allocation (each inner workers and exterior companions)
- Price range projections and monetary monitoring mechanisms
- Danger administration provisions for implementation challenges
- Change administration procedures to make sure adoption
For Portland companies, take into account how seasonal components, native expertise availability, and regional enterprise cycles would possibly have an effect on your implementation timeline.
Measuring Success: Key Efficiency Indicators
Set up clear metrics to judge your IT technique’s effectiveness, akin to:
- System uptime and reliability statistics
- Person adoption and satisfaction measures
- Course of effectivity enhancements
- Safety incident frequency and backbone occasions
- Direct value financial savings and income impacts
- Aggressive benefit indicators
Evaluation these metrics frequently, adjusting your technique as wanted to maximise enterprise influence.
Constructing the Proper Workforce
Executing your IT technique requires the correct mix of expertise and experience:
- Inner IT staff: Guarantee your workers has the mandatory expertise and capability
- Know-how companions: Establish distributors who perceive your trade and enterprise
- Managed service suppliers: Contemplate Portland-based MSPs for ongoing assist
- Cybersecurity specialists: Have interaction specialists for safety implementation and testing
- Change administration sources: Help person adoption via coaching and communication
In Portland’s aggressive know-how expertise market, take into account how your staffing strategy balances in-house capabilities with exterior experience.
Conclusion: The Path Ahead
Growing a Customized IT Technique isn’t nearly know-how—it’s about making a basis for sustainable enterprise success. By conducting an intensive IT GAP Evaluation, implementing a considerate IT Modernization Technique, and prioritizing Cybersecurity Danger Assessments, your group can rework know-how from a vital expense right into a strategic benefit.
Essentially the most profitable Portland companies acknowledge that know-how technique isn’t a one-time undertaking however an ongoing means of alignment, optimization, and innovation. As what you are promoting evolves and know-how continues to advance, your IT technique ought to adapt accordingly.
Now’s the time to judge your present know-how strategy and take into account how a very personalized IT technique may assist what you are promoting obtain its full potential.
In in the present day’s digital-first enterprise atmosphere, having the correct know-how isn’t simply a bonus—it’s important for survival. Portland companies face distinctive challenges that require tailor-made know-how options, not one-size-fits-all approaches. Whether or not you’re a producing plant on the economic eastside or a legislation agency downtown in Pioneer Sq., your IT technique should align together with your particular targets, trade calls for, and progress trajectory.
This complete information explores how producers {and professional} service companies throughout Portland can develop customized IT methods that handle their distinctive challenges, maximize operational effectivity, and safe their digital belongings in an more and more advanced know-how panorama.
Understanding Portland’s Enterprise Know-how Panorama
The Distinctive Know-how Wants of Portland Industries
Portland’s enterprise ecosystem is various—from superior manufacturing operations to specialised skilled service companies. Every sector faces distinct know-how challenges:
- Manufacturing corporations require programs that combine manufacturing workflows, stock administration, and provide chain visibility
- Regulation companies want safe doc and case administration, consumer portals, and compliance-ready programs
- Architectural companies rely on highly effective design software program, rendering capabilities, and collaborative platforms
- Engineering companies depend on specialised technical functions and data-intensive workflows
- Consulting organizations require versatile programs that assist distant collaboration and consumer engagement
Whereas nationwide know-how developments matter, Portland companies should navigate particular native components, together with the area’s expertise market, connectivity infrastructure, and aggressive panorama.
The Basis: IT GAP Evaluation for Portland Companies
What Is an IT GAP Evaluation?
An IT GAP Evaluation serves because the cornerstone of any efficient IT technique. This systematic evaluation compares your present know-how capabilities towards what you are promoting aims and trade necessities, figuring out:
- Underperforming programs that restrict productiveness
- Lacking capabilities required for future progress
- Redundant applied sciences that enhance prices with out including worth
- Safety vulnerabilities that put what you are promoting in danger
For Portland companies, an IT GAP Evaluation gives essential perception into how your present know-how stack measures towards each your strategic targets and native trade requirements.
