Authorities in the UK this week arrested 4 individuals aged 17 to twenty in reference to current knowledge theft and extortion assaults in opposition to the retailers Marks & Spencer and Harrods, and the British meals retailer Co-op Group. The breaches have been linked to a prolific however loosely-affiliated cybercrime group dubbed “Scattered Spider,” whose different current victims embody a number of airways.
The U.Ok.’s Nationwide Crime Company (NCA) declined confirm the names of these arrested, saying solely that they included two males aged 19, one other aged 17, and 20-year-old feminine.
Scattered Spider is the title given to an English-speaking cybercrime group identified for utilizing social engineering ways to interrupt into firms and steal knowledge for ransom, usually impersonating workers or contractors to deceive IT assist desks into granting entry. The FBI warned final month that Scattered Spider had lately shifted to focusing on firms within the retail and airline sectors.
KrebsOnSecurity has discovered the identities of two of the suspects. A number of sources near the investigation mentioned these arrested embody Owen David Flowers, a U.Ok. man alleged to have been concerned within the cyber intrusion and ransomware assault that shut down a number of MGM On line casino properties in September 2023. Those self same sources mentioned the girl arrested is or lately was in a relationship with Flowers.
Sources instructed KrebsOnSecurity that Flowers, who allegedly glided by the hacker handles “bo764,” “Holy,” and “Nazi,” was the group member who anonymously gave interviews to the media within the days after the MGM hack. His actual title was omitted from a September 2024 story in regards to the group as a result of he was not but charged in that incident.
The larger fish arrested this week is 19-year-old Thalha Jubair, a U.Ok. man whose alleged exploits below varied monikers have been well-documented in tales on this website. Jubair is believed to have used the nickname “Earth2Star,” which corresponds to a founding member of the cybercrime-focused Telegram channel “Star Fraud Chat.”
In 2023, KrebsOnSecurity printed an investigation into the work of three completely different SIM-swapping teams that phished credentials from T-Cellular workers and used that entry to supply a service whereby any T-Cell phone quantity may very well be swapped to a brand new gadget. Star Chat was by far probably the most energetic and consequential of the three SIM-swapping teams, who collectively broke into T-Cellular’s community greater than 100 occasions within the second half of 2022.

Jubair allegedly used the handles “Earth2Star” and “Star Ace,” and was a core member of a prolific SIM-swapping group working in 2022. Star Ace posted this picture to the Star Fraud chat channel on Telegram, and it lists varied costs for SIM-swaps.
Sources inform KrebsOnSecurity that Jubair additionally was a core member of the LAPSUS$ cybercrime group that broke into dozens of know-how firms in 2022, stealing supply code and different inner knowledge from tech giants together with Microsoft, Nvidia, Okta, Rockstar Video games, Samsung, T-Cellular, and Uber.
In April 2022, KrebsOnSecurity printed inner chat information from LAPSUS$, and people chats indicated Jubair was utilizing the nicknames Amtrak and Asyntax. At one level within the chats, Amtrak instructed the LAPSUS$ group chief to not share T-Cellular’s emblem in pictures despatched to the group as a result of he’d been beforehand busted for SIM-swapping and his dad and mom would suspect he was again at it once more.
As proven in these chats, the chief of LAPSUS$ ultimately determined to betray Amtrak by posting his actual title, cellphone quantity, and different hacker handles right into a public chat room on Telegram.
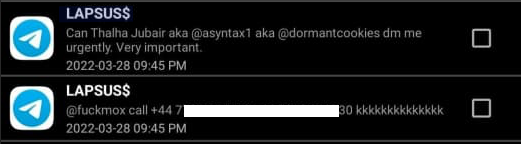
In March 2022, the chief of the LAPSUS$ knowledge extortion group uncovered Thalha Jubair’s title and hacker handles in a public chat room on Telegram.
That story in regards to the leaked LAPSUS$ chats linked Amtrak/Asyntax/Jubair to the identification “Everlynn,” the founding father of a cybercriminal service that bought fraudulent “emergency knowledge requests” focusing on the most important social media and e mail suppliers. In such schemes, the hackers compromise e mail accounts tied to police departments and authorities companies, after which ship unauthorized calls for for subscriber knowledge whereas claiming the knowledge being requested can’t anticipate a court docket order as a result of it pertains to an pressing matter of life and dying.
