The Chief Info Safety Workplace (CISO) or vCISO workshop helps speed up safety program modernization with reference methods constructed utilizing Zero Belief ideas. The workshop covers all facets of a complete safety program together with strategic initiatives, roles and obligations, success metrics, maturity fashions, and extra.
vCISO Academy
The vCISO Academy is a free, skilled studying platform designed to empower MSPs, MSSPs, safety consultants, and CISOs to construct and develop their vCISO expertise and providers.
CISO Workshop
Notice: Ciso Workshop Movies : https://study.microsoft.com/en-us/safety/ciso-workshop/the-ciso-workshop
The workshop movies (about 4 hours whole) and slides are organized into these discussions:
- Introduction and Overview of the CISO Workshop
- Half A – Key Context and Fundamentals
- Half B – Enterprise Alignment
- Partaking enterprise leaders on safety – steerage to have a dialog within the language of leaders to clarify safety, key metrics to measure success of a program, and find out how to get assist for safety targets.
- Threat Insights – discusses the twin mission of safety to cut back danger to the group and allow enterprise targets, shares tips about aligning safety enterprise targets and enterprise danger, and shares insights on the sorts of attacker motivations group’s face.
- Safety Integration – steerage for efficiently integrating safety groups collectively and integrating safety into IT and Enterprise processes. Together with an in-depth dialogue of find out how to construct a posture administration program – an operational workforce centered on preventive controls (which enhances the safety operations (SecOps/SOC) workforce centered on detection, response, and restoration)
- Enterprise Resilience – discusses how enterprise resilience is the north star of the safety program throughout all the safety disciplines that requires balancing safety investments (earlier than, throughout, and after an incident) and creating a powerful suggestions loop. This part additionally contains dialogue of the influence of unbalanced methods (which is a standard antipattern).
- Maturity fashions describing actual world journeys for Threat Insights, Safety Integration, and Enterprise Resilience – together with particular concrete actions that will help you transfer as much as the subsequent degree
- Half C – Safety Disciplines
- Entry Management – discusses how the Zero Belief strategy is reworking entry management, together with id and community entry converging right into a single coherent strategy, and the emergence of the Identified-Trusted-Allowed mannequin (which updates the traditional authenticated/licensed strategy).
- Safety Operations – discusses key management facets of a safety operations functionality, usually known as SecOps or a Safety Operations Heart (SOC) together with essential success metrics, key touchpoints with enterprise leaders and features, and crucial cultural parts.
- Asset Safety – discusses two key imperatives for groups that handle and safe belongings (usually IT Operations or Workload operations in DevOps). These groups should prioritize safety work based mostly on enterprise criticality and should attempt to effectively scale safety throughout the big, rising, and repeatedly evolving set of belongings within the technical property.
- Safety Governance – discusses the function of Safety Governance as a bridge between the world of enterprise targets and expertise and the way this function is altering with the arrival of cloud, digital and nil belief transformations. This part additionally covers key parts of safety governance together with danger, compliance, safety structure, posture administration, (strategic) menace intelligence, and extra.
- Innovation Safety – dialogue of how software safety evolves into a contemporary strategy (together with DevSecOps) and key focus areas to drive success of this functionality.
