Let me begin by very merely explaining the issue we’re making an attempt to resolve with passkeys. Think about you are logging on to a web site like this:
And, since you need to defend your account from being logged into by another person who could acquire your username and password, you have turned on two-factor authentication (2FA). That implies that even after coming into the right credentials within the display screen above, you are now prompted to enter the six-digit code out of your authenticator app:
There are a couple of totally different authenticator apps on the market, however what all of them have in widespread is that they show a one-time password (henceforth known as an OTP) with a countdown timer subsequent to it:
By solely being legitimate for a brief time period, if another person obtains the OTP then they’ve a very brief window through which it is legitimate. Apart from, who can presumably acquire it out of your authenticator app anyway?! Effectively… that is the place the issue lies, and I demonstrated this only recently, not deliberately, however moderately solely by chance when I fell sufferer to a phishing assault. This is the way it labored:
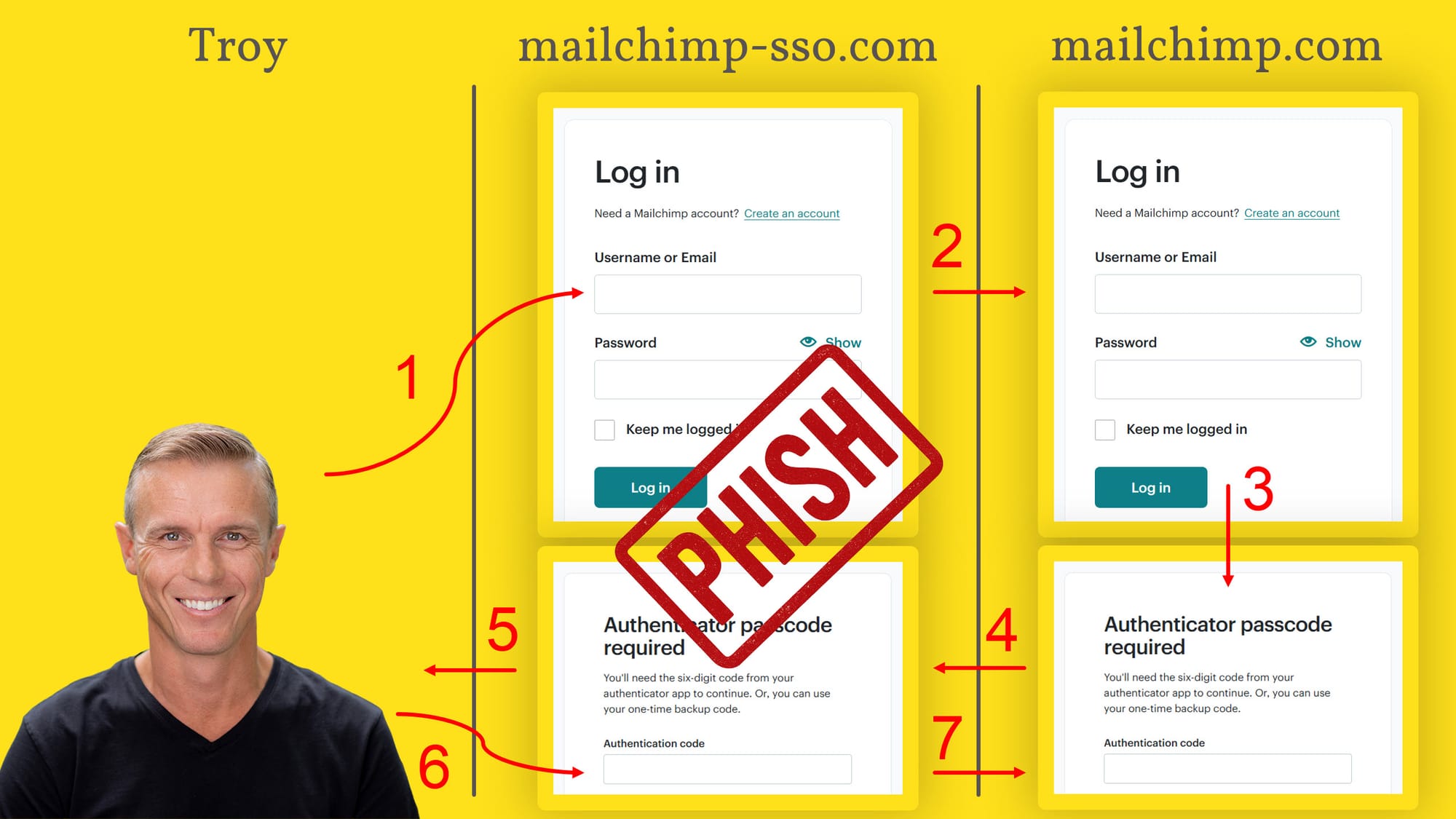
- I used to be socially engineered into visiting a phishing web page that pretended to belong to Mailchimp who I take advantage of to ship newsletters for this weblog. The web site tackle was mailchimp-sso.com, which was shut sufficient to the actual tackle (mailchimp.com) to be possible. “SSO” is “single signal on”, so additionally appeared possible.