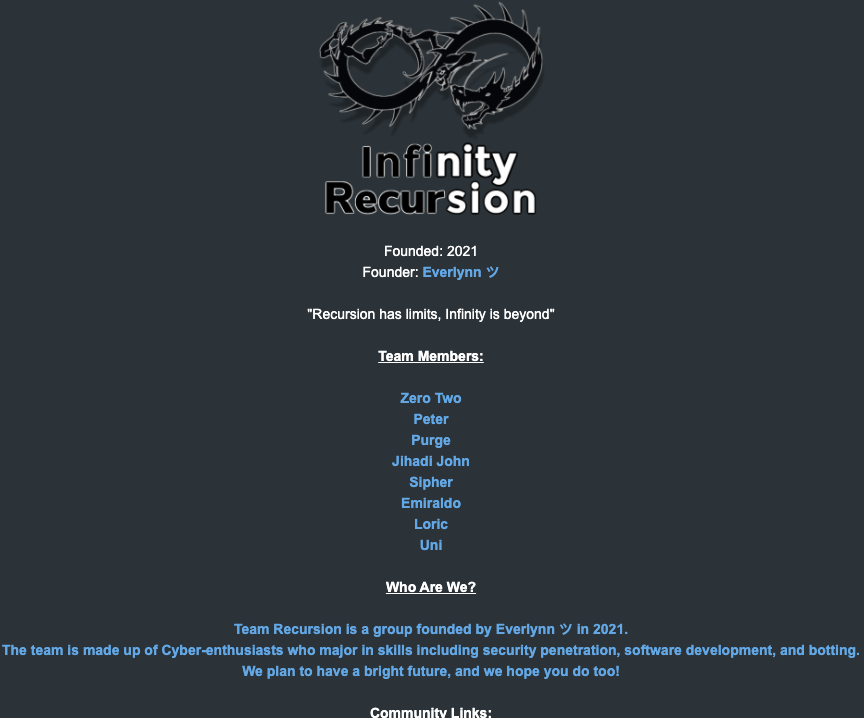
The roster of the now-defunct “Infinity Recursion” hacking workforce, from which some member of LAPSUS$ hail.
Sources say Jubair additionally used the nickname “Operator,” and that till lately he was the administrator of the Doxbin, a long-running and extremely poisonous on-line neighborhood that’s used to “dox” or publish deeply private data on individuals. In Might 2024, a number of widespread cybercrime channels on Telegram ridiculed Operator after it was revealed that he’d staged his personal kidnapping in a botched plan to throw off regulation enforcement investigators.
In November 2024, U.S. authorities charged 5 males aged 20 to 25 in reference to the Scattered Spider group, which has lengthy relied on recruiting minors to hold out its most dangerous actions. Certainly, lots of the group’s core members have been recruited from on-line gaming platforms like Roblox and Minecraft of their early teenagers, and have been perfecting their social engineering ways for years.
“There’s a clear sample that among the most wicked menace actors first joined cybercrime gangs at an exceptionally younger age,” mentioned Allison Nixon, chief analysis officer on the New York based mostly safety agency Unit 221B. “Cybercriminals arrested at 15 or youthful want severe intervention and monitoring to stop a years lengthy huge escalation.”
Authorities in the UK this week arrested 4 individuals aged 17 to twenty in reference to current knowledge theft and extortion assaults in opposition to the retailers Marks & Spencer and Harrods, and the British meals retailer Co-op Group. The breaches have been linked to a prolific however loosely-affiliated cybercrime group dubbed “Scattered Spider,” whose different current victims embody a number of airways.
The U.Ok.’s Nationwide Crime Company (NCA) declined confirm the names of these arrested, saying solely that they included two males aged 19, one other aged 17, and 20-year-old feminine.
Scattered Spider is the title given to an English-speaking cybercrime group identified for utilizing social engineering ways to interrupt into firms and steal knowledge for ransom, usually impersonating workers or contractors to deceive IT assist desks into granting entry. The FBI warned final month that Scattered Spider had lately shifted to focusing on firms within the retail and airline sectors.