- Safety Governance Maturity fashions describing actual world journeys for Safety Structure, Posture Administration, and IT Safety Upkeep – together with particular concrete actions that will help you transfer as much as the subsequent degree
- Subsequent Steps/Closing – wraps up the workshop with key fast wins and subsequent steps
Crucial: Protection for commom assault chains (Insider and exterior threats)
Microsoft Digital Protection Report:
https://aka.ms/MDDR = https://www.microsoft.com/en-us/safety/enterprise/microsoft-digital-defense-report-2022
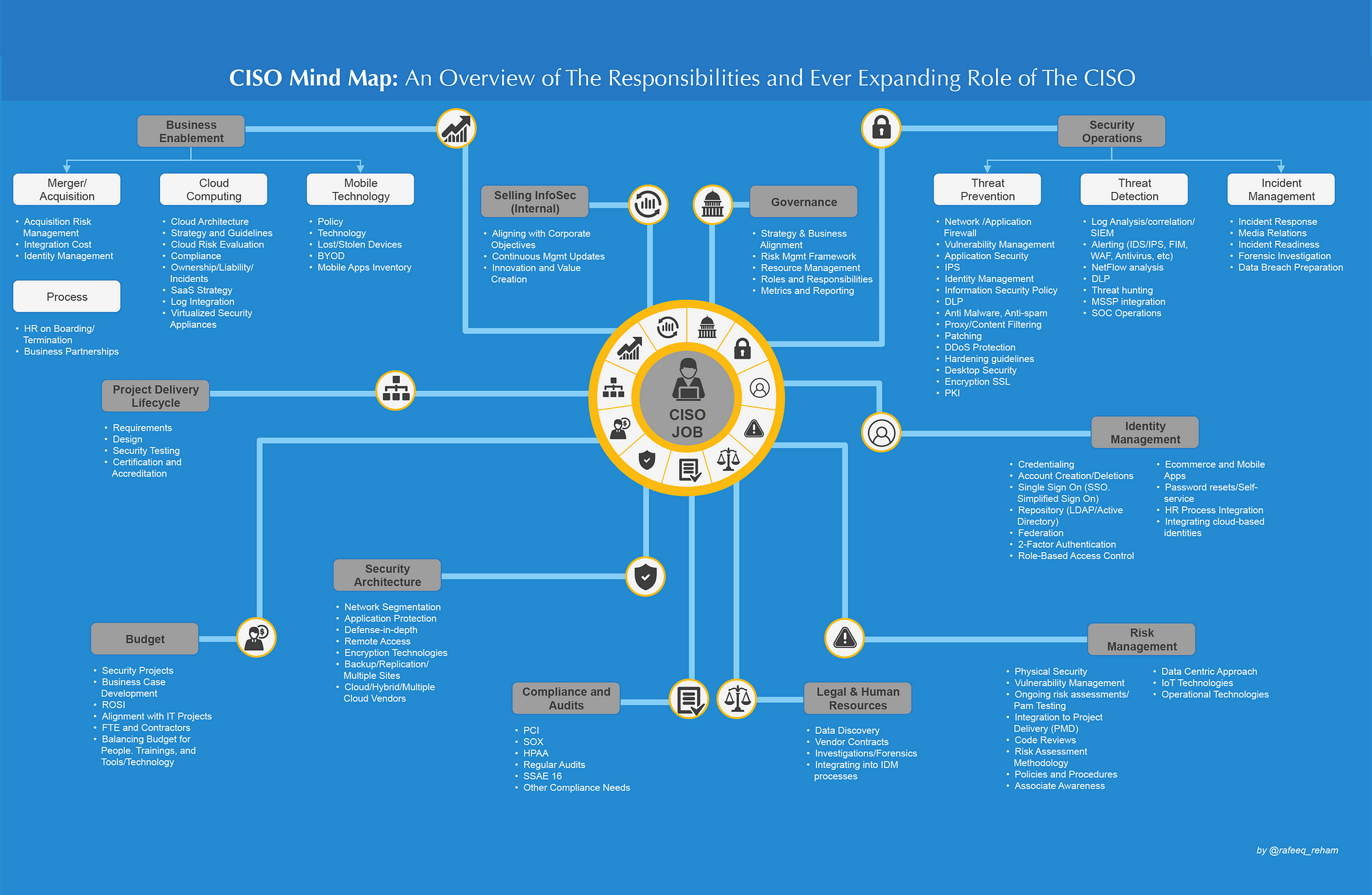
A CISO (Chief Info Safety Officer) has a posh function inside an organization. They’ve a big selection of duties to carry out, that entails many differing components, which the typical particular person shouldn’t be at all times conscious of.
CISO Thoughts Map is an summary of obligations and ever increasing function of the CISO. This Safety Management poster made by SANS reveals precisely the issues a CISO must thoughts when making a world class IT Safety workforce. It additionally highlights the important options mandatory of a Safety Operations Centre (SOC).
To make this chart extra sensible, I put them into the tables and can replace it with some applied sciences and ideas utilized in my every day work. This replace will final a long run. Will probably be put into navigation bar for simple entry.
Safety Operations
|
Prevention |
Detection |
Response |
|
|
|
Authorized and Regulatory
Threat Administration
| Threat Framework | Threat Evaluation Methodology | Enterprise Affect Evaluation |
|
||
| Threat Evaluation Course of | Threat Evaluation and Quantification | Safety Consciousness |
|
||
| Vulnerability Administration | Vendor Threat Administration | Bodily Safety |
|
||
| Catastrophe Restoration (DR) | Enterprise Continuity Planning | Threat Therapy |
|
||
| Insurance policies and Procedures | ||
|
||
Enterprise Enablement
| Product Safety | Cloud Computing | Cell |
|
|
|
| Rising Applied sciences | Mergers and Acquisitions | |
|
Governance
| Technique | Enterprise Alignment | Threat Administration |
|
||
| Program Frameworks | Management Frameworks | Program Construction |
| Program Administration | Communications Plan | Roles and Tasks |
| Workforce Planning | Useful resource Managemnet | Information Classification |
| Safety Coverage | Create a Safety Tradition | Safety Coaching |
|
||
| Metrics and Reporting | IT Portfolio Administration | Change Administration |
| Board Communications | ||
|
Establish and Entry Administration
|
Provisioning/ Deprovisioning |
Single Signal On (SSO) |
Federated Single Sing on (FSSO) |
|
Multi-Issue Authentication |
Position-Based mostly Entry Management (RBAC) |
Id Retailer (LDAP, ActiveDirectory) |
Management Expertise
| Enterprise Technique | Trade Data | Enterprise Acumen |
| Communication Expertise | Presentation Expertise | Strategic Planning |
| Technical Management | Safety Consulting | Stakeholder Administration |
|
||
| Negotiations | Mission and Imaginative and prescient | Values and Tradition |
| Roadmap Improvement | Enterprise Case Improvement | Undertaking Administration |
|
||
| Worker Improvement | Monetary Planning | Budgeting |
| Innovation | Advertising | Main Change |
| Buyer Relationships | Group Constructing | Mentoring |
|
Notice: ISO = Info Safety Workplace
One other CISO Thoughts Map instance:
Notice: The unique picture idea was created by Rafeeq Rehman and later redesigned by Momentum Companions.
CISO Job and Precedence
CISO’s Information to Price-Efficient Priorities
Building a 2025 Security Stack: A Veteran CISO’s Guide to Cost-Effective Priorities
Compliance:
Documentation:
Human sources administration:
- Carry out background verification checks of job candidates
- Put together the coaching and consciousness plan for data safety (see additionally The right way to carry out coaching & consciousness for ISO 27001 and ISO 22301)
- Carry out steady actions associated to consciousness elevating
- Performing induction coaching on safety subjects for brand new staff
- Suggest disciplinary actions in opposition to staff who carried out the safety breach
Relationship with high administration:
- Talk the advantages of data safety (see additionally 4 key advantages of ISO 27001 implementation)
- Suggest data safety goals (see additionally ISO 27001 management goals – Why are they essential?)
