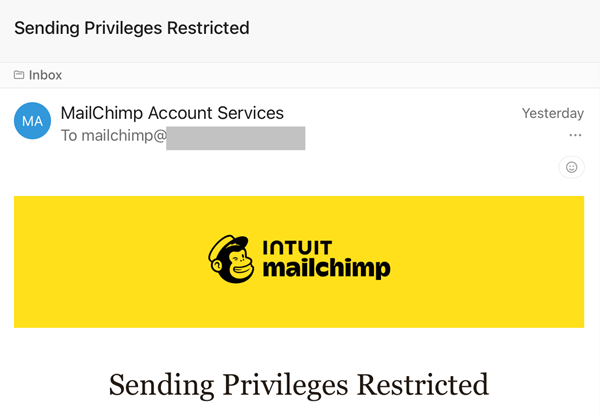
You understand once you’re actually jet lagged and actually drained and the cogs in your head are simply transferring that little bit too sluggish? That is me proper now, and the penny has simply dropped {that a} Mailchimp phish has grabbed my credentials, logged into my account and exported the mailing listing for this weblog. I am intentionally protecting this publish very succinct to make sure the message goes out to my impacted subscribers ASAP, then I will replace the publish with extra particulars. However as a fast abstract, I awoke in London this morning to the next:
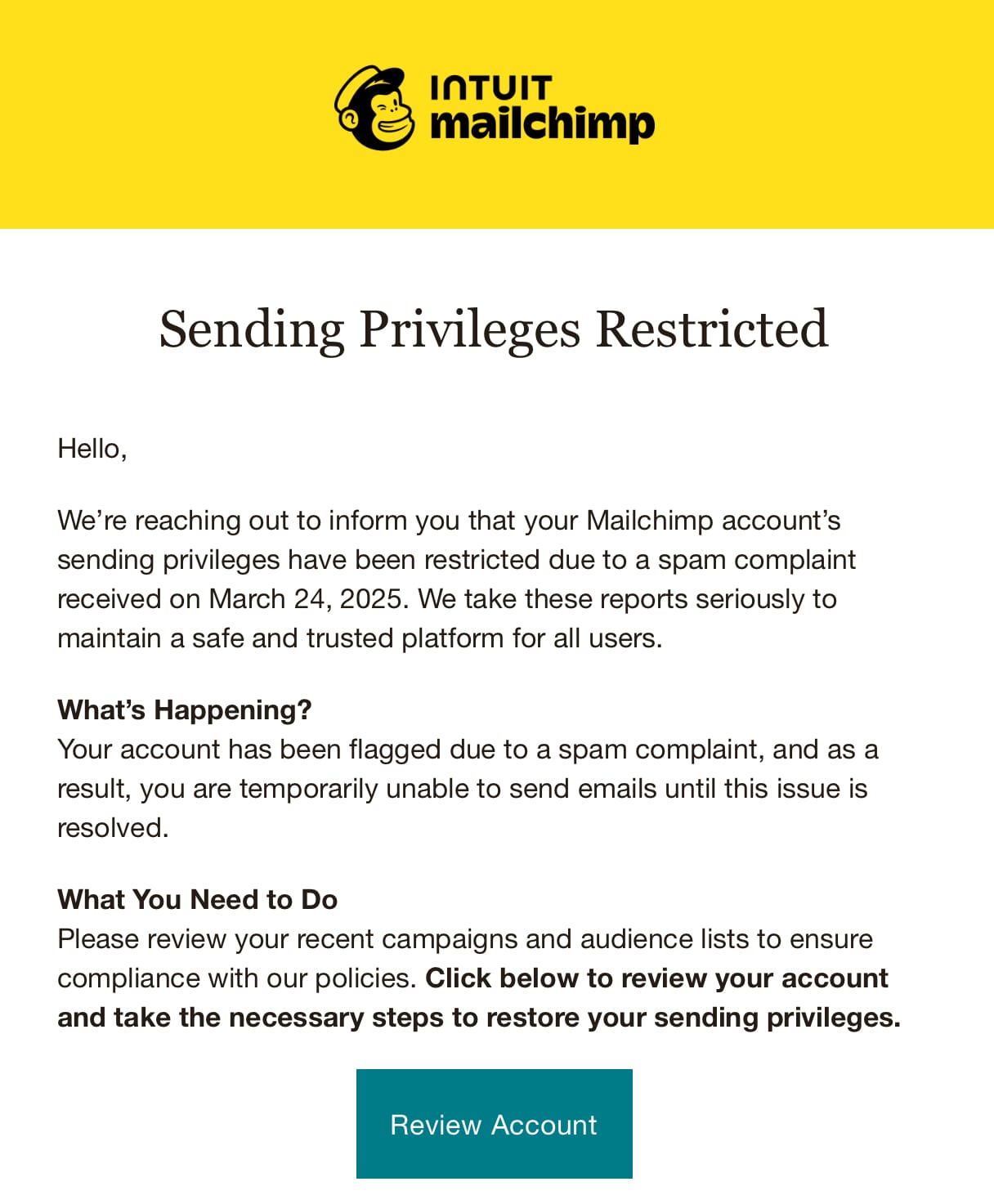
I went to the hyperlink which is on mailchimp-sso.com and entered my credentials which – crucially – didn’t auto-complete from 1Password. I then entered the OTP and the web page hung. Moments later, the penny dropped, and I logged onto the official web site, which Mailchimp confirmed by way of a notification e mail which confirmed my London IP handle:
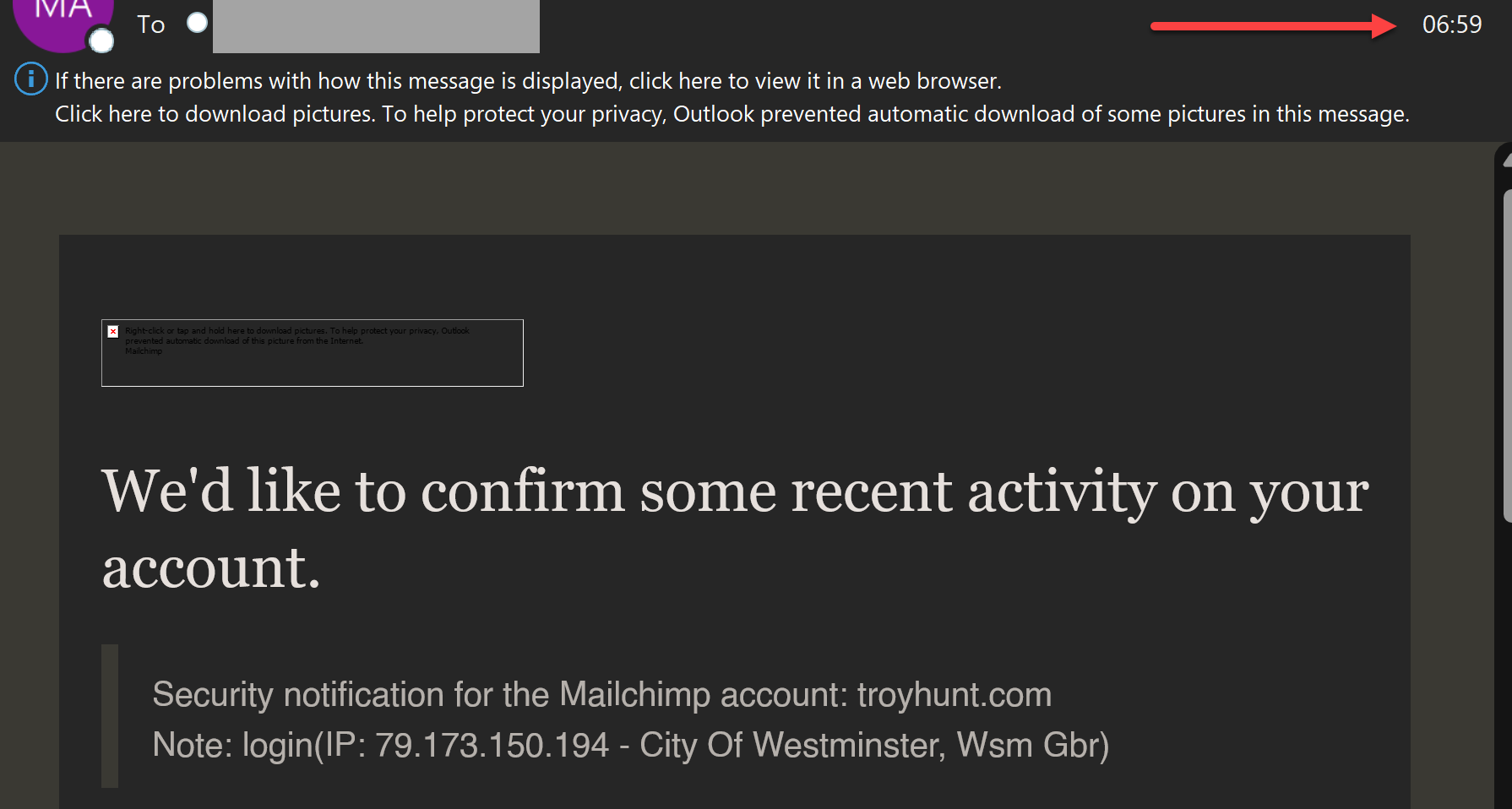
I instantly modified my password, however not earlier than I obtained an alert about my mailing listing being exported from an IP handle in New York:
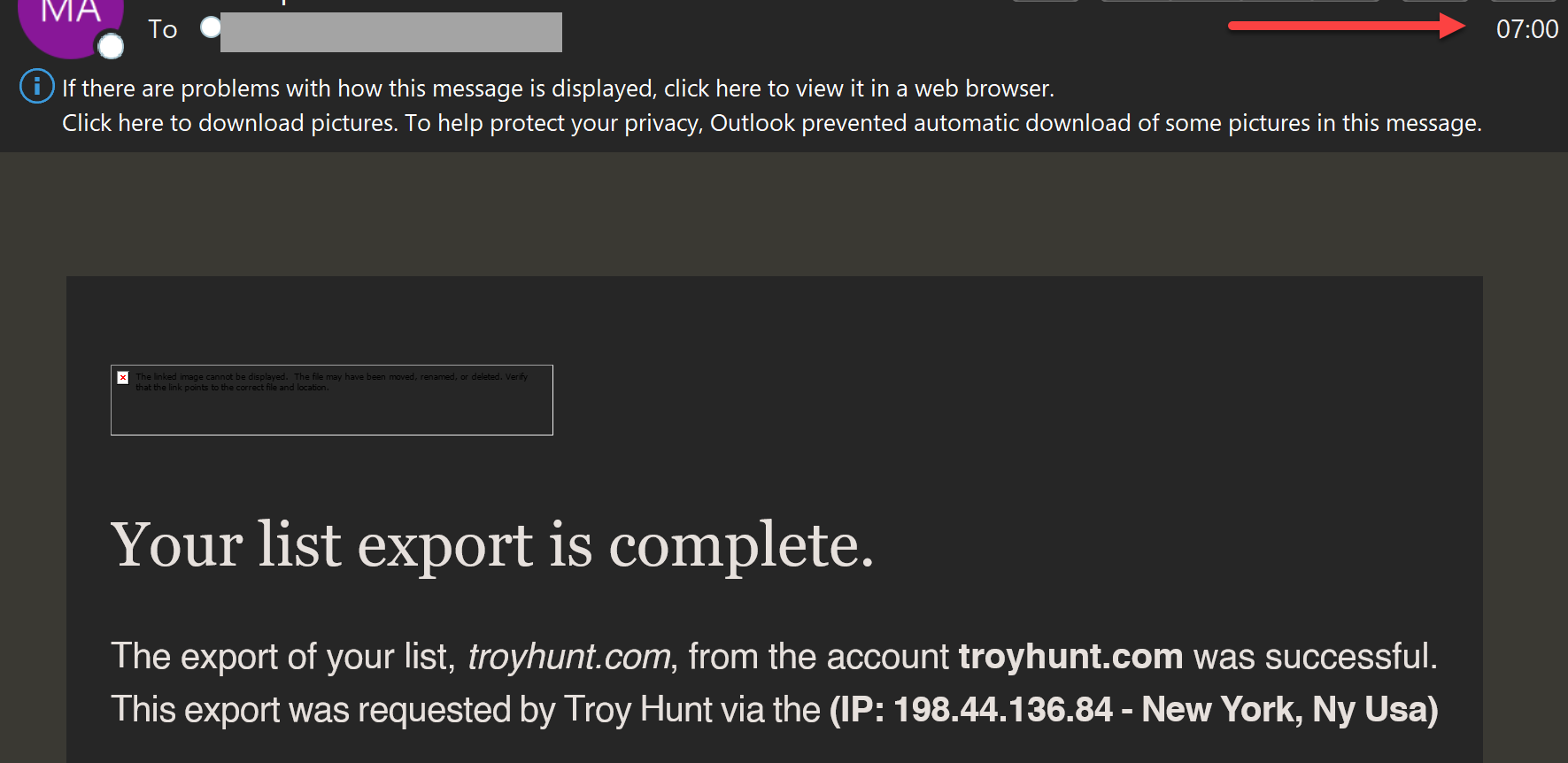
And, moments after that, the login alert from the identical IP:
This was clearly extremely automated and designed to instantly export the listing earlier than the sufferer may take preventative measures.
There are roughly 16k data in that export containing data Mailchimp routinely collects they usually seem as follows:
[redacted]@gmail.com,Weekly,https://www.troyhunt.com/i-now-own-the-coinhive-domain-heres-how-im-fighting-cryptojacking-and-doing-good-things-with-content-security-policies/#subscribe,2,"2024-04-13 22:03:08",160.154.[redacted].[redacted],"2024-04-13 22:00:50",160.154.[redacted].[redacted],5.[redacted lat],'-4.[redacted long],0,0,Africa/Abidjan,CI,AB,"2024-04-13 22:03:08",130912487,3452386287,,Each lively subscriber on my listing will shortly obtain an e mail notification by advantage of this weblog publish going out. Sadly, the export additionally consists of individuals who’ve unsubscribed (why does Mailchimp maintain these?!) so I will must work out how you can deal with these ones individually. I have been in contact with Mailchimp however do not have a reply but, I will replace this publish with extra data when I’ve it.
I am enormously annoyed with myself for having fallen for this, and I apologise to anybody on that listing. Clearly, be careful for spam or additional phishes and verify again right here or by way of the social channels within the nav bar above for extra. Paradoxically, I am in London visiting authorities companions, and I spent a few hours with the Nationwide Cyber Safety Centre yesterday speaking about how we are able to higher promote passkeys, partially on account of their phishing-resistant nature. 🤦♂️
Extra quickly, I’ve hit the publish button on this 34 minutes after the time stamp in that first e mail above.
Extra Stuff From After Preliminary Publish
Each Monday morning after I’m at residence, I head right into a radio studio and do a section on scams. It is consumer-facing so we’re speaking to the “normies” and at any time when somebody calls in and talks about being caught within the rip-off, the sentiment is similar: “I really feel so silly”. That, mates, is me proper now. Past acknowledging my very own foolishness, let me proceed with some extra ideas:
Firstly, I’ve obtained a gazillion related phishes earlier than that I’ve recognized early, so what was totally different about this one? Tiredness, was a significant component. I wasn’t alert sufficient, and I did not correctly assume by way of what I used to be doing. The attacker had no manner of understanding that (I haven’t got any purpose to suspect this was focused particularly at me), however all of us have moments of weak point and if the phish instances simply completely with that, nicely, right here we’re.
Secondly, studying it once more now, that is a very well-crafted phish. It socially engineered me into believing I would not be capable to ship out my e-newsletter so it triggered “worry”, however it wasn’t all bells and whistles about one thing horrible occurring if I did not take quick motion. It created simply the correct amount of urgency with out being excessive.
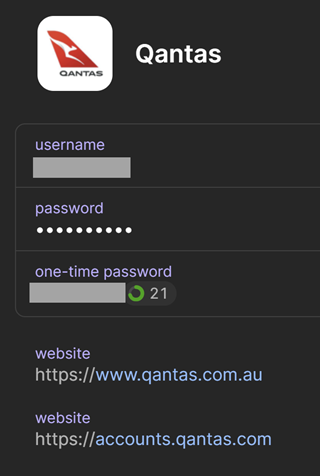
Thirdly, the factor that ought to have saved my bacon was the credentials not auto-filling from 1Password, so why did not I cease there? As a result of that is commonplace. There are such a lot of providers the place you’ve got registered on one area (and that handle is saved in 1Password), you then legitimately go online to a special area. For instance, this is my Qantas entry:
And the ultimate thought for now could be extra a frustration that Mailchimp did not routinely delete the info of people that unsubscribed. There are 7,535 e mail addresses on that listing which is sort of half of all addresses in that export. I must undergo the account settings and see if this was merely a setting I hadn’t toggled or one thing related, however the inclusion of these addresses was clearly fully pointless. I additionally do not know why IP addresses have been captured or how the lat and lengthy is calculated however given I’ve by no means seen a immediate for entry to the GPS, I think about it is in all probability derived from the IP.