Conducting an Efficient IT GAP Evaluation
A complete IT GAP Evaluation for Portland companies sometimes entails:
- Documentation of present programs: Stock all {hardware}, software program, networking gear, and cloud companies
- Enterprise targets alignment: Map how present know-how helps (or hinders) crucial enterprise aims
- Trade benchmarking: Examine your capabilities towards Portland rivals and trade requirements
- Person expertise analysis: Collect suggestions from workers about know-how ache factors and desires
- Future wants evaluation: Establish upcoming enterprise initiatives that can require know-how assist
This course of reveals the “gaps” between your present capabilities and what your Portland enterprise really must succeed—forming the inspiration for strategic know-how planning.
From Evaluation to Motion
When you’ve accomplished your IT GAP Evaluation, prioritize recognized points primarily based on:
- Enterprise influence (how considerably they have an effect on operations)
- Safety implications (potential danger publicity)
- Price concerns (each funding required and potential financial savings)
- Implementation complexity (time and sources wanted)
This prioritization ensures your customized IT technique addresses probably the most crucial wants first, maximizing the return in your know-how investments.
Modernization: Creating Your Customized IT Modernization Technique
Indicators Your Portland Enterprise Wants IT Modernization
Portland companies typically show clear warning indicators when their know-how infrastructure requires modernization:
- Methods continuously crash or function slowly
- Employees depend on handbook workarounds for routine duties
- Growing upkeep prices for legacy programs
- Incapability to assist distant or hybrid work fashions
- Issue integrating with buyer or vendor programs
- Falling behind rivals in know-how capabilities
If these signs sound acquainted, it’s time to develop a focused IT Modernization Technique.
Core Elements of an IT Modernization Technique
Infrastructure Modernization
Consider whether or not your present {hardware}, networking gear, and amenities meet enterprise wants. Contemplate:
- Cloud migration alternatives that cut back on-premise infrastructure
- Community upgrades to assist trendy functions and workflows
- Modernized information storage options that enhance accessibility and safety
Software Modernization
Evaluation your software program portfolio for modernization alternatives:
- Exchange legacy functions with trendy cloud-based alternate options
- Combine disparate programs to enhance information stream
- Implement APIs to attach crucial enterprise programs
- Automate handbook processes via workflow software program
Digital Expertise Modernization
Improve how workers and clients work together together with your know-how:
- Enhance person interfaces for inner programs
- Develop cell capabilities for field-based workers
- Create customer-facing digital instruments that streamline interactions
- Implement self-service portals for widespread requests
Phased Implementation Strategy
For Portland producers {and professional} service companies, a phased modernization strategy sometimes works finest:
- Section 1: Tackle crucial vulnerabilities and rapid enterprise wants
- Section 2: Implement core system enhancements that improve day by day operations
- Section 3: Deploy superior capabilities that present aggressive benefits
- Section 4: Set up steady enchancment processes for ongoing modernization
This sequential strategy manages danger whereas delivering incremental advantages all through the modernization journey.
Cybersecurity: Integrating Danger Assessments into Your IT Technique
The Portland Cybersecurity Panorama
Portland companies face an evolving set of cybersecurity challenges:
- Focused ransomware assaults towards native companies
- Growing compliance necessities throughout industries
- Provide chain vulnerabilities that have an effect on producers
- Consumer confidentiality issues for skilled service companies
- Superior persistent threats focusing on mental property
A customized IT technique for should embrace strong cybersecurity measures tailor-made to your particular danger profile and trade necessities.
The Cybersecurity Danger Evaluation Course of
A complete Cybersecurity Danger Evaluation sometimes contains:
- Asset stock: Documenting all programs, information repositories, and entry factors
- Risk evaluation: Figuring out potential threats particular to what you are promoting and trade
- Vulnerability evaluation: Evaluating weaknesses in your present safety posture
- Influence evaluation: Figuring out potential enterprise penalties of safety breaches
- Danger prioritization: Rating recognized dangers primarily based on chance and potential influence
- Mitigation planning: Growing particular methods to deal with precedence dangers
This evaluation ought to take into account native components like bodily safety at your amenities, regional cybersecurity sources, and Portland-specific regulatory necessities.