- Report on the outcomes of measuring
- Suggest safety enhancements and corrective actions
- Suggest finances and different required sources for safeguarding the knowledge
- Report essential necessities of events
- Notify high administration about the principle dangers
- Report concerning the implementation of safeguards
- Advise high executives on all safety issues
Enhancements:
- Make sure that all corrective actions are carried out
- Confirm if the corrective actions have eradicated the reason for nonconformities
Asset administration:
- Preserve a list of all essential data belongings
- Delete the data that aren’t wanted any extra
- Eliminate media and gear now not in use, in a safe method
Third events:
- Carry out danger evaluation for actions to be outsourced
- Carry out background examine for candidates for outsourcing companions
- Outline safety clauses that should be a part of an settlement
Communication:
- Outline which kind of communication channels are acceptable and which aren’t
- Put together communication gear for use in case of an emergency / catastrophe
Incident administration:
- Obtain details about safety incidents
- Coordinate response to safety incidents
- Put together proof for authorized motion following an incident
- Analyze incidents with the intention to stop their recurrence
Enterprise continuity:
- Coordinate the enterprise influence evaluation course of and the creation of response plans
- Coordinate exercising and testing
- Carry out post-incident evaluation of the restoration plans
Technical:
- Approve acceptable strategies for the safety of cell gadgets, pc networks and different communication channels
- Suggest authentication strategies, password coverage, encryption strategies, and so on.
- Suggest guidelines for safe teleworking
- Outline required security measures of Web providers
- Outline ideas for safe growth of data techniques
- Overview logs of person actions with the intention to acknowledge suspicious conduct
The right way to begin your first 100 days as CISO
The obligations of a CISO or vCISO embrace the event
and administration of a cybersecurity technique, danger and
vulnerability administration, incident response planning,
safety coaching, compliance possession, finances and
vendor administration, and extra
Objectives:
- Set up, Oversee and Handle Organizational Safety
- Foster Belief with Safety Objectives
- Make Safety a Enterprise Enabler
Pitfalls to Keep away from
- Placing out fires
- Getting caught up in organizational politics
- Utilizing guide processes as an alternative of automation
- Forgetting about compliance
- Doing all the pieces your self
- Forgetting to set expectations with the shopper
- Being too dogmatic
- Avoiding difficult paradigms and selections
- Juggling too many industries
- Forgetting to combine knowledge from different components of the enterprise
The 5 Phases: Your 100 Day Motion Plan
- Analysis (Days 0-30): Assembly stakeholders and administration, assembly the IT/safety workforce, reviewing previous safety incidents and responses
- Meet stakeholders and administration to know their expectations and find out about the group.
- Meet the IT/safety workforce to construct relationships, consider the workforce’s expertise, perceive present workflows, and determine any gaps in experience or sources.
- Get entry to instruments, knowledge and all related techniques so you possibly can evaluation configurations, administration practices, and safety controls.
- Analyze current infrastructure, instruments, frameworks, insurance policies and studies to achieve insights into potential vulnerabilities and the effectiveness of current safety controls and procedures.
- Get hold of and perceive community and knowledge circulate diagrams to acknowledge essential knowledge flows and potential factors of publicity.
- Overview previous safety incidents and responses to guage the group’s means to reply and get well from such incidents.
- Conduct menace intelligence analysis of the menace panorama, together with CVEs, zero-days, laws and key gamers. Be aware of which menace actors are concentrating on some of these purchasers, how they get entry, and most well-liked strategies of persistence.
- Perceive the present vendor administration course of to disclose third-party dangers and compliance with safety insurance policies.
- Overview buyer contracts to make sure that customer-imposed safety necessities are met, as these can affect the prioritization of safety duties.
- Perceive the Software program Improvement Life Cycle (SDLC) program to see how safety is built-in into software growth (when relevant).
- Perceive (Days 0-45): Conducting a safety danger evaluation, exhibiting the present safety posture and gaps to the administration, figuring out short-term and long-term wants
- Conduct a safety danger evaluation. Taking all the information you’ve gathered, you’ll need to start to collate and synthesize it in a proper danger evaluation to baseline the atmosphere.
- Use a regular onboarding questionnaire and scanning device to offer goal evaluation of present dangers.
- Create a transparent image of safety maturity and the safety posture. Compile the info out of your preliminary assessments into clear, executive-friendly studies that embrace technical metrics and an analysis of the processes, folks, and expertise in place. Use established cybersecurity frameworks like NIST to measure the group’s safety practices in opposition to trade benchmarks.