I will park this right here and do a deeper technical dive later in the present day that addresses a few of the points I’ve raised above.
The Technical Bits
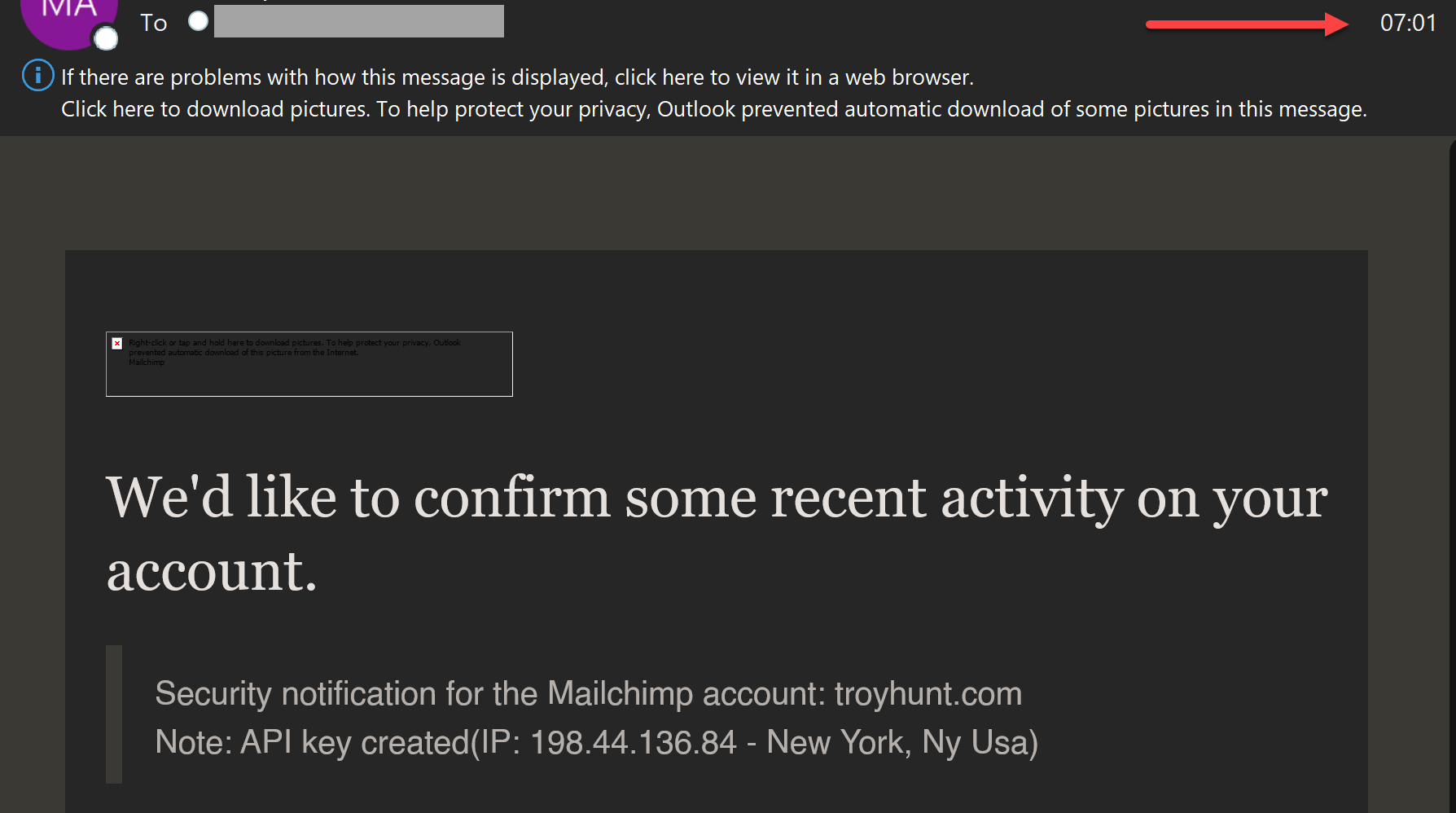
I will maintain penning this little by little (you might even see it seem partly completed whereas studying, so give the web page a refresh in a while), beginning with the API key that was created:
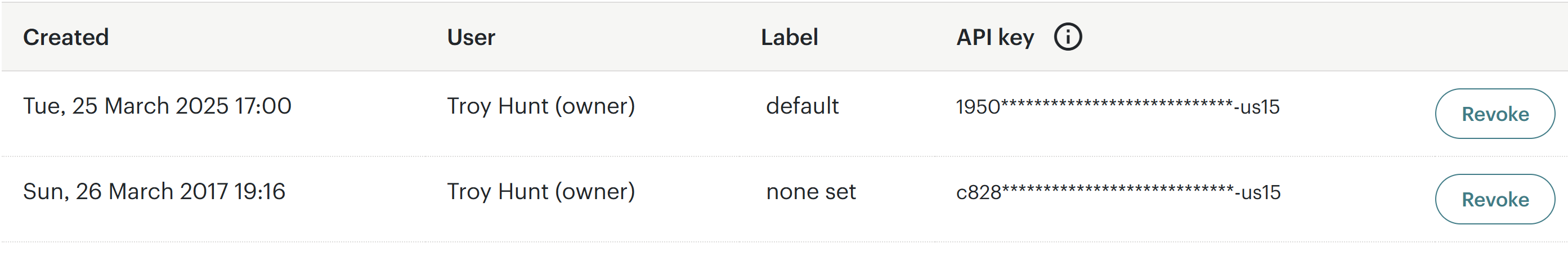
This has now been deleted so together with rolling the password, there ought to now not be any persistent entry to the account.
Sadly, Mailchimp does not supply phishing-resistant 2FA:
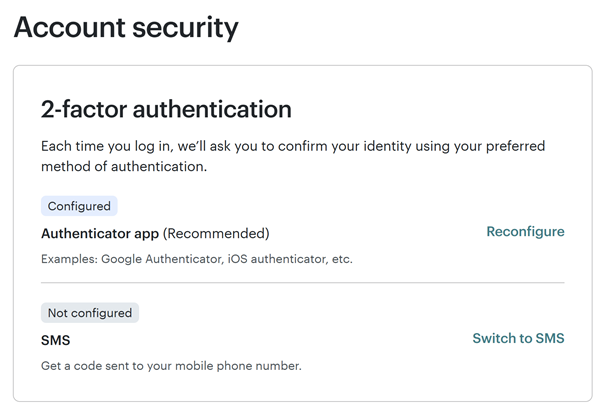
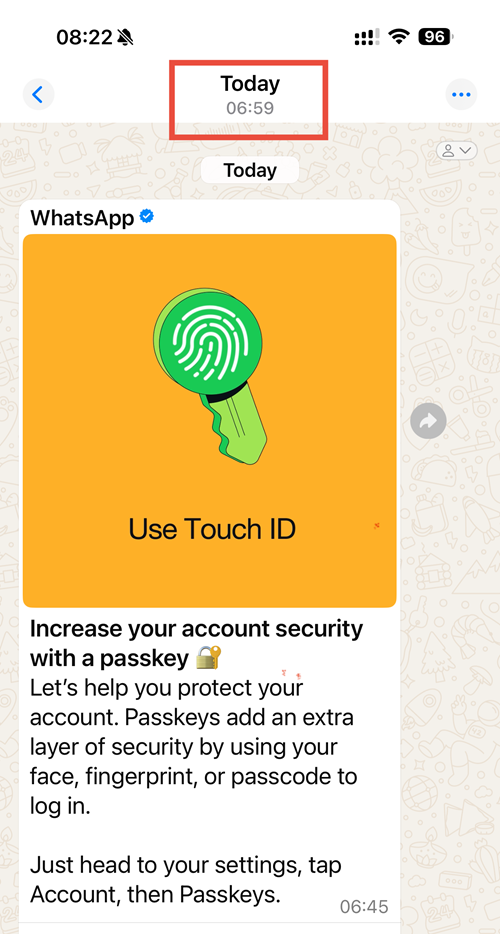
In no way would I encourage folks not to allow 2FA by way of OTP, however let this be a lesson as to how fully ineffective it’s towards an automatic phishing assault that may merely relay the OTP as quickly because it’s entered. On that be aware, one other ridiculous coincidence is that in the identical minute that I fell for this assault, I might taken a display screen cap of the WhatsApp message under and proven Charlotte – “See, this reinforces what we have been speaking about with the NCSC yesterday in regards to the significance of passkeys”:
One other attention-grabbing angle to that is the handle the phish was despatched to:
The remainder of that handle might be fairly predictable (and I do publish my full “regular” handle on the contact web page of this weblog, so it is not like I conceal it from the general public), however I discover it attention-grabbing that the phish got here to an handle solely used for Mailchimp. Which leaves two potentialities:
- Somebody particularly focused me and knew upfront the sample I exploit for the handle I signal as much as providers with. They obtained it proper first go with none mail going to different addresses.
- Somebody obtained the handle from some other place, and I’ve solely ever used it in a single place…
Making use of some Occam’s razor, it is the latter. I discover the previous extremely unlikely, and I might be very to listen to from anybody else who makes use of Mailchimp and obtained certainly one of these phishes.
Nonetheless on e mail addresses, I initially learn the phish on my iThing and Outlook rendered it as you see within the picture above. At this level, I used to be already on the hook as I meant to login and restore my account, so the best way the handle then rendered on the PC did not actually stand out to me after I switched units:
That is so rattling apparent 🤦♂️ The statement right here is that by not rendering the sender’s handle, Outlook on iOS hid the phish. However having mentioned that, not at all are you able to depend on the handle as a stable indicator of authenticity however on this case, it will have helped.
Curious as to why unsubscribed customers have been within the corpus of exported knowledge, I went trying to find solutions. At no level does Mailchimp’s web page on unsubscribing point out something about not deleting the person’s knowledge after they decide out of receiving future emails. Holding in thoughts that that is AI-generated, Google offered the next overview:
That “Objective of Holding Unsubscribes” part feels notably icky and once more, that is the AI and never Mailchimp’s phrases, however it appears to be on level. I can undergo and delete unsubscribed addresses (and I will do this shortly as the very last thing I’ll do now could be rush into one thing else), however then it appears like that must be a daily course of. This can be a large blindspot on Mailchimp’s behalf IMHO and I’ll present that suggestions to them immediately (simply remembered I do know some of us there).
I simply went to go and verify on the phishing website with the expectation of submitting it to Google Protected Looking, however it appears like that can now not be vital:
2 hours and quarter-hour after it snared my creds, Cloudflare has killed the location. I did see a Cloudflare anti-automation widget on the phishing web page when it first loaded and later questioned if that was faux or they have been genuinely fronting the web page, however I suppose that query is now answered. I do know there will be calls of “why did not Cloudflare block this when it was first arrange”, however I keep (as I’ve earlier than of their defence), that it is enormously exhausting to do this based mostly on area or web page construction alone with out making a heap of false positives.
On the query of the lat and lengthy within the knowledge, I simply grabbed my very own data and located an IP handle belonging to my mobile telco. I had two data (I exploit them to check each the every day and weekly posts), each with the identical IP handle and created inside a minute of one another. One had a geolocation in Brisbane and the opposite in far north Queensland, about 1,700km away. In different phrases, the coords don’t pinpoint the placement of the subscriber, however the file does include “australia/brisbane,au,qld” so there’s some tough geolocation knowledge in there.
Loading the Checklist into Have I Been Pwned
When I’ve conversations with breached corporations, my messaging is crystal clear: be clear and expeditious in your reporting of the incident and prioritise speaking along with your prospects. Me doing something lower than that might be hypocritical, together with how I then deal with the info from the breach, particularly including it to HIBP. As such, I’ve now loaded the breach and notifications are going out to six.6k impacted particular person subscribers and one other 2.4k monitoring domains with impacted e mail addresses.
Searching for silver linings within the incident, I’m certain I’ll refer this weblog publish to organisations I disclose future breaches to. I’ll level out upfront that although the info is “simply” e mail addresses and the danger to people doesn’t current a probability of significant hurt or threat their rights and freedoms (learn that weblog publish for extra), it’s merely the correct factor to do. Briefly, for many who learn this in future, don’t simply as I say, however as I do.
The Washup
I emailed a few contacts at Mailchimp earlier in the present day and put two inquiries to them:
- Are passkeys in your roadmap
- The place does Mailchimp stand on “unsubscribe” not deleting the info
Various folks have commented on social media in regards to the second level presumably being to make sure that somebody who unsubscribes can’t then later be resubscribed. I’m undecided that argument makes a number of sense, however I’d wish to see folks a minimum of being given the selection. I’m going to attend on their suggestions earlier than deciding if I ought to delete all of the unsubscribed emails myself, I’m not even certain if that’s potential by way of the UI or requires scripting towards the API,.
The irony of the timing with this occurring simply as I’ve been having passkey discussions with the NCSC is one thing I’m going to deal with as a chance. Proper earlier than this incident, I’d already determined to put in writing a weblog publish for the normies about passkey, and now I’ve the right instance of their worth. I’d additionally mentioned with the NCSC about making a passkey equal of my whynohttps.com mission which highlighted the most important providers not implementing HTTPS by default. As such, I’ve simply registered whynopasskeys.com (and its singular equal) and can begin considering extra about how you can construct that out so we are able to collectively put some strain on the providers that don’t help unphishable second elements. I truly tried to register that area while out strolling in the present day, solely to be met with the next courtesy of DNSimple:
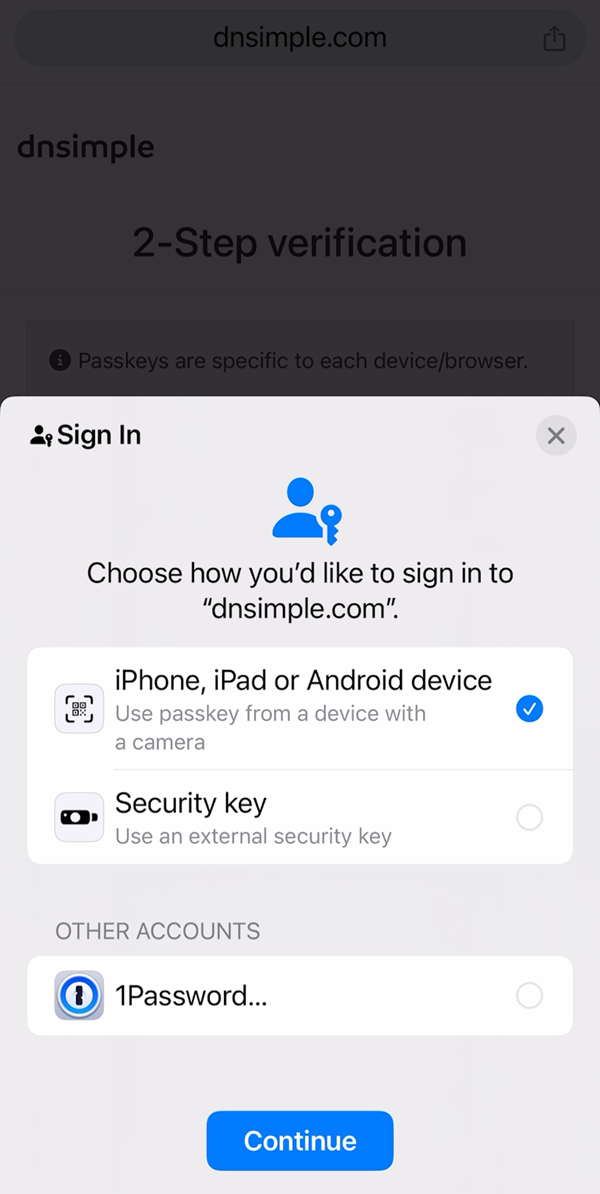
Utilizing a U2F key on actually vital stuff (like my area registrar) highlights the worth of this type of auth. At this time’s phish couldn’t have occurred towards this account, nor the opposite essential ones utilizing a phishing resistant second issue and we have to collectively push orgs on this path.
Honest apologies to anybody impacted by this, however on stability I feel this may do extra good than hurt and I encourage everybody to share this expertise broadly.
Replace 1: I will maintain including extra ideas right here by way of updates, particularly if there’s good suggestions or questions from the group. One factor I might meant so as to add earlier is that the extra I ponder this, the extra possible I feel it’s that my distinctive Mailchimp handle was obtained from someplace versus guessed in any focused style. A potential clarification is the safety incident that they had in 2022, which largely focused crypto-related lists, however I think about would possible have offered entry to the e-mail addresses of many extra prospects too. I will put that to them after I get a response to my earlier e mail.
Replace 2: I now have an open case with Mailchimp they usually’ve suggested that “login and sending for the account have been disabled to assist forestall unauthorized use of the account throughout our investigation”. I think this explains why some persons are unable to now signal as much as the e-newsletter, I will try to get that reinstated ASAP (I might rolled creds instantly and let’s face it, the horse has already bolted).
Pondering this even additional, I’m wondering if Mailchimp has any anti-automation controls on login? The credentials I entered into the phishing website have been clearly routinely replayed to the professional website, which suggests one thing there’s missing.
I additionally realised one other issue that pre-conditioned me to enter credentials into what I assumed was Mailchimp is their very short-lived authentication classes. Each time I am going again to the location, I must re-authenticate and while the blame nonetheless clearly lies with me, I am used to logging again in on each go to. Holding a trusted system auth’d for an extended interval would possible have raised a flag on my return to the location if I wasn’t nonetheless logged in.
Replace 3: Mailchimp has now restored entry to my account and the e-newsletter subscription service is working once more. Here is what they’ve mentioned:
We’ve reviewed the exercise and have come to the identical conclusion that the unauthorized export and API key from 198.44.136.84 was the scope of the entry. Given we all know how the entry came about, the API key has been deleted, and the password has been reset, now we have restored your entry to the account.