- After I noticed the login display screen (the one with the massive “PHISH” stamp on it), and submitted my username and password to them, the phishing website then mechanically used these credentials to start the login course of on Mailchimp.
- Mailchimp validated the credentials, and since I had 2FA turned on, then displayed the OTP request display screen.
- The professional OTP display screen from Mailchimp was then returned to the unhealthy guys…
- …who responded to my login request with their very own web page requesting the OTP.
- I entered the code into the shape and submitted it to the phishing website.
- The unhealthy guys then instantly despatched that request to Mailchimp, thus efficiently logging themselves in.
The issue with OTPs from authenticator apps (or despatched through SMS) is that they are phishable in that it is attainable for somebody to trick you into handing one over. What we want as a substitute is a “phishing-resistant” paradigm, and that is exactly what passkeys are. Let’s take a look at how you can set them up, how you can use them on web sites and in cellular apps, and discuss what a few of their shortcomings are.
Passkeys for Log In on Cell with WhatsApp
We’ll begin by setting one up for WhatsApp given I received a pleasant immediate from them to do that lately:
So, let’s “Attempt it” and stroll by way of the mechanics of what it means to setup a passkey. I am utilizing an iPhone, and that is the display screen I am first offered with:
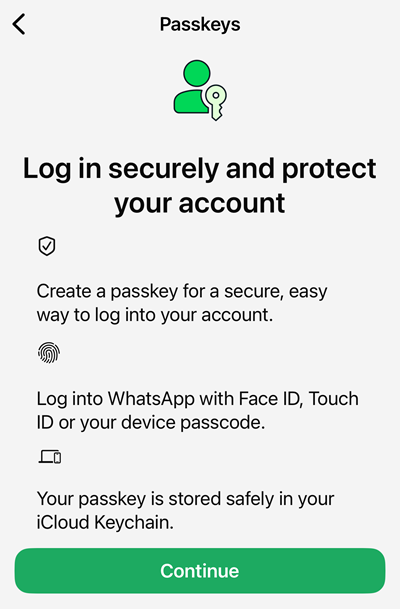
A passkey is just a digital file you retailer in your gadget. It has varied cryptographic protections in the best way it’s created after which used to login, however that goes past the scope of what I need to clarify to the viewers on this weblog put up. Let’s contact briefly on the three gadgets WhatsApp describes above:
- The passkey shall be used to logon to the service
- It really works along with the way you already authenticate to your gadget
- It must be saved someplace (keep in mind, it is a digital file)
That final level will be very device-specific and really user-specific. As a result of I’ve an iPhone, WhatsApp is suggesting I save the passkey into my iCloud Keychain. When you’ve got an Android, you are clearly going to see a unique message that aligns to how Google syncs passkeys. Selecting one in every of these native choices is your path of least resistance – a few clicks and also you’re accomplished. Nevertheless…
I’ve plenty of different providers I need to use passkeys on, and I need to authenticate to them each from my iPhone and my Home windows PC. For instance, I take advantage of LinkedIn throughout all my units, so I do not need my passkey tied solely to my iPhone. (It’s kind of clunky, however some providers allow this through the use of the cellular gadget your passkey is on to scan a QR code displayed on an internet web page). And what if sooner or later I swap from iPhone to Android? I might like my passkeys to be extra transferable, so I will retailer them in my devoted password supervisor, 1Password.
A fast aspect notice: as you will learn on this put up, passkeys don’t essentially exchange passwords. Generally they can be utilized as a “single issue” (the one factor you utilize to login with), however they could even be used as a “second issue” with the primary being your password. That is as much as the service implementing them, and one of many criticisms of passkeys is that your expertise with them will differ between web sites.