- Present the present safety posture and gaps to the administration. Current a spot evaluation to administration that clearly delineates the place the group stands versus the place it must be. This must be carried out within the context of the group’s danger urge for food, regulatory necessities and enterprise targets.
- Establish short-term and long-term wants. Based mostly on the hole evaluation, develop a prioritized record of dangers and related remediation steps that align with enterprise goals, distinguishing between fast (short-term) and strategic (long-term) wants.
- Establish enterprise wants. Carry out an evaluation of how safety investments translate into enterprise worth, contemplating elements like diminished downtime, compliance fines prevented, and reputational advantages.
- Study using automation. Establish areas the place safety processes could be automated for effectivity, like danger and compliance assessments, hole evaluation, tailor-made insurance policies, creation of strategic remediation plans with prioritized duties, use of instruments for ongoing activity administration, progress monitoring and customer-facing studies
- Prioritize (Days 15-60): Defining brief, mid and long-term targets, making a remediation/work plan based mostly on these targets, planning budgets and sources
- Outline brief, mid and long-term targets. Draft particular, measurable, achievable, related, and time-bound (SMART) targets for the present 100 days, the top of the yr, and the next yr. These targets ought to concentrate on mitigating
- essentially the most vital dangers first.
- Create a remediation/work plan based mostly on these targets that lays out the steps mandatory to attain every purpose. This could embrace timelines, accountable events and anticipated outcomes.
- Establish 2-3 fast wins that may enhance safety posture with minimal effort or funding. For instance, enabling MFA or optimizing current safety device configurations for higher protection.
- Plan budgets and sources for safety initiatives, guaranteeing cost-effectiveness and alignment with broader monetary planning. Assess the place automation can scale back the necessity for added sources and streamline current operations, to avoid wasting prices and enhance effectivity.
- Create a danger register that paperwork all recognized dangers together with their probability and influence and prioritizes them.
- Share the targets and excessive degree plan with the administration, guaranteeing transparency and setting the stage for ongoing assist and engagement from the highest down.
- Execute (Days 30-80): Speaking the plan to all stakeholders, implementing automated techniques that may ship low hanging fruit, setting a cadence for exterior scanning and reporting
- Get stakeholder and administration buy-in by explaining the strategic plan, its advantages, and its influence on the group. Make sure that the worth of your proposed safety measures is clearly understood.
- Talk the plan to all stakeholders – vertical and horizontal. Make sure that all departments really feel included and answerable for its success.
- Implement automated techniques that may ship low hanging fruit. Listed below are some examples, however the precise automated system will rely on the vertical and firm sort.
- Automated password reset platforms
- Automated report technology
- Accounting techniques that require twin approval for cash transfers
- A vCISO platform
- Orchestration platforms that may automate cog deployments to forestall misconfigurations
- RPA (Robotic Course of Automation) suppliers for imposing JIT (Simply in Time) admin entry
- Automated code scanning or static testing instruments
- Give attention to the short, impactful wins that you simply recognized, like coverage updates or turning on unused however accessible security measures. This helps construct momentum and demonstrates early successes.
- Begin with excessive precedence coverage creation, similar to these governing incident response, knowledge safety, and entry management.
- Suggest buying merchandise or instruments if wanted.
- Set a cadence for exterior scanning and reporting, demonstrating enchancment and danger discount over time.
- Constantly handle and alter remediation plans to make sure they continue to be efficient and responsive.
- Report (Days 45-100): Measuring success, speaking progress at the least as soon as a month, integrating reporting into your general plan
- Measure Success by gathering and analyzing knowledge that displays the success of the executed plan. This might embrace metrics similar to:
- Diminished incident response instances
- Fewer profitable phishing makes an attempt
- Enchancment in safety and compliance postures
- Diminished danger ranges for malicious actions like knowledge leaks, ransomware, fraud and web site defacement
- Greater scores for domains like entry administration, menace intelligence, passwords, web site and knowledge safety
- Development in activity progress
- Craft detailed studies for administration that articulate successes, challenges, and areas requiring consideration. Stories ought to translate technical operations into enterprise impacts, making it simple for executives to know the return on their safety investments.
