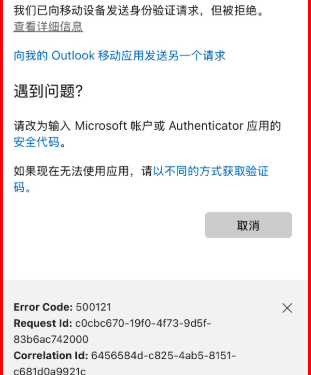
A single person couldn’t log in through Multi-Issue Authentication. SMS code would say it was despatched, wouldn’t come by. Telephone name additionally wouldn’t come by. Attempting to arrange one other MFA methodology aka.ms/mfasetup would obtain one among these errors:
You’re blocked from performing this operation. Please contact your administrator for assist.
We’re sorry, we bumped into an issue. Please choose “Subsequent to strive once more.
Signs
Troubleshooting Steps
There’s a number of areas you possibly can verify for blocked customers similar to: