It is arduous to discover a good prison nowadays. I imply a very reliable one you might be assured will not lead you up the backyard path with false guarantees of information breaches. Like this man yesterday:
For my worldwide pals, JB Hello-Fi is a large electronics retailer down below they usually have my knowledge! I imply by design as a result of I’ve purchased a bunch of stuff from them, so I used to be curious not nearly my very own knowledge however as a result of a breach of 12 million plus individuals can be huge in a rustic of not way more than double that. So, I dropped the man a message and requested if he’d be keen to assist me confirm the incident by sharing my very own document. I did not wish to publish any public commentary about this incident till I had an inexpensive diploma of confidence it was legit, not given how a lot impression it may have in my very personal yard.
Now, I would not usually share a personal dialog with one other get together, however when somebody units out to rip-off individuals, that rule goes out the window so far as I am involved. So here is the place the dialog acquired fascinating:
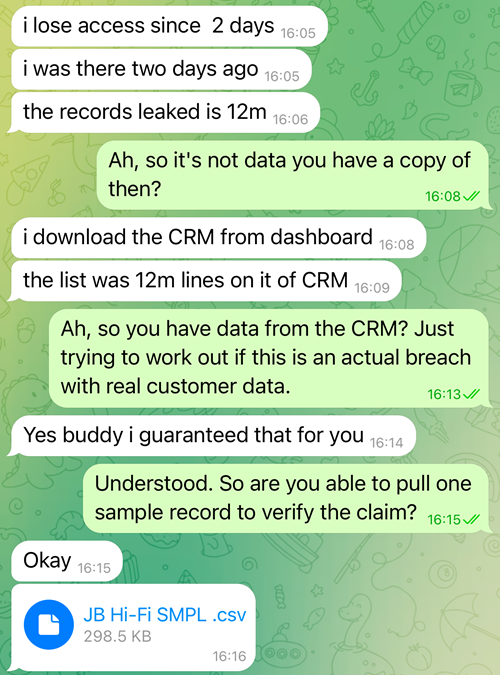
He assured it for me! Sounds legit. However hey, everybody will get the good thing about the doubt till confirmed in any other case, so I began wanting on the knowledge. It seems my very own information wasn’t within the full set, however he was comfortable to supply a number of thousand pattern data with 14 columns:
- customer_id_
- first_name
- last_name
- FullName
- gender
- email_address_
- mobile_country_
- mobile_number_
- dob
- postal_street_1_
- state_
- postal_code_
- city_
- account_status
Fairly commonplace stuff, might be legit, let’s examine. I’ve slightly Powershell script I run towards the HIBP API when a brand new alleged breach is available in and I wish to get a very good sense of how distinctive it’s. It merely loops by all the e-mail addresses in a file, checks which breaches they have been in and retains observe of the proportion which have been seen earlier than. A singular breach could have anyplace from about 40% to 80% beforehand seen addresses, however this one had, nicely, extra:
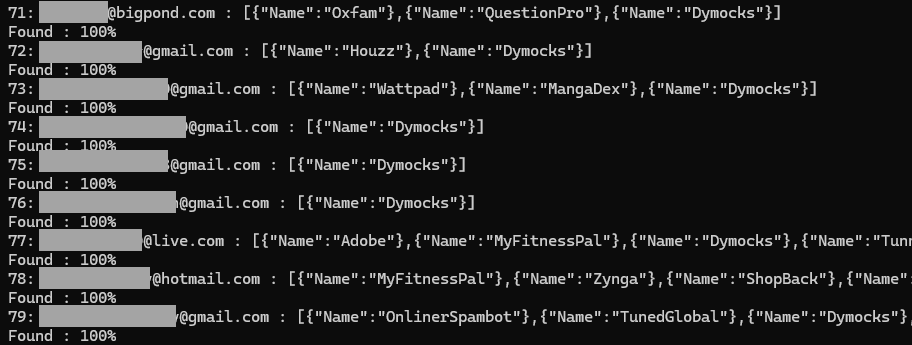
Spot the development? Each single tackle has one breach in widespread. Hmmm… marvel what the man has to say about that?
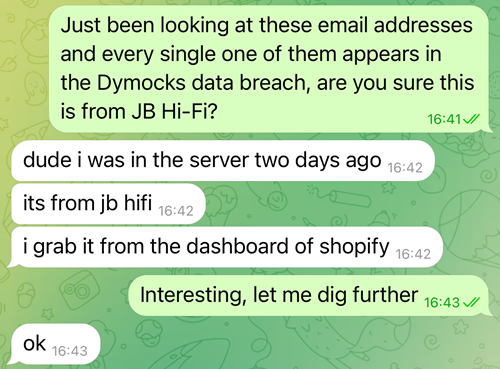
However he was within the server! And he grabbed it from the dashboard of Shopify! Have to be legit, except… what if I in contrast it to the precise full breach of Dymocks? That is an area Aussie bookseller (so it might have a number of Aussie-looking electronic mail addresses in it, identical to JB Hello-Fi would), and their breach dated again to mid-2023. I preserve breaches like that readily available for simply such events, let’s evaluate the 2:
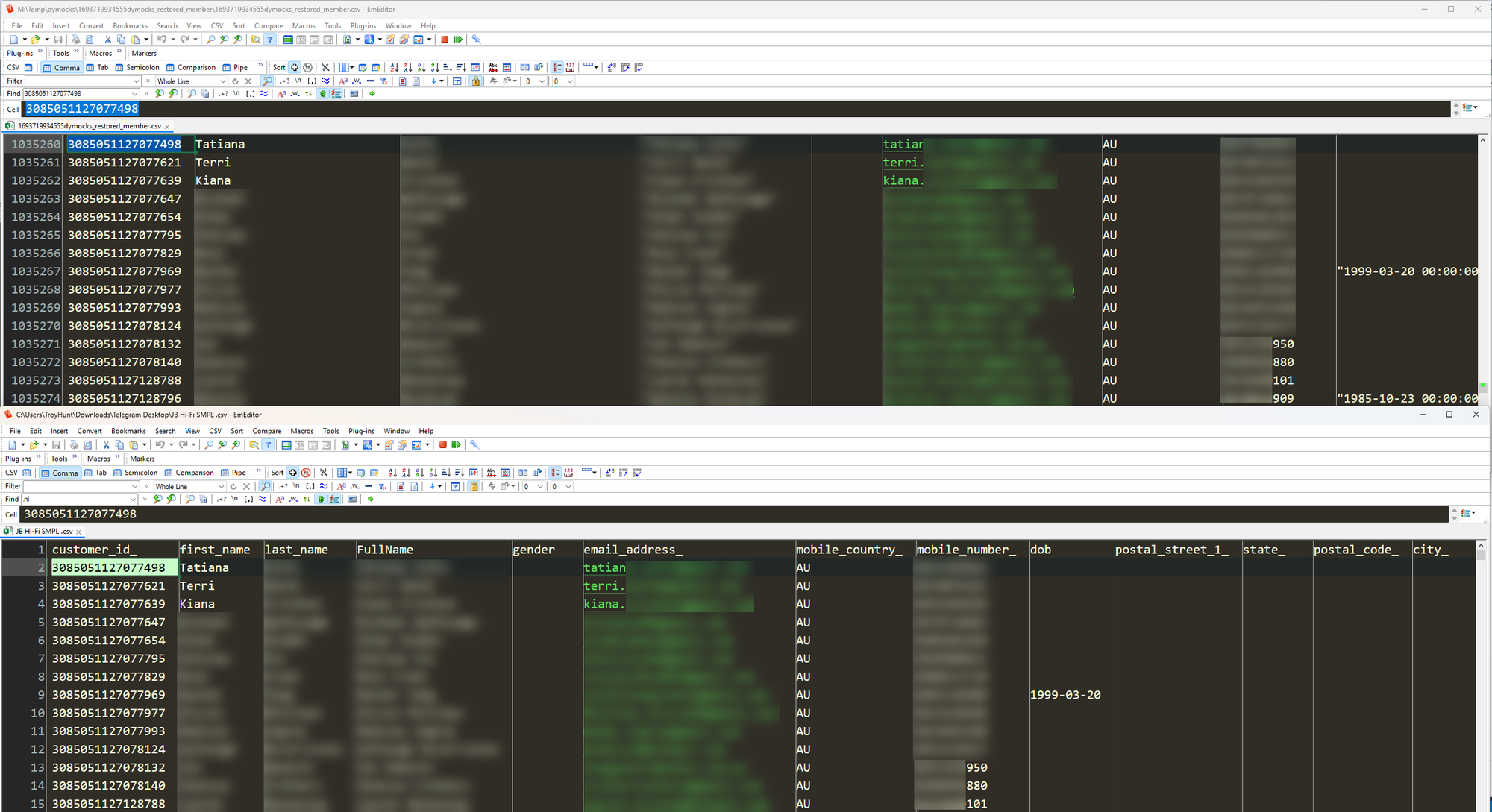
Wow! What are the probabilities?! He will be so when he hears about this!
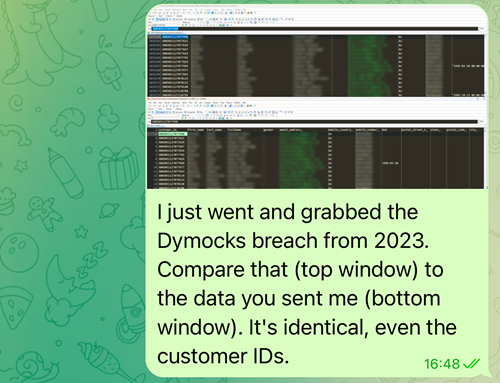
And that was it. The chat went silent and really shortly after, the itemizing was gone:
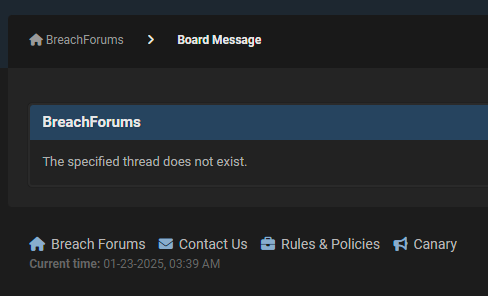
It appears to be like just like the bloke has additionally since been booted off the discussion board the place he tried to run the rip-off so yeah, this one did not work out nice for him. That $16k would have been so tasty too!
I wrote this quick publish to focus on how vital verification of information breach claims is. Clearly, I’ve seen hundreds of reliable ones however I’ve additionally seen a number of garbage. Not normally this blatant the place the get together contacting me is making such demonstrably false claims about their very own exploits, however very frequently from individuals who get hold of one thing from one other get together and repeat the lie they have been advised. This instance additionally highlights how helpful knowledge from earlier breaches is, even after the e-mail addresses have been extracted and loaded into HIBP. Knowledge is so typically recycled and shipped round as one thing new, this was only a textbook excellent case of constructing use of a earlier incident to disprove a brand new declare. Plus, it is kinda enjoyable poking holes in a scamming prison’s claims 😊