We nonetheless want passwords, we nonetheless need them to be sturdy and distinctive, subsequently we nonetheless want password managers. I have been utilizing 1Password for 14 years now (full disclosure: they sponsor Have I Been Pwned, and infrequently sponsor this weblog too) and in addition to storing passwords (and bank cards and passport information and safe notes and sharing all of it with my household), they will additionally retailer passkeys. I’ve 1Password put in on my iPhone and set as the default app to autofill passwords and passkeys:
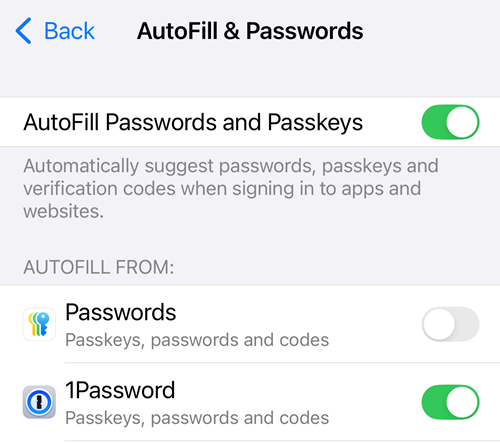
Due to this, I am given the choice to retailer my WhatsApp passkey straight there:
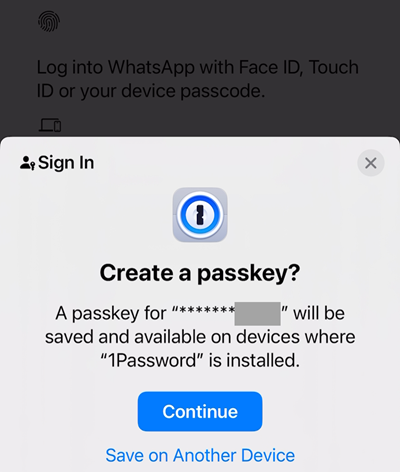
The obfuscated part is the final 4 digits of my telephone quantity. Let’s “Proceed”, after which 1Password pops up with a “Save” button:
As soon as saved, WhatsApp shows the passkey that’s now saved towards my account:
And since I saved it into 1Password that syncs throughout all my units, I can soar over to the PC and see it there too.

And that is it, I now have a passkey for WhatsApp which can be utilized to log in. I picked this instance as a place to begin given the large breadth of the platform and the very fact I used to be actually simply prompted to create a passkey (the very day my Mailchimp account was phished, paradoxically). Solely factor is, I genuinely cannot see how you can log off of WhatsApp so I can then check utilizing the passkey to login. Let’s go and create one other with a unique service and see how that have differs.
Passkeys For Log In through PC with LinkedIn
Let’s choose one other instance, and we’ll set this one up on my PC. I will choose a service that incorporates some vital private data, which might be damaging if it had been taken over. On this case, the service has additionally beforehand suffered an information breach themselves: LinkedIn.
I already had two-step verification enabled on LinkedIn, however as evidenced in my very own phishing expertise, this is not all the time sufficient. (Word: the phrases “two-step”, “two-factor” and “multi-factor” do have delicate variations, however for the sake of simplicity, I will deal with them as interchangeable phrases on this put up.)