KrebsOnSecurity has discovered the identities of two of the suspects. A number of sources near the investigation mentioned these arrested embody Owen David Flowers, a U.Ok. man alleged to have been concerned within the cyber intrusion and ransomware assault that shut down a number of MGM On line casino properties in September 2023. Those self same sources mentioned the girl arrested is or lately was in a relationship with Flowers.
Sources instructed KrebsOnSecurity that Flowers, who allegedly glided by the hacker handles “bo764,” “Holy,” and “Nazi,” was the group member who anonymously gave interviews to the media within the days after the MGM hack. His actual title was omitted from a September 2024 story in regards to the group as a result of he was not but charged in that incident.
The larger fish arrested this week is 19-year-old Thalha Jubair, a U.Ok. man whose alleged exploits below varied monikers have been well-documented in tales on this website. Jubair is believed to have used the nickname “Earth2Star,” which corresponds to a founding member of the cybercrime-focused Telegram channel “Star Fraud Chat.”
In 2023, KrebsOnSecurity printed an investigation into the work of three completely different SIM-swapping teams that phished credentials from T-Cellular workers and used that entry to supply a service whereby any T-Cell phone quantity may very well be swapped to a brand new gadget. Star Chat was by far probably the most energetic and consequential of the three SIM-swapping teams, who collectively broke into T-Cellular’s community greater than 100 occasions within the second half of 2022.

Jubair allegedly used the handles “Earth2Star” and “Star Ace,” and was a core member of a prolific SIM-swapping group working in 2022. Star Ace posted this picture to the Star Fraud chat channel on Telegram, and it lists varied costs for SIM-swaps.
Sources inform KrebsOnSecurity that Jubair additionally was a core member of the LAPSUS$ cybercrime group that broke into dozens of know-how firms in 2022, stealing supply code and different inner knowledge from tech giants together with Microsoft, Nvidia, Okta, Rockstar Video games, Samsung, T-Cellular, and Uber.
In April 2022, KrebsOnSecurity printed inner chat information from LAPSUS$, and people chats indicated Jubair was utilizing the nicknames Amtrak and Asyntax. At one level within the chats, Amtrak instructed the LAPSUS$ group chief to not share T-Cellular’s emblem in pictures despatched to the group as a result of he’d been beforehand busted for SIM-swapping and his dad and mom would suspect he was again at it once more.
As proven in these chats, the chief of LAPSUS$ ultimately determined to betray Amtrak by posting his actual title, cellphone quantity, and different hacker handles right into a public chat room on Telegram.

In March 2022, the chief of the LAPSUS$ knowledge extortion group uncovered Thalha Jubair’s title and hacker handles in a public chat room on Telegram.
That story in regards to the leaked LAPSUS$ chats linked Amtrak/Asyntax/Jubair to the identification “Everlynn,” the founding father of a cybercriminal service that bought fraudulent “emergency knowledge requests” focusing on the most important social media and e mail suppliers. In such schemes, the hackers compromise e mail accounts tied to police departments and authorities companies, after which ship unauthorized calls for for subscriber knowledge whereas claiming the knowledge being requested can’t anticipate a court docket order as a result of it pertains to an pressing matter of life and dying.

The roster of the now-defunct “Infinity Recursion” hacking workforce, from which some member of LAPSUS$ hail.
Sources say Jubair additionally used the nickname “Operator,” and that till lately he was the administrator of the Doxbin, a long-running and extremely poisonous on-line neighborhood that’s used to “dox” or publish deeply private data on individuals. In Might 2024, a number of widespread cybercrime channels on Telegram ridiculed Operator after it was revealed that he’d staged his personal kidnapping in a botched plan to throw off regulation enforcement investigators.
In November 2024, U.S. authorities charged 5 males aged 20 to 25 in reference to the Scattered Spider group, which has lengthy relied on recruiting minors to hold out its most dangerous actions. Certainly, lots of the group’s core members have been recruited from on-line gaming platforms like Roblox and Minecraft of their early teenagers, and have been perfecting their social engineering ways for years.
“There’s a clear sample that among the most wicked menace actors first joined cybercrime gangs at an exceptionally younger age,” mentioned Allison Nixon, chief analysis officer on the New York based mostly safety agency Unit 221B. “Cybercriminals arrested at 15 or youthful want severe intervention and monitoring to stop a years lengthy huge escalation.”

