With the widespread use of Web and cloud computing, social networking, e-commerce functions, a considerable amount of knowledge will get generated day by day. Information safety is a really essential facet of community safety as an increasing number of individuals are utilizing the Web and society is transferring in the direction of the digital info age, cyber criminals are extra lively and utilizing superior strategies to realize entry to group’s life traces, their knowledge. Community safety and cryptography is used to guard community and knowledge transmission over wi-fi networks.
In at this time’s subject we are going to look extra intimately in regards to the community safety mannequin which reveals how safety service is designed, its parts, the way it works and its options.
Community Safety Mannequin
Community safety mannequin describes how a safety service is designed to forestall cyber attackers from inflicting menace to confidentiality and authenticity of knowledge transmitted or exchanged over the community. Trade of messages occur between a sender and receiver and earlier than transmission they should mutually agree on sharing the message with this is available in image is the communication channel or info channel which is an Web service.
When message is transmitted over the community between sender and receiver, it entails three parts from safety service perspective specifically:
- Transformation – of knowledge which must be despatched or acquired to be encrypted so {that a} cyber attacker is unable to intercept it. It might contain addition of code in the course of the transmission of knowledge which can be used to confirm the identification of the receiver.
- Secret info / key sharing between sender and receiver is used to encrypt messages at sender finish and decrypt at receiver finish.
- Trusted third get together is the one which ought to take the accountability of distributing secret info / key to each sender and receiver concerned in communication with out the involvement of intruder or cyber attacker.
Community Safety Mannequin Structure
The community safety mannequin above depicts two events in communication the place sender and receiver mutually conform to trade info. Sender needs to ship some messages to the receiver however can’t transmit them in clear textual content format as it might have threat of interception by intruder. So earlier than sending a message to the receiver through an info channel, it needs to be transmitted in an unreadable format.
- Secret info / key’s used to transmit a message to receiver together with key to make message readable to the receiver and thus a 3rd get together comes into the image who could be accountable for distributing the key info / key to each the events concerned in communication.
- An encryption key used together with transformation to scramble message earlier than transmission after which unscramble it on receiving it.
- Encryption supplies knowledge safety whereas key administration is required to allow entry to knowledge which require safety from unauthorized events.
Cryptography
Cryptography is used to retailer / transmit knowledge in a particular format in order that solely these from whom it’s supposed are in a position to course of it. The cleartext is scrambled into ciphertext (often called encryption) after which again once more, often called decryption. There are typically three sorts of cryptographic schemes generally used: secret key (or symmetric) cryptography, public-key (or uneven) cryptography, and hash features.
Sorts of Cryptography
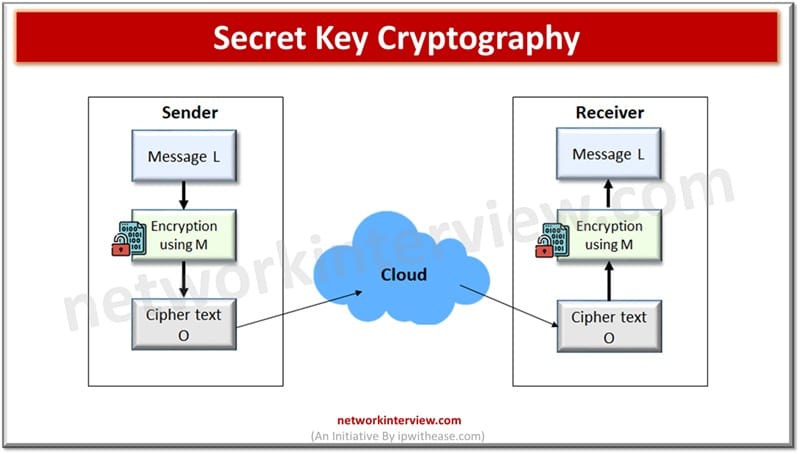
Secret Key (or symmetric) Cryptography
A single key’s used for encryption and decryption each as depicted in determine under.
Sender A makes use of Key M to encrypt plaintext message L and sends the ciphertext O to the receiver. The receiver applies the Key M to decrypt the ciphertext O and get well plaintext L. Key should be identified to each sender and receiver right here.
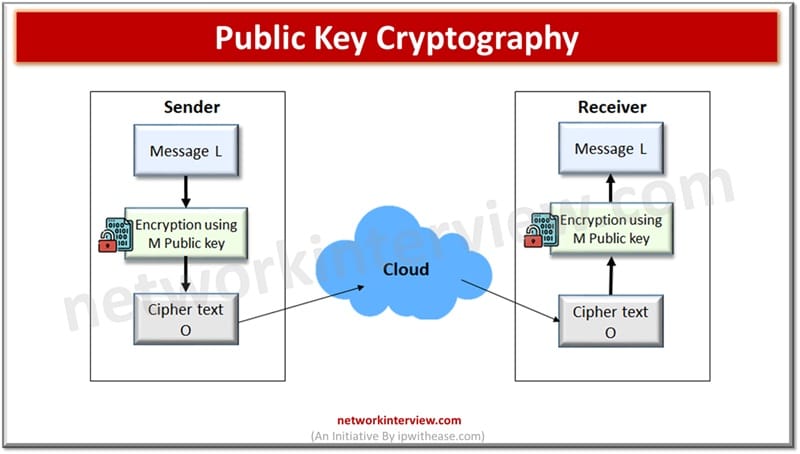
Public-key (or uneven) Cryptography
Encryption is carried out utilizing totally different keys – private and non-private key. Sender makes use of the general public key of the receiver to encrypt plaintext message L and sends ciphertext O to the receiver. The receiver replies with its personal personal key to decrypt the ciphertext O and get well plaintext message L.
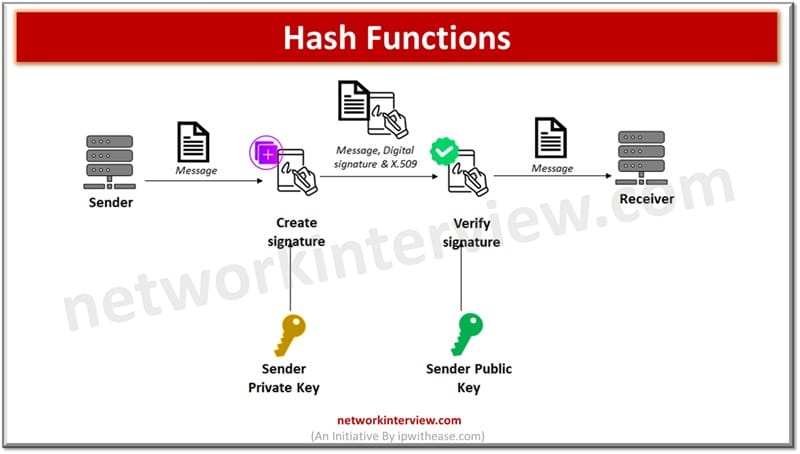
Hash features
A digital signature is an authentication mechanism to allow the creator of a message to connect a code which acts as signature. Signature is fashioned by taking the hash of the message and encrypting the message with the creator’s personal key. Signature is used to ensure message supply and its integrity.