Onto passkeys, and you may see similarities between LinkedIn’s and WhatsApp’s descriptions. An vital distinction, nonetheless, is LinkedIn’s remark about not needing to recollect complicated passwords:
Let’s soar into it and create that passkey, however simply earlier than we do, needless to say it is as much as each totally different service to resolve how they implement the workflow for creating passkeys. Identical to how totally different providers have totally different guidelines for password energy standards, the identical applies to the mechanics of passkey creation. LinkedIn begins by requiring my password once more:
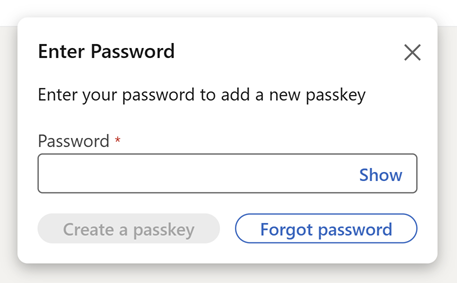
That is a part of the verification course of to make sure somebody apart from you (for instance, somebody who can sit down at your machine that is already logged into LinkedIn), cannot add a brand new approach of accessing your account. I am then prompted for a 6-digit code:
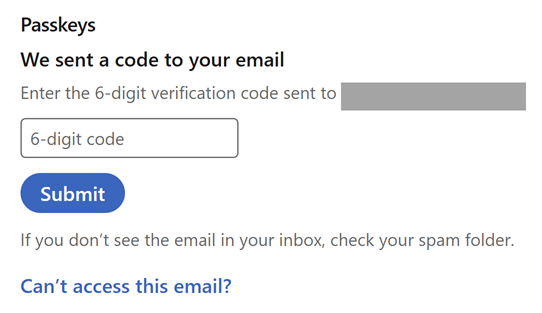
Which has already been despatched to my e-mail tackle, thus verifying I’m certainly the professional account holder:
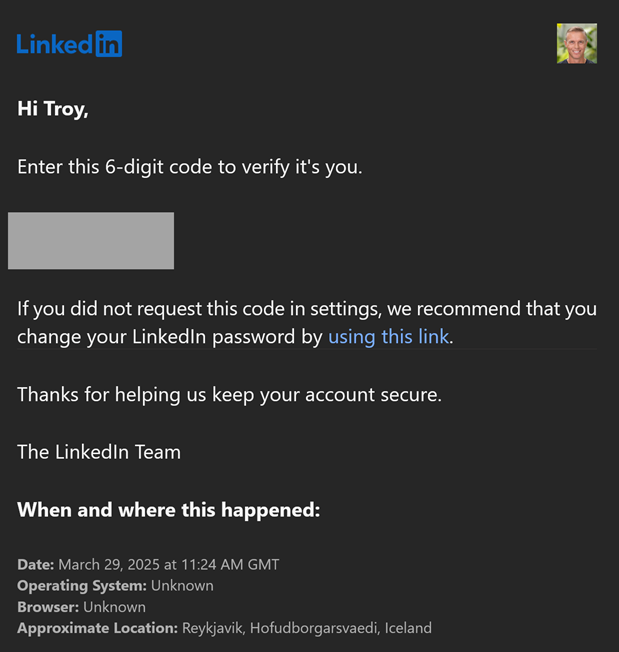
As quickly as I enter that code within the web site, LinkedIn pushes the passkey to me, which 1Password then affords to avoid wasting:
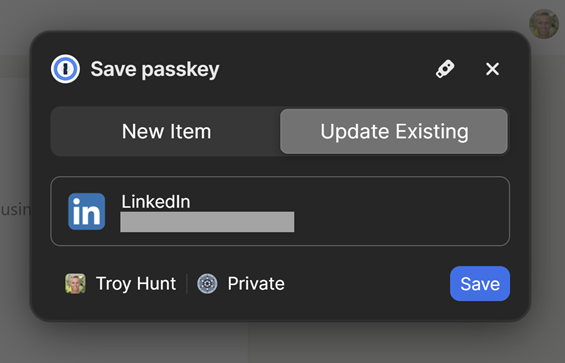
Once more, your expertise will differ based mostly on which gadget and most well-liked methodology of storing passkeys you are utilizing. However what’s going to all the time be the identical for LinkedIn is you can then see the efficiently created passkey on the web site:
Now, let’s have a look at the way it works by logging out of LinkedIn after which returning to the login web page. Instantly, 1Password pops up and affords to signal me in with my passkey:
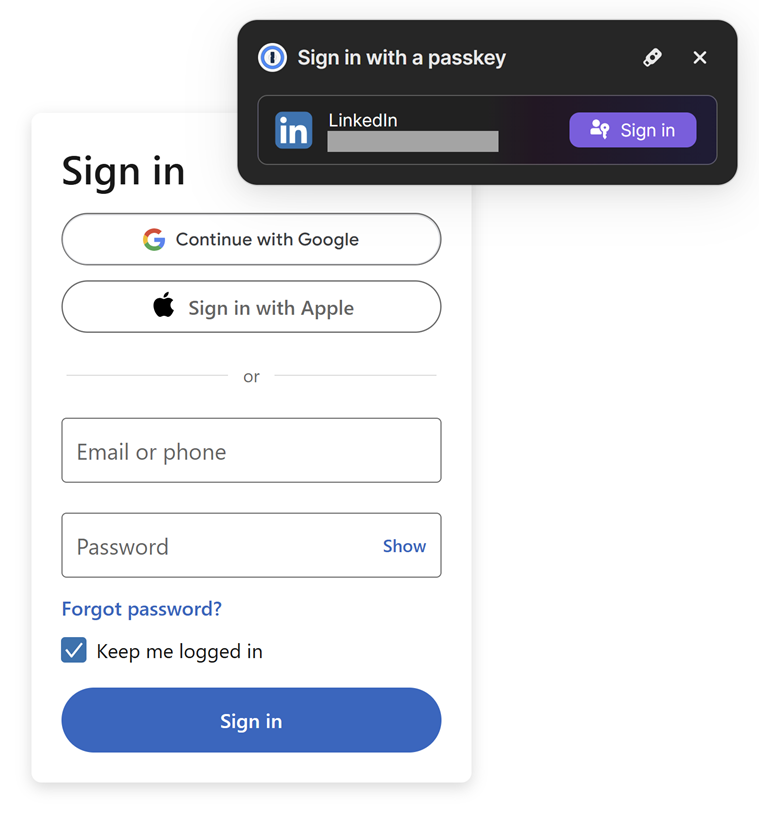
That is a one-click sign-in, and clicking the purple button instantly grants me entry to my account. Not solely will 1Password not let me enter the passkey right into a phishing website, as a result of technical implementation of the keys, it could be fully unusable even when it was submitted to a nefarious celebration. Let me emphasise one thing actually vital about this course of:
Passkeys are one of many few safety constructs that make your life simpler, moderately than tougher.