- Talk progress at the least as soon as a month, guaranteeing transparency and sustaining the urgency of cybersecurity initiatives. Professional tip: Use the identical commonplace studies to make reporting simpler to create and to devour.
- Combine reporting into your general plan, reflecting on how the safety measures contribute to the general enterprise technique and danger administration framework.
- Conduct a further full evaluation after 3-4 months to exhibit progress and determine any new or unresolved vulnerabilities.
- Reassess and Reajust:
- Use the findings from steady assessments to realign the safety technique with the
- group’s evolving wants and menace panorama.
- Prioritize new initiatives or reduce on these which are much less efficient.
- Work intently with the manager workforce to interpret report findings and plan for the approaching
- quarters.
- Constantly adapt and enhance your processes and controls to maintain safety measures
- efficient and related.
Pattern Inquiries to Ask Stakeholders
Pattern Inquiries to Ask Stakeholders:
- Are you able to record the mission-critical purposes your division makes use of every day?
- What knowledge sorts are mostly processed inside these purposes?
- Might you stroll me by way of the enterprise workflow utilizing these techniques?
- What sorts of fee strategies are processed, and thru what techniques?
- What are your main considerations about your present techniques and knowledge safety?
- What ongoing initiatives are being performed?
- What are your particular expectations from the vCISO service and this engagement?
CISA Tabletop Train Packages
CISA Tabletop Train Packages (CTEPs) are a complete set of sources designed to help stakeholders in conducting their very own workouts. Companions can use CTEPs to provoke discussions inside their organizations about their means to handle a wide range of menace eventualities.
Every bundle is customizable and contains template train goals, eventualities, and dialogue questions in addition to a group of references and sources. Obtainable eventualities cowl a broad array of bodily safety and cybersecurity subjects, similar to pure disasters, pandemics, civil disturbances, industrial management techniques, election safety, ransomware, automobile ramming, insider threats, energetic assailants, and unmanned aerial techniques. CTEPs additionally present state of affairs and module questions to debate pre-incident data and intelligence sharing, incident response, and post-incident restoration.
With over 100 CTEPs accessible, stakeholders can simply discover sources to satisfy their particular train wants.
Cybersecurity Situations
These CTEPs embrace cybersecurity-based eventualities that incorporate varied cyber menace vectors together with ransomware, insider threats, phishing, and Industrial Management System (ICS) compromise. There are additionally sector-specific cybersecurity eventualities for elections infrastructure, native governments, maritime ports, water, and healthcare.
Bodily Safety Situations
Lively shooters, automobile ramming, improvised explosive gadgets (IEDs), unmanned plane techniques (UASs), and lots of extra. There are additionally CTEPs which are geared in direction of particular industries or services to permit for dialogue of their distinctive wants.
Cyber-Bodily Convergence Situations
Bodily impacts ensuing from a cyber menace vector, or cyber impacts ensuing from a bodily menace vector. Whereas CTEPs inside the cyber and bodily sections could contact on these topics, convergence CTEPs are designed to additional discover the impacts of convergence and find out how to improve one’s resiliency.
CTEP Paperwork
Leverage pre-built templates to develop a full understanding of roles and obligations for train planners, facilitators / evaluators, and individuals. Moreover, the documentation contains templates for the preliminary invitation to individuals, a slide deck to make use of for each planning conferences and conduct, a suggestions type to distribute to individuals post-exercise, and an After Motion Report. At the side of choosing one of many above scenario manuals, your train planning workforce will be capable of absolutely develop your individual tabletop train and replace data sharing processes; emergency response protocols; and restoration plans, insurance policies, and procedures.