Constructing Safety Into Your IT Technique
Based mostly in your Cybersecurity Danger Evaluation, combine these safety components into your broader IT technique:
- Safety structure: Design programs with safety controls in-built from the beginning
- Entry administration: Implement role-based entry controls and multi-factor authentication
- Knowledge safety: Develop complete information classification and safety mechanisms
- Incident response: Create detailed plans for responding to safety incidents
- Safety consciousness: Practice workers on safety finest practices and menace recognition
- Steady monitoring: Implement programs to detect and alert on safety anomalies
By approaching safety as an integral part of your IT technique quite than an afterthought, Portland companies can defend precious belongings whereas enabling operational effectivity.
Trade-Particular IT Technique Insights
Customized IT Methods for Producers
Portland’s manufacturing sector—from steel fabrication to superior electronics—requires specialised know-how approaches:
- Manufacturing programs integration: Join store ground gear with administration programs
- Provide chain visibility: Implement real-time monitoring and forecasting capabilities
- High quality assurance know-how: Deploy programs to watch and enhance product high quality
- Predictive upkeep: Use IoT sensors and analytics to forestall gear failures
- Workforce enablement: Present digital instruments that improve employee productiveness and security
Customized IT Methods for Skilled Companies
For Portland’s legislation companies, architectural practices, engineering corporations, and consultancies, efficient IT methods sometimes emphasize:
- Consumer collaboration: Safe platforms for sharing deliverables and speaking
- Data administration: Methods to seize, set up, and leverage institutional experience
- Undertaking administration: Built-in instruments to trace timelines, sources, and deliverables
- Safe mobility: Options that allow safe work from wherever
- Enterprise intelligence: Analytics capabilities to measure efficiency and determine alternatives
Implementation: Bringing Your Customized IT Technique to Life
Creating Your Implementation Roadmap
Translating technique into motion requires an in depth implementation roadmap that features:
- Undertaking phases with clear timelines and milestones
- Useful resource allocation (each inner workers and exterior companions)
- Price range projections and monetary monitoring mechanisms
- Danger administration provisions for implementation challenges
- Change administration procedures to make sure adoption
For Portland companies, take into account how seasonal components, native expertise availability, and regional enterprise cycles would possibly have an effect on your implementation timeline.
Measuring Success: Key Efficiency Indicators
Set up clear metrics to judge your IT technique’s effectiveness, akin to:
- System uptime and reliability statistics
- Person adoption and satisfaction measures
- Course of effectivity enhancements
- Safety incident frequency and backbone occasions
- Direct value financial savings and income impacts
- Aggressive benefit indicators
Evaluation these metrics frequently, adjusting your technique as wanted to maximise enterprise influence.
Constructing the Proper Workforce
Executing your IT technique requires the correct mix of expertise and experience:
- Inner IT staff: Guarantee your workers has the mandatory expertise and capability
- Know-how companions: Establish distributors who perceive your trade and enterprise
- Managed service suppliers: Contemplate Portland-based MSPs for ongoing assist
- Cybersecurity specialists: Have interaction specialists for safety implementation and testing
- Change administration sources: Help person adoption via coaching and communication
In Portland’s aggressive know-how expertise market, take into account how your staffing strategy balances in-house capabilities with exterior experience.
Conclusion: The Path Ahead
Growing a Customized IT Technique isn’t nearly know-how—it’s about making a basis for sustainable enterprise success. By conducting an intensive IT GAP Evaluation, implementing a considerate IT Modernization Technique, and prioritizing Cybersecurity Danger Assessments, your group can rework know-how from a vital expense right into a strategic benefit.
Essentially the most profitable Portland companies acknowledge that know-how technique isn’t a one-time undertaking however an ongoing means of alignment, optimization, and innovation. As what you are promoting evolves and know-how continues to advance, your IT technique ought to adapt accordingly.
Now’s the time to judge your present know-how strategy and take into account how a very personalized IT technique may assist what you are promoting obtain its full potential.