Nevertheless, there’s an issue: I nonetheless have a password on the account, and I can nonetheless log in with it. What this implies is that LinkedIn has determined (and, once more, that is a kind of website-specific selections), {that a} passkey merely represents a parallel technique of logging in. It would not exchange the password, nor can or not it’s used as a second issue. Even after producing the passkey, solely two choices can be found for that second issue:
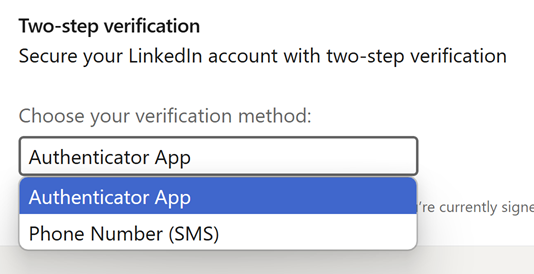
The chance right here is you can nonetheless be tricked into coming into your password right into a phishing website, and per my Mailchimp instance, your second issue (the OTP generated by your authenticator app) can then even be phished. This isn’t to say you should not use a passkey on LinkedIn, however while you continue to have a password and phishable 2FA, you are still susceptible to the identical kind of assault that received me.
Passkeys for 2FA with Ubiquiti
Let’s strive yet one more instance, and this time, it is one which implements passkeys as a real second issue: Ubiquiti.
Ubiquiti is my favorite producer of networking tools, and logging onto their system provides you an huge quantity of visibility into my residence community. When initially establishing that account a few years in the past, I enabled 2FA with an OTP and, as you now perceive, ran the danger of it being phished. However simply the opposite day I observed passkey help and some minutes later, my Ubiquiti account in 1Password appeared like this:
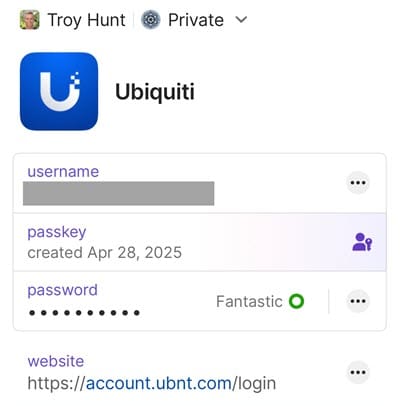
I will not trouble working by way of the setup course of once more as a result of it is largely much like WhatsApp and LinkedIn, however I’ll share simply what it appears wish to now login to that account, and it is superior:
I deliberately left this working at real-time velocity to indicate how briskly the login course of is with a password supervisor and passkey (I’ve blanked out some fields with private information in them). That is about seven seconds from once I first interacted with the display screen to once I was absolutely logged in with a powerful password and second issue. Let me break that course of down step-by-step:
- After I click on on the “E mail or Username” subject, 1Password suggests the account to be logged in with.
- I click on on the account I need to use and 1Password validates my identification with Face ID.
- 1Password mechanically fills in my credentials and submits the shape.