They’ve additionally acknowledged a number of excellent questions I’ve (resembling whether or not passkeys are on the roadmap) and have handed them alongside to the related get together. I will replace this publish as soon as I’ve solutions.
There’s been a number of dialogue round “Mailchimp are violating my native privateness legal guidelines by not deleting emails after I unsubscribe”, and that is one of many excellent questions I’ve despatched them. However on that, I’ve had a number of folks contact me and level out this isn’t the case because the handle must be retained with a view to guarantee an opted-out particular person is not later emailed if their handle is imported from one other supply. Learn this explainer from the UK’s ICO on suppression lists, particularly this para:
As a result of we don’t contemplate {that a} suppression listing is used for direct advertising functions, there is no such thing as a automated proper for folks to have their data on such a listing deleted.
I think this explains Mailchimp’s place, however I recommend that needs to be clearer through the unsubscribe course of. I simply went by way of and examined it and at no time is it clear the e-mail handle shall be retained for the aim of supression:
My suggestion could be to comply with our method for Have I Been Pwned the place we give folks three decisions and permit them to decide on how they’d like their knowledge to be dealt with:
At current, Mailchimp is successfully implementing the primary choice we offer and the oldsters which can be upset have been anticipating the final choice. Hopefully they’re going to contemplate a extra self-empowering method to how folks’s knowledge is dealt with, I will replace this weblog publish as soon as I’ve their response.
Replace 4: Somebody has identified that the sending e mail handle within the phish truly belongs to a Belgian cleansing firm referred to as Group-f. It is commonplace for addresses like this for use to ship malicious mail as they normally do not have a adverse status and extra simply cross by way of spam filters. It additionally signifies a potential compromise on their finish, so I’ve now reached to them to report the incident.
Replace 5: I have been contacted by somebody that runs a widely known web site that obtained the identical phishing e mail as me. They made the next statement relating to the handle that obtained the phish:
We’ve subscribed to Mailchimp with an handle that’s solely used to subscribe to providers, no outgoing communication from us. The phishing emails have been delivered to precisely this handle, could not but discover them on some other handle. This makes me very a lot consider that risk #2 is the case – they obtained the handle from someplace.
This aligns with my earlier statement {that a} buyer listing could have been obtained from Mailchimp and used to ship the phishing emails. They went on to say they have been seeing a number of subsequent phishes focusing on their Mailchimp account.
Btw, we obtained some extra (Mailchimp) phishing emails in the present day — similar type, this time 4 instances writing a few new login detected, and as soon as that an abuse report was obtained and we wanted to take quick motion.
{That a} buyer listing could have been compromised was one of many questions I put to Mailchimp and am nonetheless awaiting a solution on. That was about 36 hours in the past now, so I’ve simply given them a bit of nudge.
Replace 6: There have been a number of recommendations that Mailchimp needs to be storing the hashes of unsubscribed emails fairly than the complete addresses within the clear. I perceive the sentiment, and it does supply some safety, however it not at all ticks the “we now not have the handle” field. That is merely pseudoanonymisation, and the hashed handle might be resolved again to the clear in case you have a listing of plain textual content candidates to hash and examine them to. There is a good explainer of this within the reply to this query on Safety Stack Alternate about hashing e mail addresses for GDPR compliance. IMHO, my instance of how we deal with this in HIBP is the gold customary that Mailchimp needs to be implementing.
And there is additionally one other drawback: wanting cracking the hashed addresses, you possibly can by no means export a listing of unsubscribed e mail addresses, for instance, in the event you needed to alter mail marketing campaign supplier. The one manner that might work is that if the hashing algorithm is similar within the vacation spot service, otherwise you construct another degree of abstraction at some other future level the place you might want to examine plain textual content values to the hashed impression listing. It is messy, very messy.
You understand once you’re actually jet lagged and actually drained and the cogs in your head are simply transferring that little bit too sluggish? That is me proper now, and the penny has simply dropped {that a} Mailchimp phish has grabbed my credentials, logged into my account and exported the mailing listing for this weblog. I am intentionally protecting this publish very succinct to make sure the message goes out to my impacted subscribers ASAP, then I will replace the publish with extra particulars. However as a fast abstract, I awoke in London this morning to the next:

I went to the hyperlink which is on mailchimp-sso.com and entered my credentials which – crucially – didn’t auto-complete from 1Password. I then entered the OTP and the web page hung. Moments later, the penny dropped, and I logged onto the official web site, which Mailchimp confirmed by way of a notification e mail which confirmed my London IP handle:

I instantly modified my password, however not earlier than I obtained an alert about my mailing listing being exported from an IP handle in New York:

And, moments after that, the login alert from the identical IP:

This was clearly extremely automated and designed to instantly export the listing earlier than the sufferer may take preventative measures.
There are roughly 16k data in that export containing data Mailchimp routinely collects they usually seem as follows:
[redacted]@gmail.com,Weekly,https://www.troyhunt.com/i-now-own-the-coinhive-domain-heres-how-im-fighting-cryptojacking-and-doing-good-things-with-content-security-policies/#subscribe,2,"2024-04-13 22:03:08",160.154.[redacted].[redacted],"2024-04-13 22:00:50",160.154.[redacted].[redacted],5.[redacted lat],'-4.[redacted long],0,0,Africa/Abidjan,CI,AB,"2024-04-13 22:03:08",130912487,3452386287,,Each lively subscriber on my listing will shortly obtain an e mail notification by advantage of this weblog publish going out. Sadly, the export additionally consists of individuals who’ve unsubscribed (why does Mailchimp maintain these?!) so I will must work out how you can deal with these ones individually. I have been in contact with Mailchimp however do not have a reply but, I will replace this publish with extra data when I’ve it.
I am enormously annoyed with myself for having fallen for this, and I apologise to anybody on that listing. Clearly, be careful for spam or additional phishes and verify again right here or by way of the social channels within the nav bar above for extra. Paradoxically, I am in London visiting authorities companions, and I spent a few hours with the Nationwide Cyber Safety Centre yesterday speaking about how we are able to higher promote passkeys, partially on account of their phishing-resistant nature. 🤦♂️
Extra quickly, I’ve hit the publish button on this 34 minutes after the time stamp in that first e mail above.
Extra Stuff From After Preliminary Publish
Each Monday morning after I’m at residence, I head right into a radio studio and do a section on scams. It is consumer-facing so we’re speaking to the “normies” and at any time when somebody calls in and talks about being caught within the rip-off, the sentiment is similar: “I really feel so silly”. That, mates, is me proper now. Past acknowledging my very own foolishness, let me proceed with some extra ideas:
Firstly, I’ve obtained a gazillion related phishes earlier than that I’ve recognized early, so what was totally different about this one? Tiredness, was a significant component. I wasn’t alert sufficient, and I did not correctly assume by way of what I used to be doing. The attacker had no manner of understanding that (I haven’t got any purpose to suspect this was focused particularly at me), however all of us have moments of weak point and if the phish instances simply completely with that, nicely, right here we’re.
Secondly, studying it once more now, that is a very well-crafted phish. It socially engineered me into believing I would not be capable to ship out my e-newsletter so it triggered “worry”, however it wasn’t all bells and whistles about one thing horrible occurring if I did not take quick motion. It created simply the correct amount of urgency with out being excessive.
Thirdly, the factor that ought to have saved my bacon was the credentials not auto-filling from 1Password, so why did not I cease there? As a result of that is commonplace. There are such a lot of providers the place you’ve got registered on one area (and that handle is saved in 1Password), you then legitimately go online to a special area. For instance, this is my Qantas entry:

And the ultimate thought for now could be extra a frustration that Mailchimp did not routinely delete the info of people that unsubscribed. There are 7,535 e mail addresses on that listing which is sort of half of all addresses in that export. I must undergo the account settings and see if this was merely a setting I hadn’t toggled or one thing related, however the inclusion of these addresses was clearly fully pointless. I additionally do not know why IP addresses have been captured or how the lat and lengthy is calculated however given I’ve by no means seen a immediate for entry to the GPS, I think about it is in all probability derived from the IP.
I will park this right here and do a deeper technical dive later in the present day that addresses a few of the points I’ve raised above.
The Technical Bits
I will maintain penning this little by little (you might even see it seem partly completed whereas studying, so give the web page a refresh in a while), beginning with the API key that was created:

This has now been deleted so together with rolling the password, there ought to now not be any persistent entry to the account.
Sadly, Mailchimp does not supply phishing-resistant 2FA:

In no way would I encourage folks not to allow 2FA by way of OTP, however let this be a lesson as to how fully ineffective it’s towards an automatic phishing assault that may merely relay the OTP as quickly because it’s entered. On that be aware, one other ridiculous coincidence is that in the identical minute that I fell for this assault, I might taken a display screen cap of the WhatsApp message under and proven Charlotte – “See, this reinforces what we have been speaking about with the NCSC yesterday in regards to the significance of passkeys”:

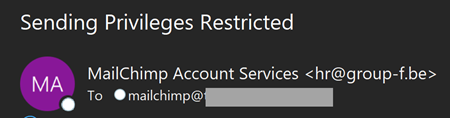
One other attention-grabbing angle to that is the handle the phish was despatched to:

The remainder of that handle might be fairly predictable (and I do publish my full “regular” handle on the contact web page of this weblog, so it is not like I conceal it from the general public), however I discover it attention-grabbing that the phish got here to an handle solely used for Mailchimp. Which leaves two potentialities:
- Somebody particularly focused me and knew upfront the sample I exploit for the handle I signal as much as providers with. They obtained it proper first go with none mail going to different addresses.
- Somebody obtained the handle from some other place, and I’ve solely ever used it in a single place…
Making use of some Occam’s razor, it is the latter. I discover the previous extremely unlikely, and I might be very to listen to from anybody else who makes use of Mailchimp and obtained certainly one of these phishes.
Nonetheless on e mail addresses, I initially learn the phish on my iThing and Outlook rendered it as you see within the picture above. At this level, I used to be already on the hook as I meant to login and restore my account, so the best way the handle then rendered on the PC did not actually stand out to me after I switched units:

That is so rattling apparent 🤦♂️ The statement right here is that by not rendering the sender’s handle, Outlook on iOS hid the phish. However having mentioned that, not at all are you able to depend on the handle as a stable indicator of authenticity however on this case, it will have helped.
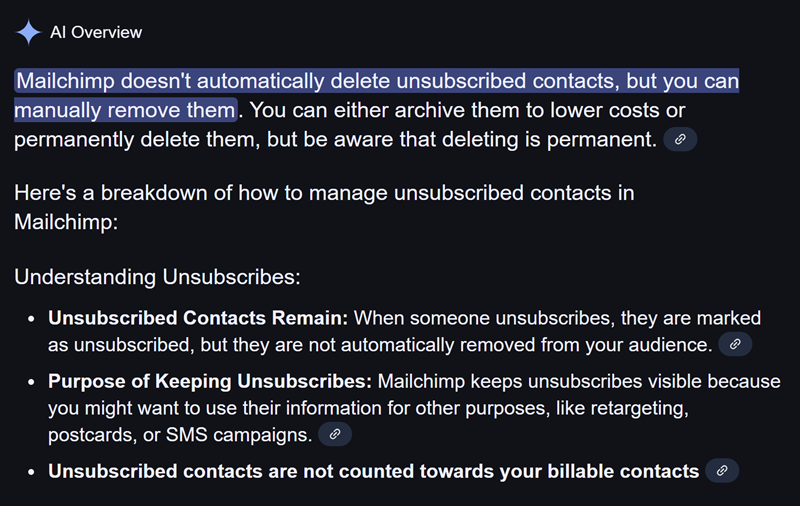
Curious as to why unsubscribed customers have been within the corpus of exported knowledge, I went trying to find solutions. At no level does Mailchimp’s web page on unsubscribing point out something about not deleting the person’s knowledge after they decide out of receiving future emails. Holding in thoughts that that is AI-generated, Google offered the next overview:

That “Objective of Holding Unsubscribes” part feels notably icky and once more, that is the AI and never Mailchimp’s phrases, however it appears to be on level. I can undergo and delete unsubscribed addresses (and I will do this shortly as the very last thing I’ll do now could be rush into one thing else), however then it appears like that must be a daily course of. This can be a large blindspot on Mailchimp’s behalf IMHO and I’ll present that suggestions to them immediately (simply remembered I do know some of us there).
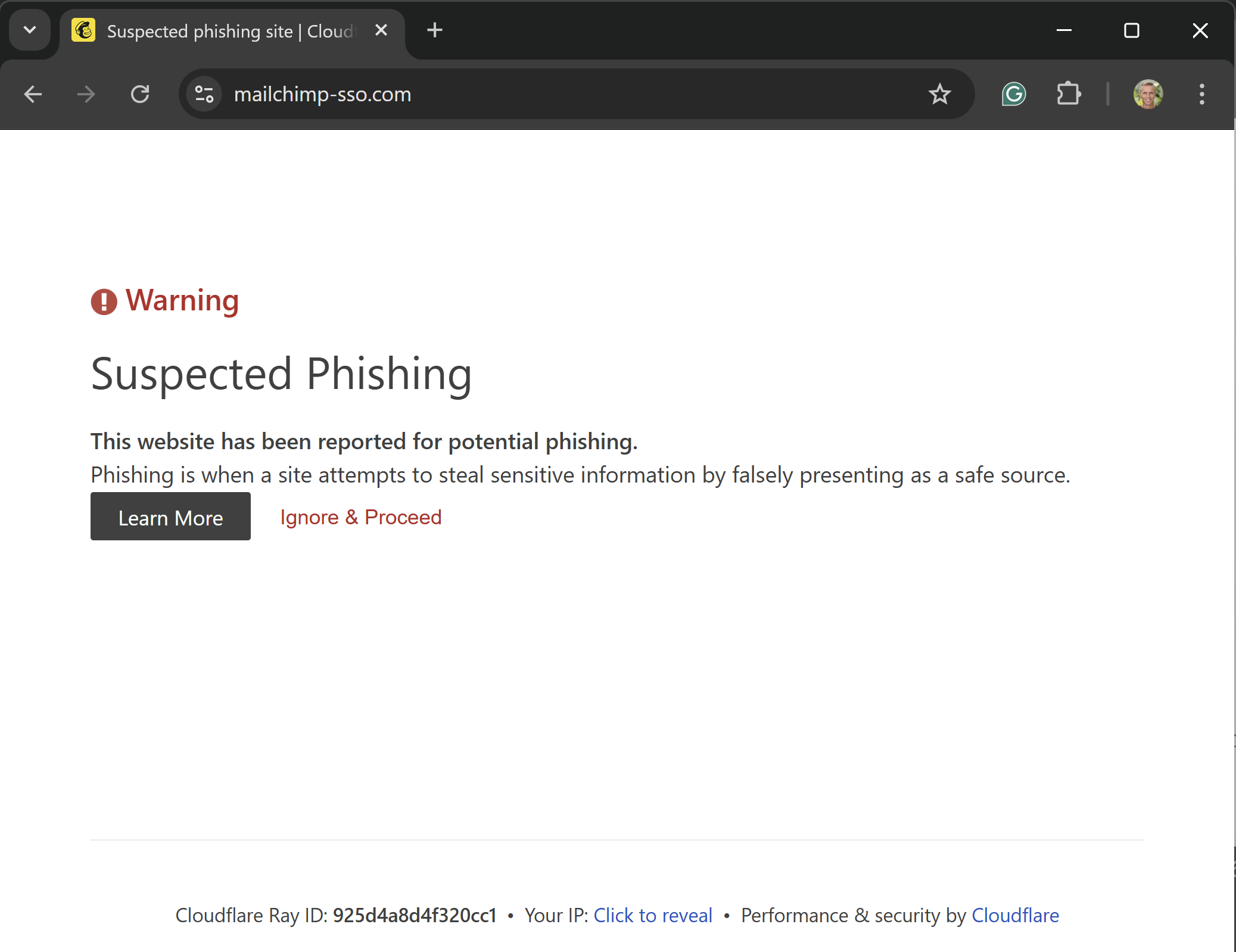
I simply went to go and verify on the phishing website with the expectation of submitting it to Google Protected Looking, however it appears like that can now not be vital:

2 hours and quarter-hour after it snared my creds, Cloudflare has killed the location. I did see a Cloudflare anti-automation widget on the phishing web page when it first loaded and later questioned if that was faux or they have been genuinely fronting the web page, however I suppose that query is now answered. I do know there will be calls of “why did not Cloudflare block this when it was first arrange”, however I keep (as I’ve earlier than of their defence), that it is enormously exhausting to do this based mostly on area or web page construction alone with out making a heap of false positives.
On the query of the lat and lengthy within the knowledge, I simply grabbed my very own data and located an IP handle belonging to my mobile telco. I had two data (I exploit them to check each the every day and weekly posts), each with the identical IP handle and created inside a minute of one another. One had a geolocation in Brisbane and the opposite in far north Queensland, about 1,700km away. In different phrases, the coords don’t pinpoint the placement of the subscriber, however the file does include “australia/brisbane,au,qld” so there’s some tough geolocation knowledge in there.
Loading the Checklist into Have I Been Pwned
When I’ve conversations with breached corporations, my messaging is crystal clear: be clear and expeditious in your reporting of the incident and prioritise speaking along with your prospects. Me doing something lower than that might be hypocritical, together with how I then deal with the info from the breach, particularly including it to HIBP. As such, I’ve now loaded the breach and notifications are going out to six.6k impacted particular person subscribers and one other 2.4k monitoring domains with impacted e mail addresses.
Searching for silver linings within the incident, I’m certain I’ll refer this weblog publish to organisations I disclose future breaches to. I’ll level out upfront that although the info is “simply” e mail addresses and the danger to people doesn’t current a probability of significant hurt or threat their rights and freedoms (learn that weblog publish for extra), it’s merely the correct factor to do. Briefly, for many who learn this in future, don’t simply as I say, however as I do.
The Washup
I emailed a few contacts at Mailchimp earlier in the present day and put two inquiries to them:
- Are passkeys in your roadmap
- The place does Mailchimp stand on “unsubscribe” not deleting the info
Various folks have commented on social media in regards to the second level presumably being to make sure that somebody who unsubscribes can’t then later be resubscribed. I’m undecided that argument makes a number of sense, however I’d wish to see folks a minimum of being given the selection. I’m going to attend on their suggestions earlier than deciding if I ought to delete all of the unsubscribed emails myself, I’m not even certain if that’s potential by way of the UI or requires scripting towards the API,.
The irony of the timing with this occurring simply as I’ve been having passkey discussions with the NCSC is one thing I’m going to deal with as a chance. Proper earlier than this incident, I’d already determined to put in writing a weblog publish for the normies about passkey, and now I’ve the right instance of their worth. I’d additionally mentioned with the NCSC about making a passkey equal of my whynohttps.com mission which highlighted the most important providers not implementing HTTPS by default. As such, I’ve simply registered whynopasskeys.com (and its singular equal) and can begin considering extra about how you can construct that out so we are able to collectively put some strain on the providers that don’t help unphishable second elements. I truly tried to register that area while out strolling in the present day, solely to be met with the next courtesy of DNSimple:

Utilizing a U2F key on actually vital stuff (like my area registrar) highlights the worth of this type of auth. At this time’s phish couldn’t have occurred towards this account, nor the opposite essential ones utilizing a phishing resistant second issue and we have to collectively push orgs on this path.
Honest apologies to anybody impacted by this, however on stability I feel this may do extra good than hurt and I encourage everybody to share this expertise broadly.
Replace 1: I will maintain including extra ideas right here by way of updates, particularly if there’s good suggestions or questions from the group. One factor I might meant so as to add earlier is that the extra I ponder this, the extra possible I feel it’s that my distinctive Mailchimp handle was obtained from someplace versus guessed in any focused style. A potential clarification is the safety incident that they had in 2022, which largely focused crypto-related lists, however I think about would possible have offered entry to the e-mail addresses of many extra prospects too. I will put that to them after I get a response to my earlier e mail.
Replace 2: I now have an open case with Mailchimp they usually’ve suggested that “login and sending for the account have been disabled to assist forestall unauthorized use of the account throughout our investigation”. I think this explains why some persons are unable to now signal as much as the e-newsletter, I will try to get that reinstated ASAP (I might rolled creds instantly and let’s face it, the horse has already bolted).
Pondering this even additional, I’m wondering if Mailchimp has any anti-automation controls on login? The credentials I entered into the phishing website have been clearly routinely replayed to the professional website, which suggests one thing there’s missing.
I additionally realised one other issue that pre-conditioned me to enter credentials into what I assumed was Mailchimp is their very short-lived authentication classes. Each time I am going again to the location, I must re-authenticate and while the blame nonetheless clearly lies with me, I am used to logging again in on each go to. Holding a trusted system auth’d for an extended interval would possible have raised a flag on my return to the location if I wasn’t nonetheless logged in.
Replace 3: Mailchimp has now restored entry to my account and the e-newsletter subscription service is working once more. Here is what they’ve mentioned:
We’ve reviewed the exercise and have come to the identical conclusion that the unauthorized export and API key from 198.44.136.84 was the scope of the entry. Given we all know how the entry came about, the API key has been deleted, and the password has been reset, now we have restored your entry to the account.
They’ve additionally acknowledged a number of excellent questions I’ve (resembling whether or not passkeys are on the roadmap) and have handed them alongside to the related get together. I will replace this publish as soon as I’ve solutions.
There’s been a number of dialogue round “Mailchimp are violating my native privateness legal guidelines by not deleting emails after I unsubscribe”, and that is one of many excellent questions I’ve despatched them. However on that, I’ve had a number of folks contact me and level out this isn’t the case because the handle must be retained with a view to guarantee an opted-out particular person is not later emailed if their handle is imported from one other supply. Learn this explainer from the UK’s ICO on suppression lists, particularly this para:
As a result of we don’t contemplate {that a} suppression listing is used for direct advertising functions, there is no such thing as a automated proper for folks to have their data on such a listing deleted.
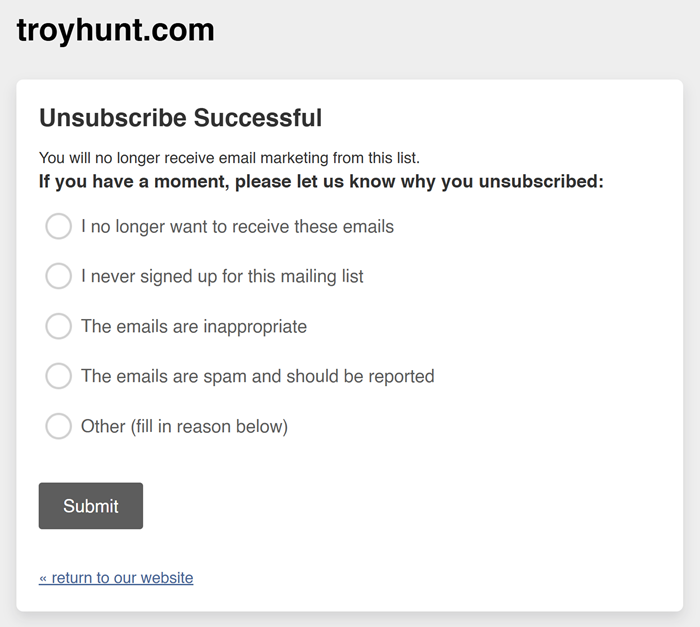
I think this explains Mailchimp’s place, however I recommend that needs to be clearer through the unsubscribe course of. I simply went by way of and examined it and at no time is it clear the e-mail handle shall be retained for the aim of supression:

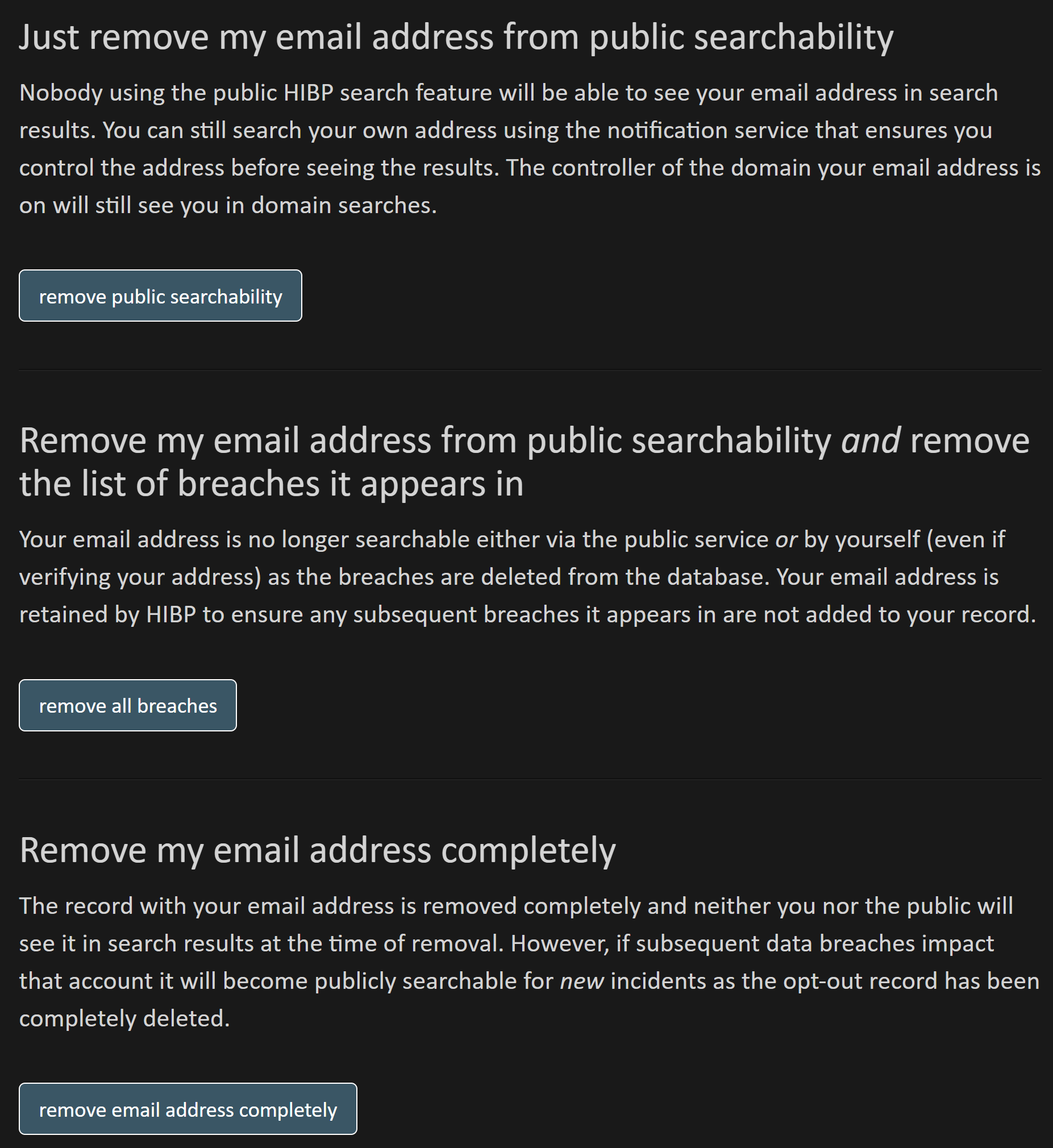
My suggestion could be to comply with our method for Have I Been Pwned the place we give folks three decisions and permit them to decide on how they’d like their knowledge to be dealt with:

At current, Mailchimp is successfully implementing the primary choice we offer and the oldsters which can be upset have been anticipating the final choice. Hopefully they’re going to contemplate a extra self-empowering method to how folks’s knowledge is dealt with, I will replace this weblog publish as soon as I’ve their response.
Replace 4: Somebody has identified that the sending e mail handle within the phish truly belongs to a Belgian cleansing firm referred to as Group-f. It is commonplace for addresses like this for use to ship malicious mail as they normally do not have a adverse status and extra simply cross by way of spam filters. It additionally signifies a potential compromise on their finish, so I’ve now reached to them to report the incident.
Replace 5: I have been contacted by somebody that runs a widely known web site that obtained the identical phishing e mail as me. They made the next statement relating to the handle that obtained the phish:
We’ve subscribed to Mailchimp with an handle that’s solely used to subscribe to providers, no outgoing communication from us. The phishing emails have been delivered to precisely this handle, could not but discover them on some other handle. This makes me very a lot consider that risk #2 is the case – they obtained the handle from someplace.
This aligns with my earlier statement {that a} buyer listing could have been obtained from Mailchimp and used to ship the phishing emails. They went on to say they have been seeing a number of subsequent phishes focusing on their Mailchimp account.
Btw, we obtained some extra (Mailchimp) phishing emails in the present day — similar type, this time 4 instances writing a few new login detected, and as soon as that an abuse report was obtained and we wanted to take quick motion.
{That a} buyer listing could have been compromised was one of many questions I put to Mailchimp and am nonetheless awaiting a solution on. That was about 36 hours in the past now, so I’ve simply given them a bit of nudge.
Replace 6: There have been a number of recommendations that Mailchimp needs to be storing the hashes of unsubscribed emails fairly than the complete addresses within the clear. I perceive the sentiment, and it does supply some safety, however it not at all ticks the “we now not have the handle” field. That is merely pseudoanonymisation, and the hashed handle might be resolved again to the clear in case you have a listing of plain textual content candidates to hash and examine them to. There is a good explainer of this within the reply to this query on Safety Stack Alternate about hashing e mail addresses for GDPR compliance. IMHO, my instance of how we deal with this in HIBP is the gold customary that Mailchimp needs to be implementing.
And there is additionally one other drawback: wanting cracking the hashed addresses, you possibly can by no means export a listing of unsubscribed e mail addresses, for instance, in the event you needed to alter mail marketing campaign supplier. The one manner that might work is that if the hashing algorithm is similar within the vacation spot service, otherwise you construct another degree of abstraction at some other future level the place you might want to examine plain textual content values to the hashed impression listing. It is messy, very messy.