- Ubiquiti asks for my passkey, I click on “Proceed” and my iPhone makes use of Face ID once more to make sure it is actually me.
- The passkey is submitted to Ubiquiti and I am efficiently logged in. (Because it was my first login through Chrome on my iPhone, Ubiquiti then asks if I need to belief the gadget, however that occurs after I am already efficiently logged in.)
Now, keep in mind “the LinkedIn drawback” the place you had been nonetheless caught with phishable 2FA? Not so with Ubiquiti, who allowed me to fully delete the authenticator app:
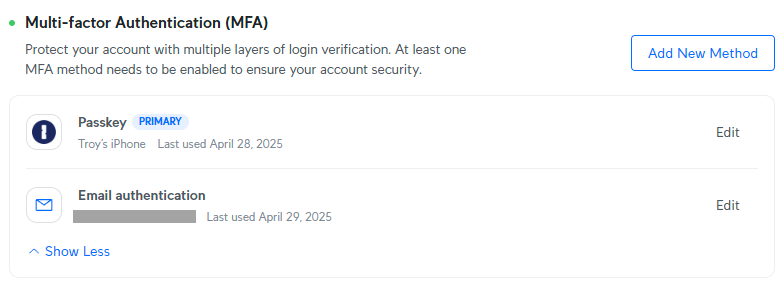
However there’s yet one more factor we will do right here to strengthen every thing up additional, and that is to eliminate e-mail authentication and exchange it with one thing even stronger than a passkey: a U2F key.
Bodily Common 2 Issue Key for 2FA with Ubiquiti
While passkeys themselves are thought-about non-phishable, what occurs if the place you retailer that digital key will get compromised? Your iCloud Keychain, for instance, or your 1Password account. If you happen to configure and handle these providers correctly then the probability of that occuring is extraordinarily distant, however the chance stays. Let’s add one thing solely totally different now, and that is a bodily safety key:

This can be a YubiKey and you’ll you’ll be able to retailer your digital passkey on it. It must be bought and as of in the present day, that is a couple of US$60 funding for a single key. YubiKeys are referred to as “Common 2 Issue” or U2F keys and the one above (that is a 5C NFC) can both plug into a tool with USB-C or be held subsequent to a telephone with NFC (that is “close to subject communication”, a short-range wi-fi know-how that requires units to be a couple of centimetres aside). YubiKeys aren’t the one makers of U2F keys, however their identify has change into synonymous with the know-how.
Again to Ubiquiti, and once I try to take away e-mail authentication, the next immediate stops me useless in my tracks:
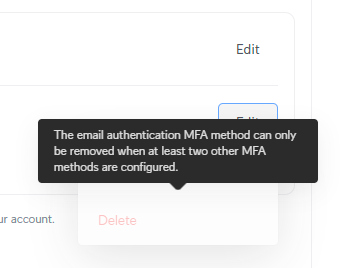
I do not need e-mail authentication as a result of that includes sending a code to my e-mail tackle and, nicely, everyone knows what occurs once we’re counting on folks to enter codes into login varieties 🤔 So, let’s now stroll by way of the Ubiquiti course of and add one other passkey as a second issue:
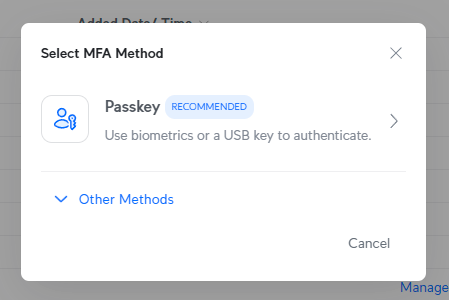
However this time, when Chrome pops up and affords to reserve it in 1Password, I am going to decide on the little USB icon on the prime of the immediate as a substitute:
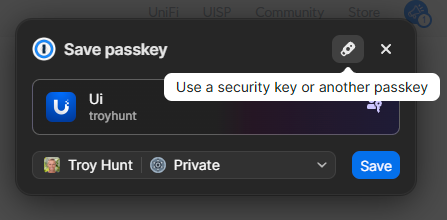
Home windows then provides me a immediate to decide on the place I want to save the passkey, which is the place I select the safety key I’ve already inserted into my PC:
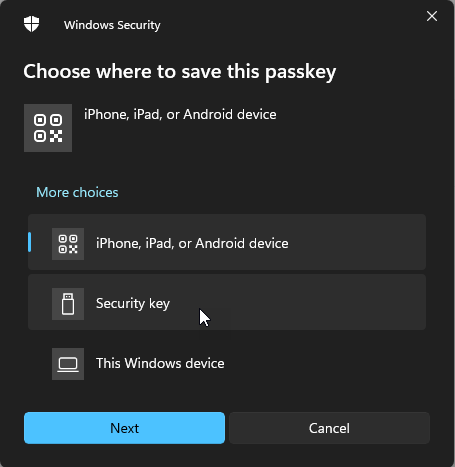
Every time you start interacting with a U2F key, it requires slightly faucet:
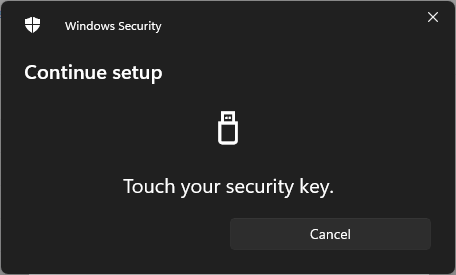
And a second later, my digital passkey has been saved to my bodily U2F key:
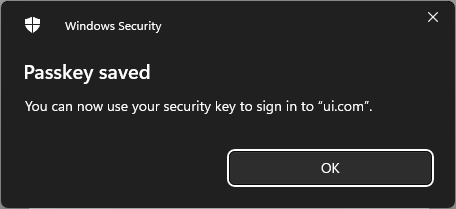
Simply as it can save you your passkey to Apple’s iCloud Keychain or in 1Password and sync it throughout your units, you can too put it aside to a bodily key. And that is exactly what I’ve now accomplished – saved one Ubiquiti passkey to 1Password and one to my YubiKey. Which implies I can now go and take away e-mail authentication, nevertheless it does carry a danger:
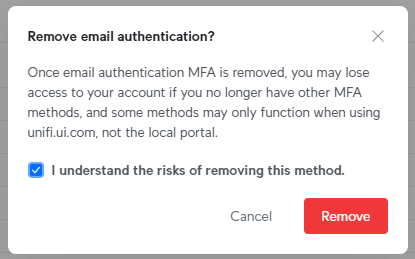
This can be a good level to replicate on the paradox that securing your digital life presents: as we search stronger types of authentication, we create totally different dangers. Shedding all of your types of non-phishable 2FA, for instance, creates the danger of shedding entry to your account. However we even have mitigating controls: your digital passkey is managed completely independently of your bodily one so the possibilities of shedding each are extraordinarily low. Plus, greatest apply is normally to have two U2F keys and enrol them each (I all the time take one with me once I journey, and go away one other one at residence). New ranges of safety, new dangers, new mitigations.
Discovering Websites That Assist Passkeys
All that is nice, however past my examples above, who really helps passkeys?! A quickly increasing variety of providers, lots of which 1Password has documented of their glorious passkeys.listing web site:
Take a look by way of the record there, and you may see many very acquainted manufacturers. You will not see Ubiquiti as of the time of writing, however I’ve gone by way of the “Recommend new itemizing” course of to have them added and shall be chatting additional with the 1Password of us to see how we will extra quickly populate that record.
Do additionally check out the “Vote for passkeys help” tab and should you see a model that actually needs to be there, make your voice heard. Hey, this is a great one to begin voting for:
Abstract
I’ve intentionally simply centered on the mechanics of passkeys on this weblog put up, however let me take only a second to focus on vital separate however associated ideas. Consider passkeys as one a part of what we name “defence in depth”, that’s the utility of a number of controls to assist hold you protected on-line. For instance, it is best to nonetheless deal with emails containing hyperlinks with a wholesome suspicion and each time unsure, not click on something and independently navigate to the web site in query through your browser. You need to nonetheless have sturdy, distinctive passwords and use a password supervisor to retailer them. And it is best to most likely additionally be sure to’re absolutely awake and never jet lagged in mattress earlier than manually coming into your credentials into a web site your password supervisor did not autofill for you 🙂
We’re not on the very starting of passkeys, and we’re additionally not but fairly at the tipping level both… nevertheless it’s within reach. Simply final week, Microsoft introduced that new accounts shall be passwordless by default, with a choice to utilizing passkeys. While passkeys are certainly not excellent, have a look at what they’re changing! Begin utilizing them now in your most important providers and push people who do not help them to genuinely take the safety of their prospects critically.


